Microsoft’s “Patch Tuesday “Includes Four New Exchange Server Fixes
- Microsoft has squashed 114 critical and important bugs this month.
- There are four fixes for flaws concerning the Exchange Server product.
- The set also contains fixes for zero-day flaws that have been under exploitation since February.
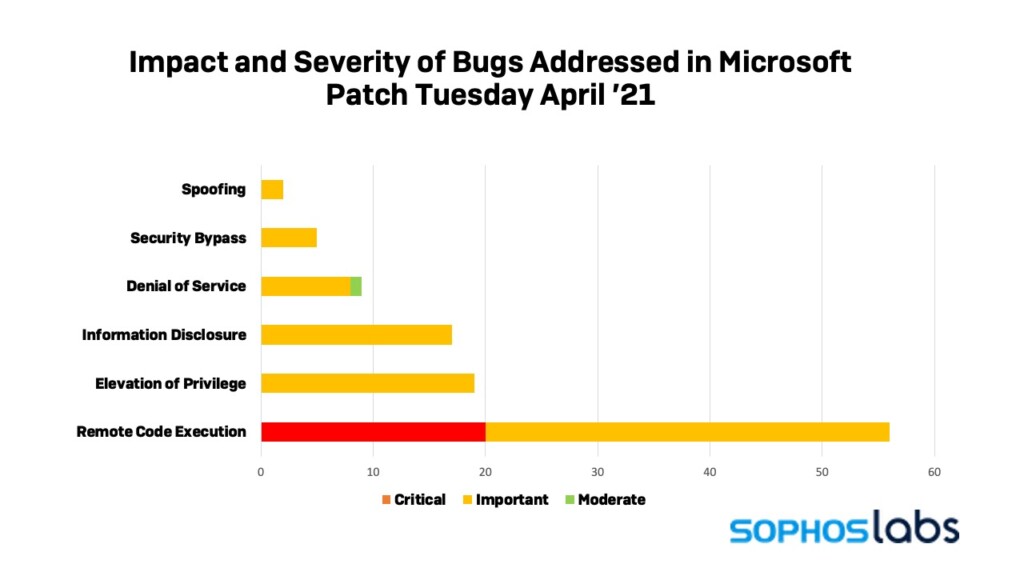
Microsoft has released this month’s patch for a range of its software products, bringing a large set of 114 fixes for critical and important vulnerabilities. Among the latest fixes, we see four new Exchange server flaws, which come on top of those that shook the infosec world last month. These are identified as CVE-2021-28480, CVE-2021-28481, CVE-2021-28482, and CVE-2021-28483, and they are all of critical severity.
All four were reported by the NSA, although Microsoft found two internally. These two flaws don’t even require the attacker to authenticate to the vulnerable Exchange Server in order to exploit it, and according to Microsoft, they are “more likely to be exploited.” As such, applying the patch as soon as possible is critical, as it’s the case every month with Microsoft’s security patches.
From the rest of the fixes, we have 12 critical RCE vulnerabilities that exist in the remote procedure call runtime, and all of which require no user interaction at all. A worrying example of these is CVE-2021-27095 and also CVE-2021-28315, two flaws in the Windows Media Video Decoder that don’t require special privileges to exploit and are of low complexity.
Another important fix is the one addressing CVE-2021-28310, an elevation of privilege flaw in the Win32k process. Kaspersky researchers discovered threat actors using this zero-day in the wild back in February, possibly chained with other vulnerabilities, resulting in a “sandbox escape” situation where the attackers were able to break free from browser protections.
And as for the most popular bugs for crooks, these were CVE-2021-28319 and CVE-2021-28439, two denial of service flaws, and also CVE-2021-28442, an information disclosure bug. All these are on the Windows TCP/IP driver and can be triggered remotely to cause BSOD.
For a full list of all flaws fixed by Microsoft’s engineers this month, check out the Security Update Guide. As always, make sure to backup your important files and data before you apply the update, as something could go wrong with the process, and you could end up with a corrupted filesystem. This is never a reason to postpone applying security patches, though, so make sure to perform the update as soon as practically possible.