New Magecart Campaign Compromised More Than 80 eCommerce Sites
- Researchers uncover a new large-scale Magecart campaign which involves eighty websites.
- All of the compromised platforms use older Magento platforms, so they are easy to exploit.
- There’s a sudden rise in this type of attacks, as e-commerce platform owners continue to act irresponsibly.
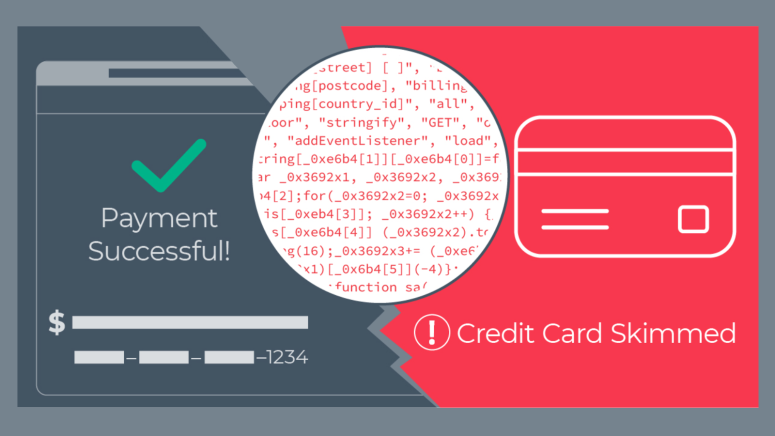
Arxan Technologies has published a report that uncovers a new large-scale Magecart campaign which has spread over 80 e-commerce websites. The administrators of the infected platforms have no idea that malicious actors infected their websites, and how they steal the credit card information of their clients. The Arxan researchers claim that it took them only 2.5 hours to discover this campaign, as the malicious actors have used moderately strong JavaScript code obfuscation and anti-detection methods. The compromised websites deploy older versions of the Magento platform that carry known and published exploits, while 25% of them belong to renown brands who are engaged in high-end motorsports and luxury retail.
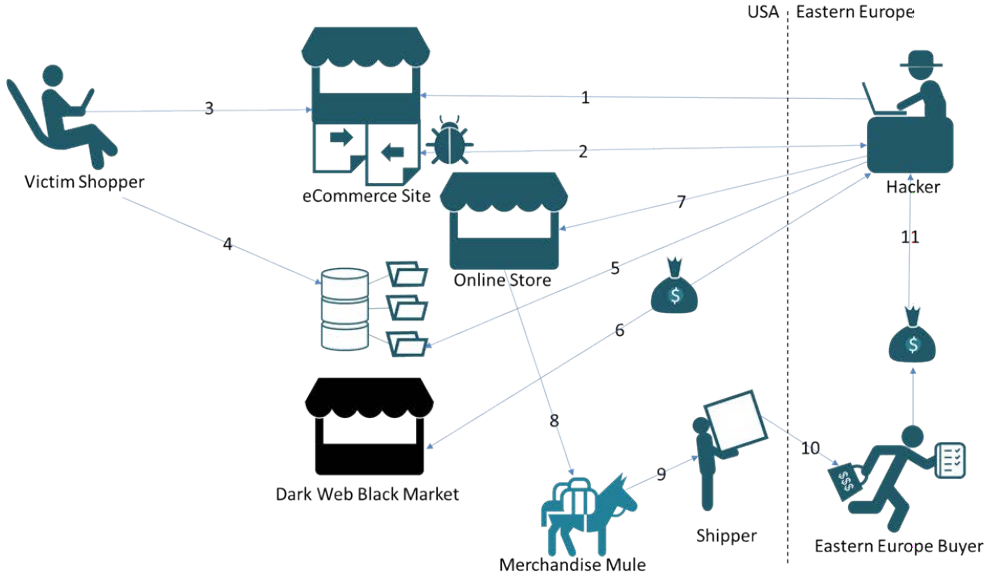
This indicates that the actors are after heavy wallets, so their targeting isn’t random at all. The malicious code is inserted onto the server-side checkout payment form and is incorporated in the e-commerce’s site source code. Unsuspecting customers who enter their payment details like credit card information, CVC codes, names, expiration dates, etc., have this data captured and transferred directly onto the actor’s server. The transactions on the e-commerce website go through as normal, and the platform receives all of the expected transaction reports with nothing else indicating a problem.
Source: info.arxan.com
Having all this data in their hands, the actors can buy stuff from online shops, pass them through merchandise mules, who finally ship them to the buyer’s destination. This form of activity has been growing in popularity lately, as crooks find it relatively safe, reliable, and very profitable. We have repeatedly reported about similar Magecart schemes since the start of the year, with campus stores in North America getting compromised in May, and 277 e-commerce platforms being infected with payment data-stealing code in January. A recent Malwarebytes report claims that in July alone, their products blocked 65000 data theft attempts of this type.
All that said, customers aren’t expected to analyze and de-obfuscate the JavaScript code that lies on the source of the checkout form webpages. The responsibility to secure this sensitive data burdens the e-commerce website administrators, who really can’t have any excuse for not doing the best they can. For starters, updating to the latest available version of the e-commerce platform that you’re using will wipe out all possibilities of falling victim to known and publicly available exploits. To take things further, you could audit your web code now and then implement a security solution that will alert your team when suspicious activities take place on your website.
Do you trust e-commerce platforms with your credit card data, or do you prefer other payment methods? Let us know in the comments section down below, or on our socials, on Facebook and Twitter.