Graboid is The First-Ever Worm to be Found Hiding in Docker Hub Images
- Graboid worm infects Docker hosts and scans the network for further propagation.
- The worm is limited to crypto-mining activities right now, but its capabilities could easily expand in the future.
- Docker admins should prefer SSH connections and Unix socket communication instead of exposing the Docker Engine.
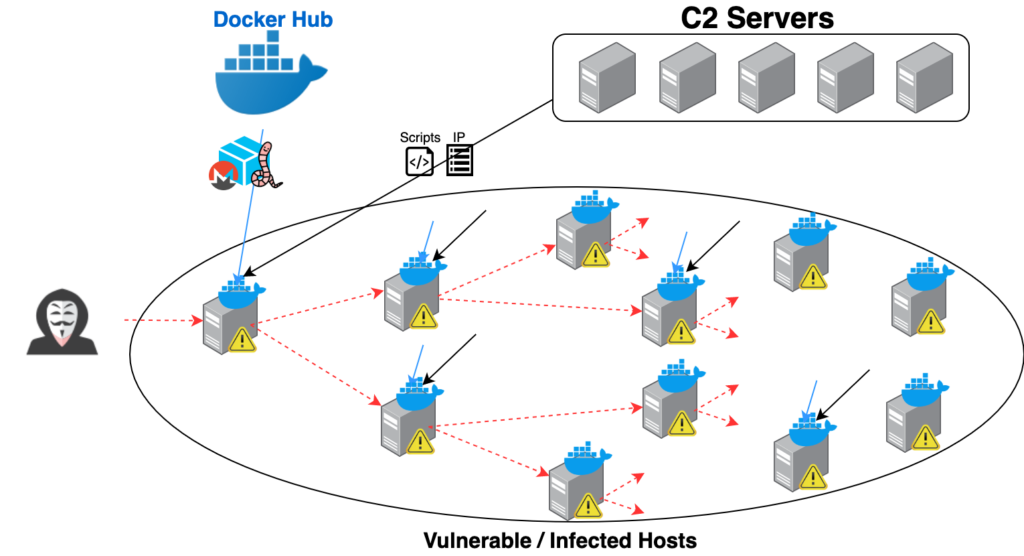
According to a report by Unit 42 researchers who made the discovery, there’s a new cryptojacking worm that has already nested in 2,000 Docker hosts. The worm was named “Graboid”, and spreads through containers of the Docker Engine. As the cryptojacking activity isn’t detectable by most endpoint security tools, the actors are free to continue making money out of the Monero mining that goes on. As the researchers point out, each mining session lasts for 250 seconds and then stops for 90 seconds.
After the initial host infection, the C2 server which controls the worm network periodically queries the target connections to find new vulnerable hosts to spread to. The malicious image (pocsow/centos) that is used for this process contains a docker client tool. After its entry, the container downloads four shell scripts from the C2 and executes them sequentially. These scripts detect the number of available CPUs on the compromised host, download a file that contains a list of 2,000 IPs with the unsecured docker API endpoints, and randomly pick the next target. This process repeats every 100 seconds - until there are no other vulnerable hosts to spread to.
Source: Unit 42 Report
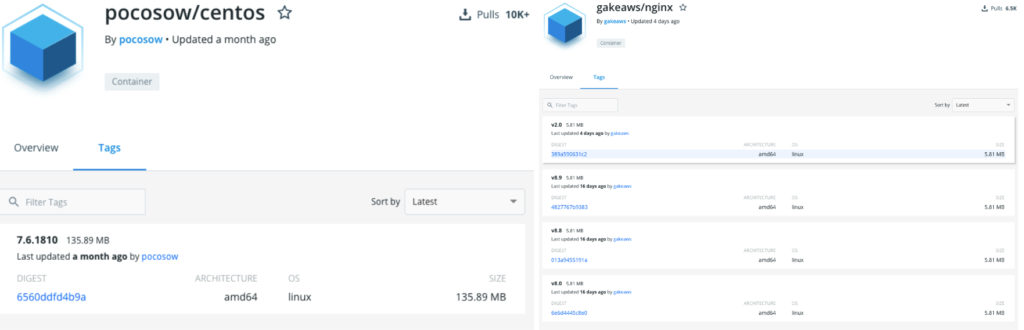
The “pocsow/centos” Docker image has been downloaded more than 10,000 times, while the similar in content “gakeaws/nginx” was downloaded another 6,500 times. Of course, nothing is stopping the actors from uploading new images with different names. Moreover, the C2 may send new scripts to the Graboid worm, rendering it into a powerful malware, ransomware, etc., taking over the hosts completely. While the current operation is just stealing resources, the worm network may easily get a lot more threatening and dangerous at any time.
Source: Unit 42 Report
Thomas Hatch, the co-founder of SaltStack has stated the following about Graboid: “There is a false but prevailing sentiment within the Docker community that the OS is not relevant and that the OS is a commoditized layer. This issue highlights how amazingly wrong this assumption is. When distributing an OS image there are hundreds of binaries that can be manipulated to stealthily hide issues that current security and DevSecOps tools are not going to see.”
James Condon, the Director of Research at Lacework commented: “It is important to scan images pre-deploy, only use images you trust, utilize a runtime solution that has proper container visibility, and implement network security monitoring. All in all, the risk of this threat is predicated on a critical misconfiguration.”
The researchers suggest avoiding the exposure of the docker daemon to the internet without ensuring a robust authentication mechanism. By default, the Docker Engine isn’t exposed, and admins are changing this setting for convenience. Instead, they should use a Unix socket or SSH to connect to the Docker daemon. Finally, set up a firewall and define strict whitelisting to allow only trustworthy traffic.
Have something to comment on the above? Feel free to share your thoughts with us in the section down below, or join the discussion on our socials, on Facebook and Twitter.