Microsoft’s First ‘Patch Tuesday’ of the Year Brings Fix for Defender Zero-Day
- Microsoft has released the first patch of the year, and it’s a comprehensive set of fixes.
- One noteworthy flaw is an actively exploited bug in Defender, which triggers an RCE scan.
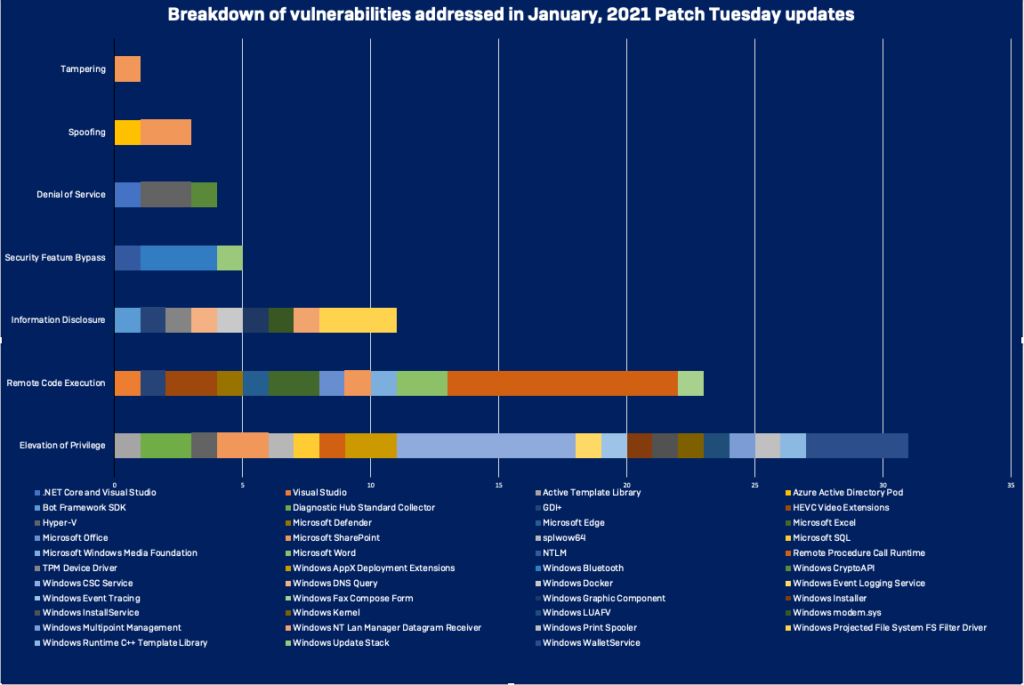
- Most of the addressed vulnerabilities are elevation of privilege, RCE, and information disclosure bugs.
The first ‘Patch Tuesday’ to kick-off 2021 has Microsoft fixing 83 vulnerabilities across its various products, with one being an actively exploited zero-day in Windows Defender (CVE-2021-1647). It is to be found on all Windows installations out there as it’s the default AV/AM tool of the OS.
The particular bug enables attackers to engage in remote code execution because of an error in handling the parsing of information structures in certain executables. One would have to craft a special file that would trigger a Windows Defender scan to exploit it.
One thing to clarify is that if the user has manually disabled the Defender or has installed a third-party AV product that automatically disables Microsoft’s tool, then the attack would not work. That said, if applying the patch right now is impossible, a temporary mitigation would be to deactivate Defender.
A second vulnerability that may be under active exploitation but not definitely is 'CVE-2021-1709'. This is a bug in the Win32k component, which could enable an attacker to gain escalation of privilege on the target system through memory corruption. This bug presupposed local access to the target system, so it’s not as critical.
Other notable important flaws that were fixed with the latest patch are the following:
- CVE-2021-1707: SharePoint service flaw allowing access to a site and remote code execution within the kernel.
- CVE-2021-1677: Identity spoofing vulnerability in Azure Active Directory Pod.
- CVE-2021-1705: Memory corruption vulnerability in the HTML-based version of Microsoft Edge.
- CVE-2021-1648: Elevation of privilege vulnerability in splwow64.
- CVE-2021-1643: Code execution vulnerability in HEVC video files.
- CVE-2021-1660: Remote procedure call runtime remote code execution flaw that is particularly easy to reproduce.
Of course, there are many more flaws, and their importance is not always reflected by the individual CVVS scores, as people use different components, configurations, and tools. Thus, the best way to stay safe and protected against hacking risks would be to just apply the patch and address everything.
As always, be sure to backup your data before applying the update, as things can always go wrong in the patching process. Even if you blindly trust Windows testers, a power outage during the update (which would lead to a corrupted filesystem) is always a possibility, so don’t risk it.