There’s a New File-Based Cryptominer Dubbed ‘Beapy’ Hitting Chinese Companies
- A new cryptominer named “Beapy” is targeting Asian corporation while ignoring consumers.
- The particular malware has been upgraded multiple times in the past few months and is now a versatile worm.
- Malicious actors turn back to file-based crypto miners as they are yielding much higher amounts of money.
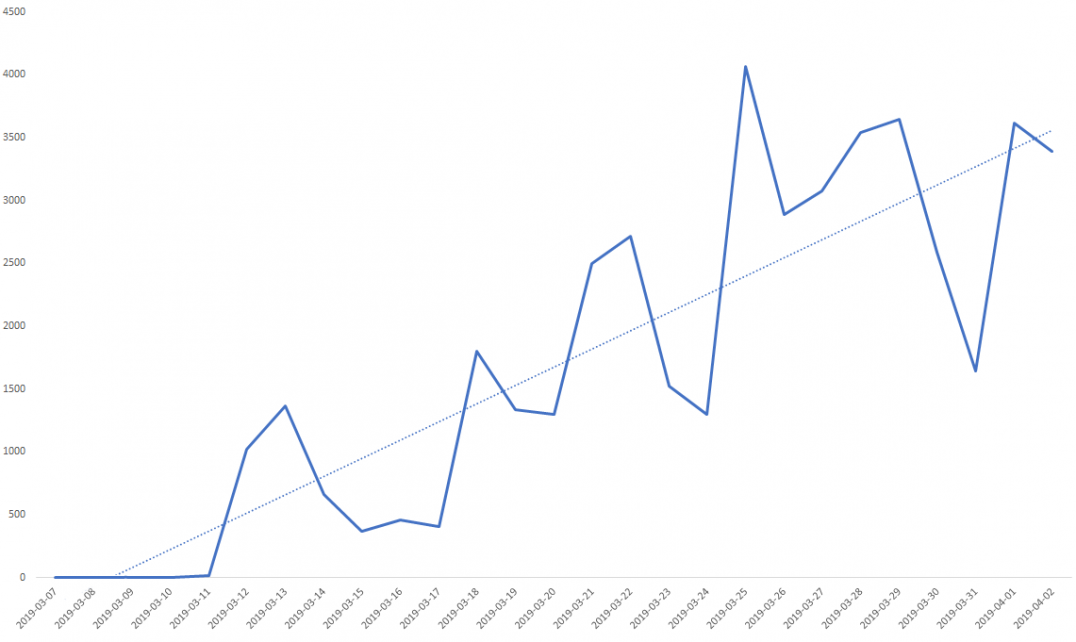
In perfect alignment with what we reported earlier today, cryptojacking campaigns are currently solely targeted on exploiting the resources of enterprise entities and are configured to ignore consumers. The latest example of that comes in the form of “Beapy”, a malware which targets large organizations in Asia. This new threat is written in Python and was developed specifically to use the DoublePulsar backdoor to carry out remote code execution through EternalBlue, which exploits a vulnerability in the Windows SMB (Server Message Block) protocol. According to the latest telemetry data published by Symantec Corporation, 2% of the infections that concern consumers can be attributed to an accidental proceeding, while the remaining 98% is targeting large companies. Out of these, 83% involves China-based targets.
Beapy finds its way inside corporate networks through malicious email messages, usually Excel document attachments that download the DoublePulsar backdoor onto the infected machine. Beapy receives instructions from a malicious C&C server in the form of a series of PowerShell commands which eventually lead to the downloading of a file-based Monero miner. From there, all unpatched machines in the same network are vulnerable to Beapy, as aggressive propagation remains the main focus of the particular malware.
image source: symantec.com
Where EternalBlue fails, Beapy uses a rich set of hardcoded list of usernames and passwords, trying to dig deeper into the infected network. In this process, it also employs the “Hacktool.Mimikatz”, trying to collect any credentials that are possibly present in the machines that have been already compromised. Moreover, Beapy doesn’t rely solely on the SMB vulnerability, as Symantec researchers have also noticed the examined samples trying to exploit known flaws like the Apache Tomcat (CVE-2017-12615) and the Oracle WebLogic Server (CVE-2017-10271). All of this combined gives Beapy worm-like characteristics, and make it a particularly persistent menace that once it finds its way into a corporate network, it can’t be easily stopped.
image source: symantec.com
With Coinhive gone, cryptojacking campaigns seem to follow a new trend that prefers file-based tools instead of browser-based exploitation tools. This is, of course, more complex for the actors, but it comes with a set of advantages for them as well. For example, the average profit per infected machine can be 25 times higher, and so the financial gains for crooks are much higher. Now, what this means from the businesses’ perspective is slower machines, overheating hardware, accelerated degradation and shorter-than-expected system replacement times, higher electricity costs, and higher cloud billing costs for those who deploy/rent cloud resources. All of these are clear signs that something shady is going on, and that the IT department of a company should investigate further.
Care to share your views on the above? Feel free to do so in the comments down below, or on our social media pages, on Facebook and Twitter.