Skidmap is a New Cryptomining Malware For Linux Systems
- Skidmap is a modern example of the sophistication and power of Linux malware samples.
- It features high levels of obfuscation, loads kernel-mode rootkits, and is supported by monitoring components.
- The particular malware is hard to detect, and very hard to remove from infected systems.
Linux is not at all mainstream, and many think of the OS as the safest choice when it comes to malware targeting. While this holds some truth for desktop users, actors still look to leverage the sheer power of server farms and cloud infrastructure that usually run Linux, and what better way to exploit this power than to make it mine cryptocurrency for you? Skidmap is the latest effort on that part, discovered and analyzed by Trend Micro researchers who warn about its extended capabilities and resilience against detection.
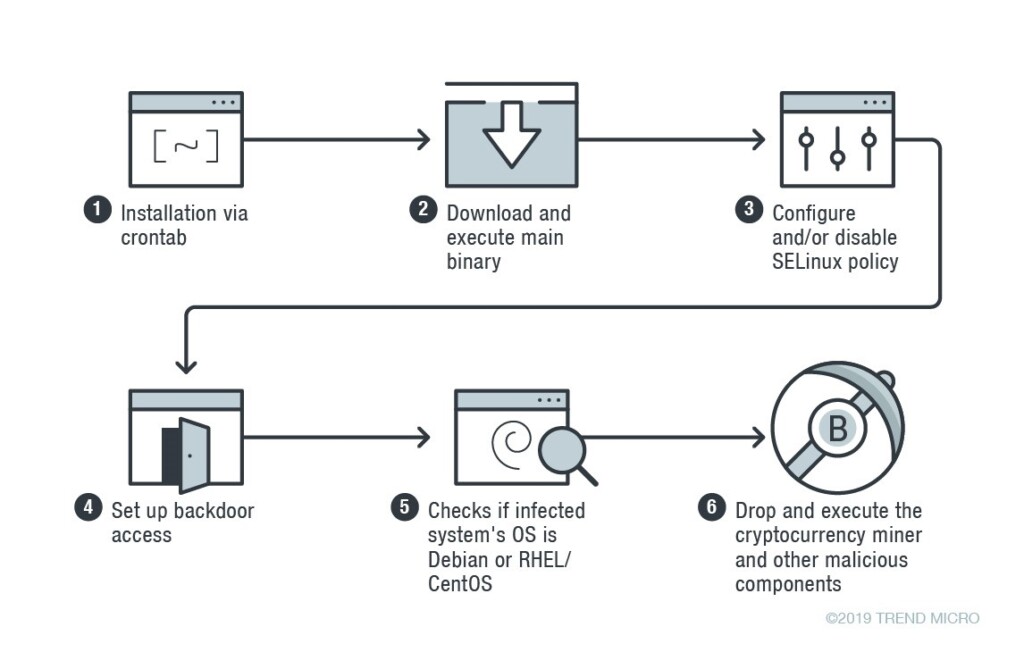
Skidmap loads kernel-mode rootkits so as to stay hidden from the user. This is way different than user-mode rootkits that run with administrative privileges because they can’t be easily detected by protection tools. The infection chain begins with a crontab installation, which is a system that enables users to schedule the execution of commands. The next step is to download and execute Skidmap’s main binary, disable the SELinux module, or at least set it to “setenforce 0” which makes it less strict, and then set up backdoor access. The malware then checks if the infected Linux distribution is based on Debian or Red Hat EL/CentOS, and finally drops the appropriate cryptocurrency miner with the accompanying components.
Source: blog.trendmicro.com
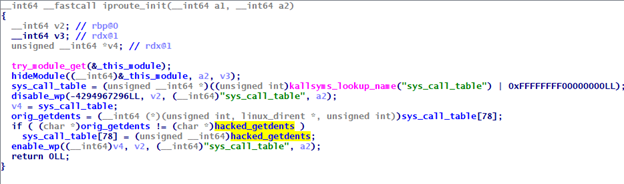
These additional components are mostly tools to help Skidmap hide its activity, or obfuscate it. For example, “kaudited” is a binary that drops and installs several kernel modules that help to prevent system crashes, which is the main drawback of using kernel-mode rootkits. Another example of a malicious component that comes with Skidmap is a fake “rm” binary, which randomly sets up cron jobs and replaces the legitimate “rm” command in the infected system, making it impossible to delete files by using it. Finally, there’s the “iproute” module that hooks “getdents”, which an admin would use in order to look into the contents of a directory.
Source: blog.trendmicro.com
Skidmap can cause great disruption to enterprise environments and it can be especially hard to detect or even to remove. For this reason, system administrators are advised not to trust and enable unsigned repositories, patch their systems to the latest available versions, and use Linux server protection solutions from reliable vendors.
Have something to comment on the above? Let us know of your opinion in the section down below, or kickstart a discussion on our socials, on Facebook and Twitter.