Microsoft’s Patch Tuesday for March 2021 Carries 14 Critical Fixes
- Microsoft has released this month’s security updates for all its products, and they bring 89 fixes.
- The tech firm has included the previously released critical Exchange server fixes in the patch pack.
- Most of the fixed flaws are remote code execution and privilege escalation issues.
It has been a tough month for Microsoft and its clients, as the Exchange flaws that were patched recently proved to be a lot more widely exploited than what was initially thought. The time for the monthly patching has arrived in the middle of urgent pleads for Exchange patching, so there’s quite a significant amount of stress for system administrators to deal with right now. Still, applying the monthly fixes remains critical, and Microsoft is giving everyone 14 important reasons for it.
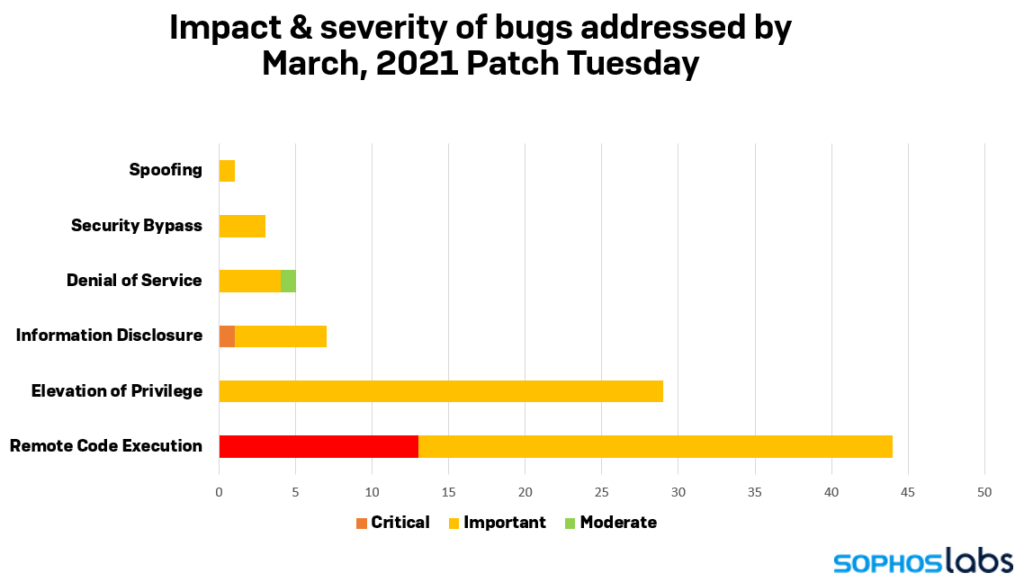
In total, the March 2021 patch addresses 89 vulnerabilities, with 14 of them being classified as critical. The vast majority of the fixes concern RCE flaws, while the elevation of privilege issues also have a significant portion.
Starting with the Exchange fixes, we have the addressing of CVE-2021-26412, CVE-26854, CVE-26855, CVE-26857, CVE-26858, CVE-27065, and CVE-27078, which affect Exchange server 2013, 2016, and 2019. These were already pushed earlier this month as an out-of-band patch due to its criticality, but the fixes have been incorporated into the Tuesday pack too.
Next, we have two serious RCE flaws in Internet Explorer, CVE-2021-26411 and CVE-2021-27085. Microsoft claims to have spotted the exploitation of these flaws in the wild, so addressing them was urgent. This makes us wonder who could still be using Internet Explorer in this day, but since there is active exploitation, there are users.
Then, there are several RCEs and denial of service bugs in the DNS server (versions 2008 through 2019), like CVE-2021-26877, CVE-26893, CVE-26894, CVE-26895, CVE-26896, and CVE-27063. These open the door to code execution and also make the server unavailable to its users, so attackers could combine exploits to achieve more catastrophic results.
And finally, we have several privilege escalation bug fixes in win32k (CVE-2021-26863, CVE-26875, CVE-26900, CVE-27077) and one in DirectX (CVE-2021-24095). The first of these fixes got a very detailed write-up by the MAPP team, as it is an interesting race condition creator in the win32k driver, leading to dangerous situations.
As always, you are advised to backup your data before you proceed with the updating, as errors in the process or a power outage may easily render your filesystem corrupted. Also, this is the last patch to fix problems on the legacy Edge, so starting by next month, only the Chromium-based Edge will be supported. If you haven’t made the leap yet, you need to do it now.