Magento Killer Infects eCommerce Platforms and Steals Payment Info
- Magento Killer is the new three-step script menace for Magento platforms around the globe.
- The PHP script changes core settings in the installation, stealing money and client information.
- The actors take things further by trying to steal the PII data of the compromised customers.
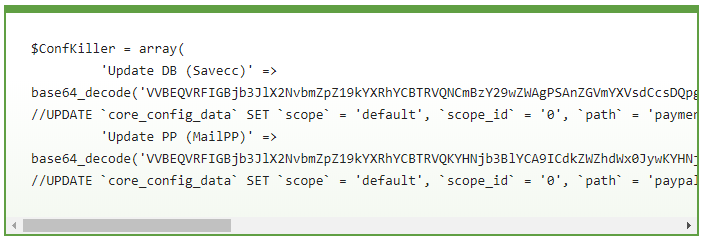
Sucuri researcher Luke Leak warns of a malicious PHP script named “Magento Killer” that infects Magento installations and enables the malicious actor to modify the core of the database. According to the technical report, the attacker uses special SQL queries encoded in base64 to modify the “core_config_data” table of the target database, and use two objects, namely the Update DB and the Update PP. The first one configures the Magento website to save the entered credit card information of the clients onto the server, and the second one changes the PayPal merchant business account to one that belongs to the hacker.
image source: blog.sucuri.net
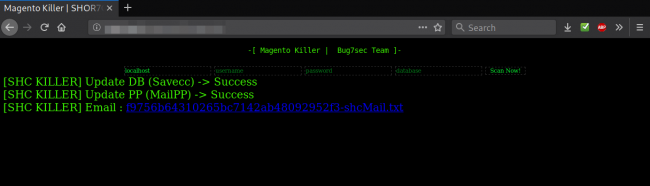
This means that the attacker removes the connection of the website to the payment processor who would otherwise have data protection measures in place, and steals the credit card details from customers of the compromised shops. The attacker isn’t leaving the website payments untouched either, as changing the merchant’s account means that the money of the transactions ends up in their PayPal account instead. So, this PHP script enables attackers to get the money you paid for goods and services, and then empty your credit card at a later date, or sell this information on the dark web.
image source: blog.sucuri.net
As detailed by the researcher, the attackers prefer to use this information themselves, so they create a variable array in their SQL queries from the injected Magento database, stealing the full names of the victims, their email addresses, their physical address, and any other billing information that would make emptying their banks accounts possible or easier. The array listing has been optimized to trim the data down to the absolutely required information and generates a text file that contains the customer information for the attacker to retrieve it later on.
Magento is a very popular eCommerce platform used by many thousands of websites out there, and that is why crooks are trying to build tools that make their exploitation more automated. In this case, we have a PHP script that may cause significant damage before the administrator realizes that something dreadful is going on on their platforms. If you want to check whether your Magento installation has been compromised, check out Sucuri’s guide which will also help you with advice on how to clean it.
Do you have something to say on the above? Feel free to do so in the comments down below, or on our socials, on Facebook and Twitter.