Microsoft’s February Patch Tuesday Fixes Easy to Exploit DoS Flaws
- Microsoft has released this month’s patch for Windows and other products, addressing 56 flaws.
- The firm focuses on fixing three RCEs affecting TCP/IP, one of which is easy to exploit.
- There’s a workaround for those who can’t apply the patch, but it’s not perfect or without downsides.
Microsoft has released this month’s security patch for a wide range of products, and the fixes include two critical RCE (remote code execution) flaws (CVE-2021-24074, CVE-2021-24094) and an important DoS (denial of service) bug (CVE-2021-24086). According to Microsoft, the first two are quite complicated, so it wouldn’t be easy for hackers to develop a functional exploit based on them.
The DoS vulnerability, though, would be fairly trivial to exploit, so the news about it is very likely to spark a wave of attacks. Thus, there’s an urgent recommendation to apply this patch as soon as possible.
The particular flaw is an IPv6 bug that unravels during the reassembly of a fragmented packet. The attacker would have to use a large volume of extension headers in the fragmented packets sent to the target, creating a NULL pointer dereference situation which crashes the Windows kernel and ends up in a “blue screen of death.” It is possible that the bug is exploitable through both LAN networks and over the internet, but this hasn’t been clarified.
For those who can’t apply the patch, a workaround would be to disable the function of packet reassembly. This would drop any out-of-order packets, potentially causing packet losses, so it’s not a perfect solution. Those willing to try it and see how it works for them can use the following command:
“Netsh int ipv6 set global reassemblylimit=0”
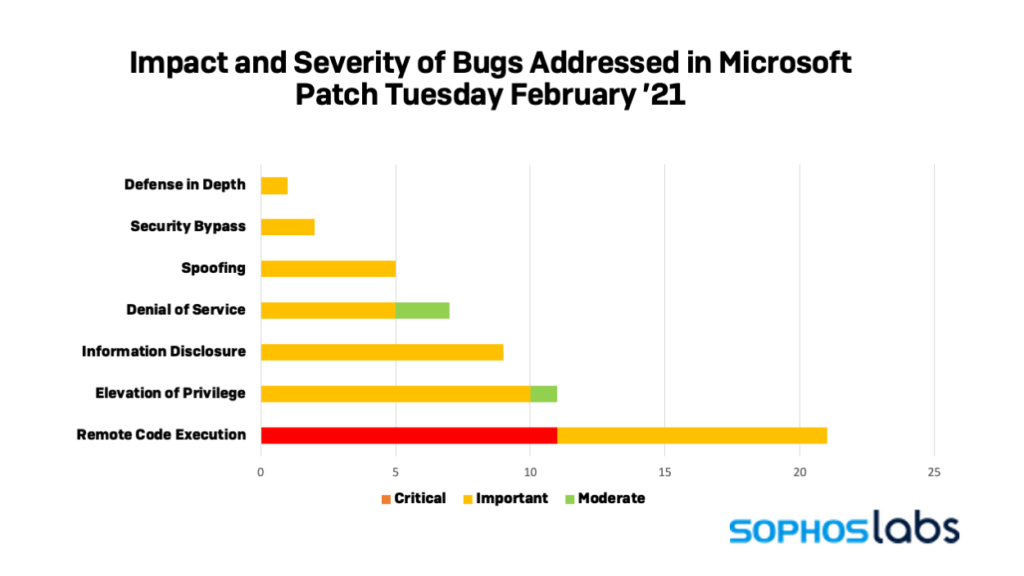
In total, this month’s patch is fixing 56 vulnerabilities, 11 of which are rated as “critical,” three as “moderate,” and the rest as “important.”
Other noteworthy squashed bugs include:
- CVE-2021-1732 – Privilege escalation in Win32k
- CVE-2021-26701 – Windows and Visual Studio SDK
- CVE-2021-24072 – Interaction-less flaw in SharePoint
- CVE-2021-24093 – Windows Graphics Component
- CVE-2021-24088 + 24091 – RCE on Windows codes (image and video)
Once again, the majority of the fixes concern RCEs, with the elevation of privilege, information disclosure, and denial of service following in that order.
As always, before you proceed to apply the patch, make sure to backup your valuable data to secure them from unfortunate events like a power outage during the update process, for example. Fixing security flaws shouldn’t come at the risk of your data, and ending up with a system that won’t boot is always a possibility you should keep in mind.