Key TakeawaysGotaTun security audit findings: Independent review found no major vulnerabilities in GotaTun v0.2.0 during January–February 2026 security assessment.Low-severity issues identified: Audit highlighted predictable session…
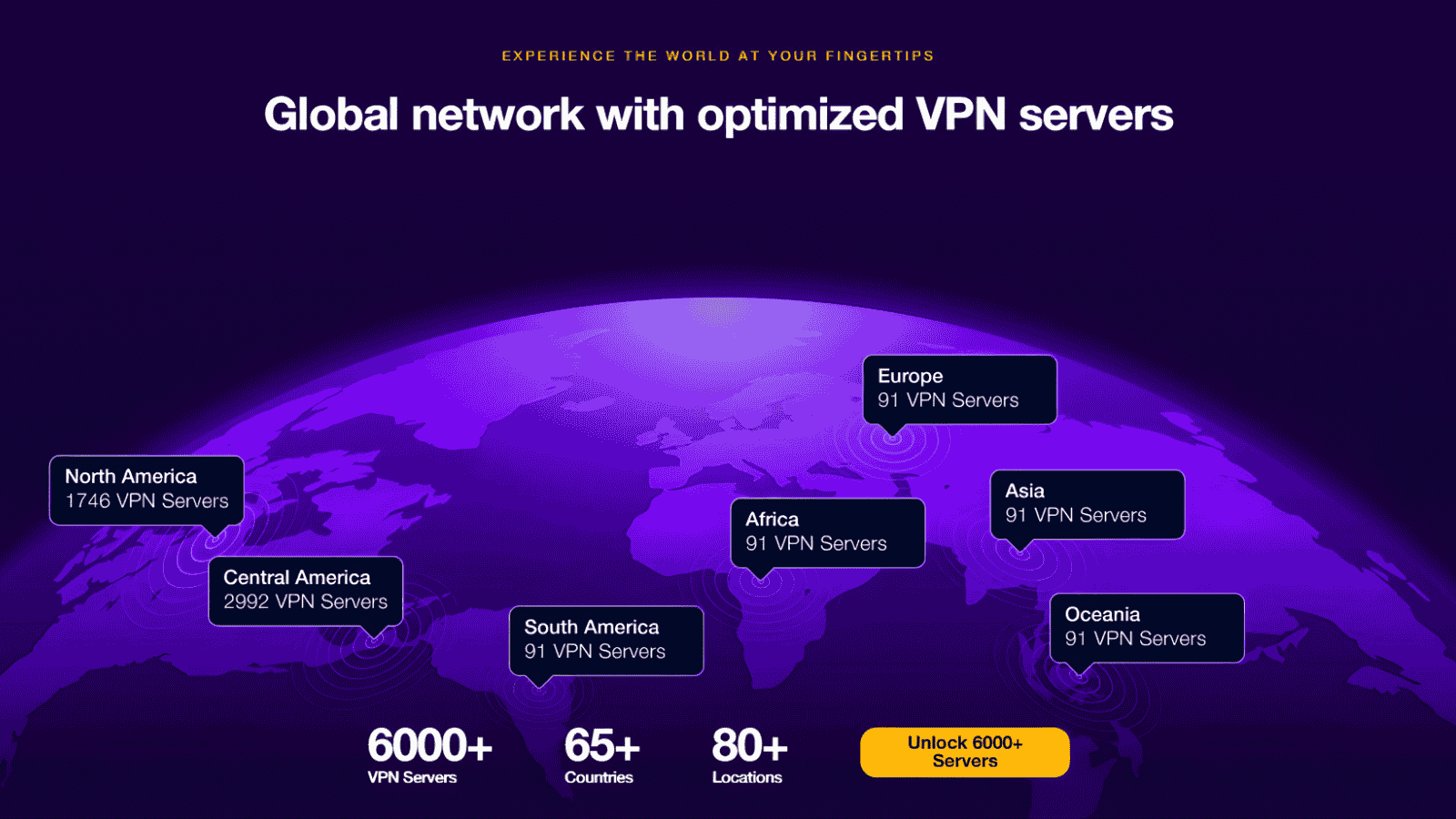
QUICK ANSWERPureVPN Network Expansion: Added 40+ global servers improving speed, stability, and regional connectivity for all users.Improved Latency and Stability: Shorter routing paths and distributed…

Key TakeawaysOfficial Inquiry: The UK's Information Commissioner's Office (ICO) is formally contacting Meta regarding significant data privacy concerns linked to its AI-powered smart glasses.Intimate Data…

Key TakeawaysCoordinated Campaign: Almost 150 hacktivist-led Distributed Denial-of-Service attacks have targeted 110 distinct organizations across 16 countries.Critical Sector Focus: Twelve threat groups primarily focused on…

Key TakeawaysPlatform Disruption: International law enforcement successfully executed a coordinated global cybercrime operation to completely shut down LeakBase, a massive illicit data repository.User Deanonymization: Authorities…

Key TakeawaysMassive Scale: The open-source CyberStrikeAI framework orchestrated over 600 unauthorized network intrusions spanning 55 countries.Targeted Infrastructure: Threat actors specifically compromised FortiGate appliances utilizing 21…

Key TakeawaysSurveillance Compromise: Suspected Iran-nexus threat actors are actively exploiting exposed network cameras, possibly for real-time assessments of battle damage.Targeted Hardware: The campaign targets known…
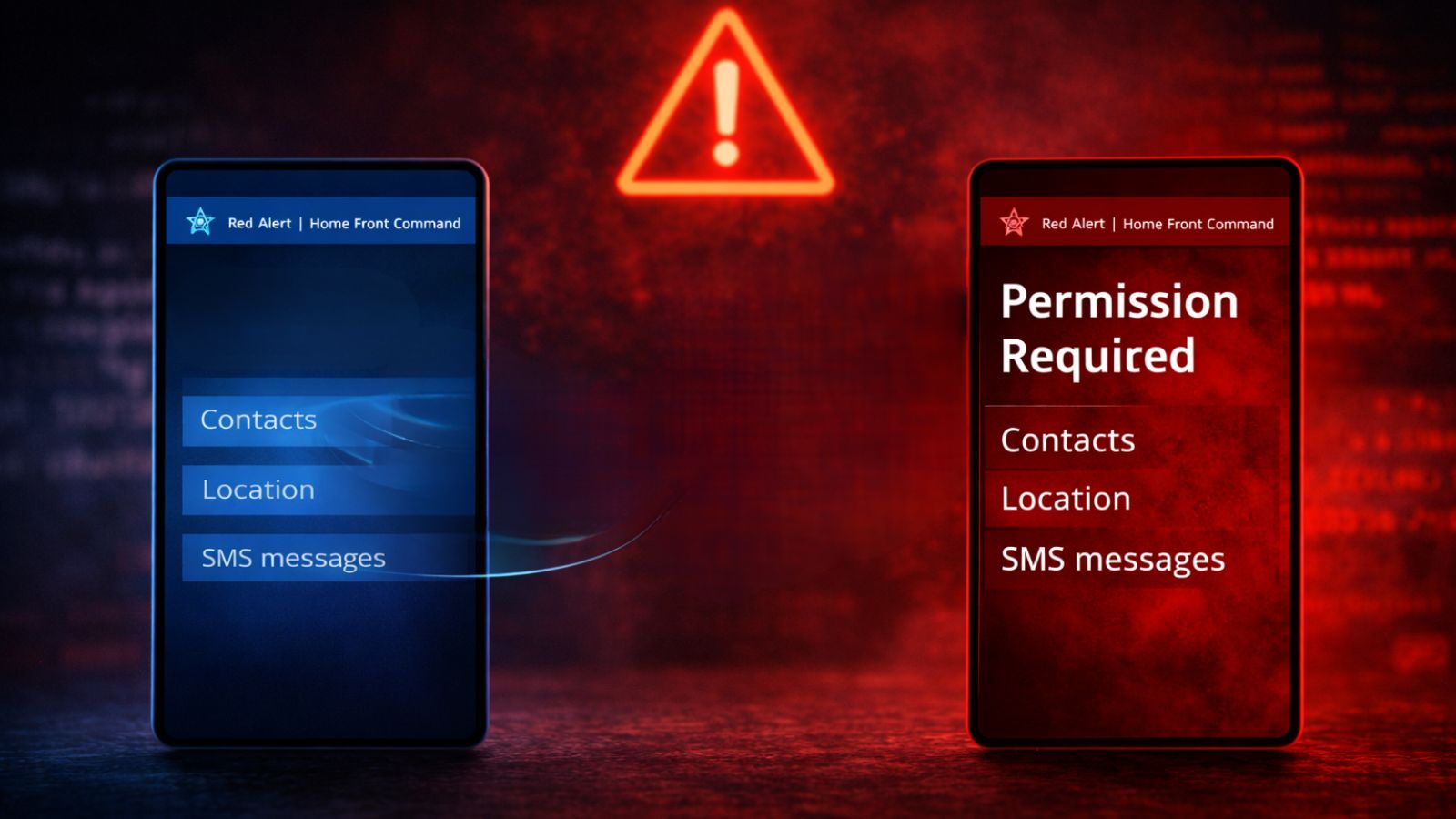
Key TakeawaysSMS Trojan: Threat actors are executing a RedAlert Trojan campaign using targeted SMS phishing to distribute a malicious Android application.Impersonation: The fake emergency alert…

Key TakeawaysExploit Proliferation: A sophisticated suite of hacking tools designed to compromise iPhones has been leaked and is now actively used by cybercriminals.Broad Impact: The…

Key TakeawaysExploited Authorization Flows: Threat actors are manipulating OAuth redirect URIs to route authenticated users to malicious infrastructure undetected.Sophisticated Payloads: The campaign deploys embedded ZIP…

Key TakeawaysNetwork Disruption: The Denmark School District experienced a prolonged internet outage stemming from an alleged internal vulnerability.Operational Impact: The lack of connectivity forced educators…

Key TakeawaysDigital Strikes: Critical Iranian communication and sensor frameworks were disabled in a coordinated operation by the U.S. Cyber Command.Tactical Foundation: These non-kinetic cyber actions…

Key TakeawaysPrison Sentence: A Bavarian court sentenced the central figure of the Milton Group scam network to more than 7 years in prison for financial…

Key TakeawaysRegulatory Deadline: Starting March 9, AI services in Australia must restrict access to harmful content for users under 18 or pay millions in penalties.Gatekeeper…

Key TakeawaysAI-Powered Breach: Threat actors leveraged Anthropic's Claude Code and OpenAI's GPT-4.1 to execute a multi-stage attack against Mexican government entities.Massive Data Exfiltration: The breach…

Key TakeawaysCompromised Application: The 'BadeSaba' prayer app was hacked to broadcast "surrender" notifications to millions of Iranians during airstrikes.Psychological Operations: Messages promised amnesty to military…

Key TakeawaysOperational Failure: The National Tax Service inadvertently published a seed phrase in press materials, compromising a seized wallet.Asset Theft: Unauthorized actors exploited the leak…

Nick Andersen – CISA The Cybersecurity and Infrastructure Security Agency (CISA) has named Nick Andersen as Interim Director following the departure of Madhu Gottumukkala from…

Arrests, indictments, and convictions maintained continued pressure on ransomware, fraud networks, and insider threats, with criminal activity moving laterally across airlines, energy, healthcare, and education…