Retadup Worm is Stopped by Avast After Reaching its Zenith at 850k Infections
- The Retadup crypto miner-dropping worm has been stopped after Avast replaced its C&C.
- The security company worked together with the FBI and the French police to stop the worm.
- The authorities know who the actor is, as he has been bragging about Retadup on social media.
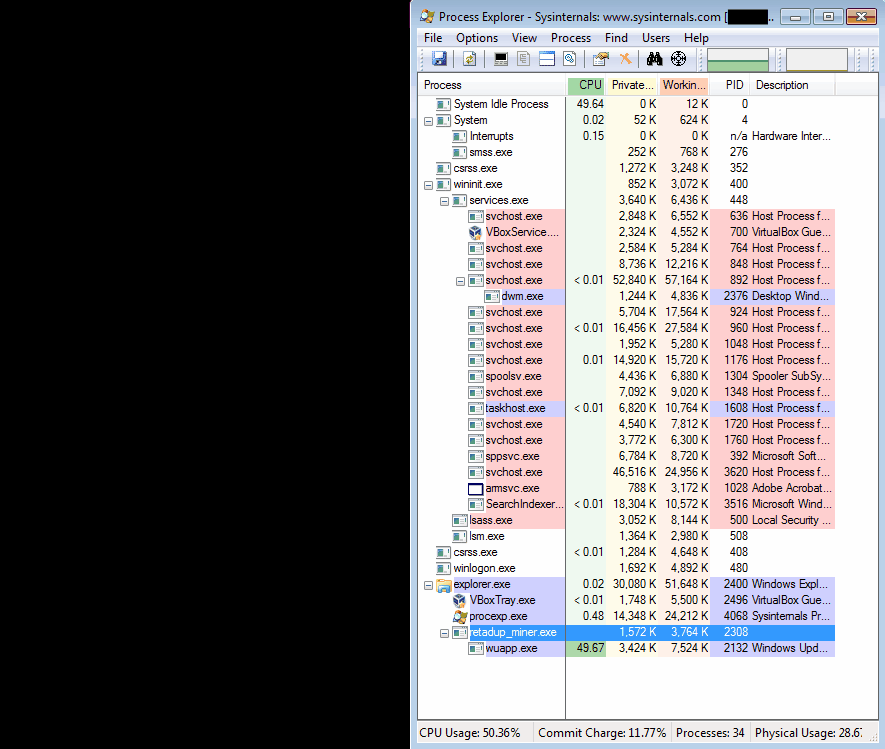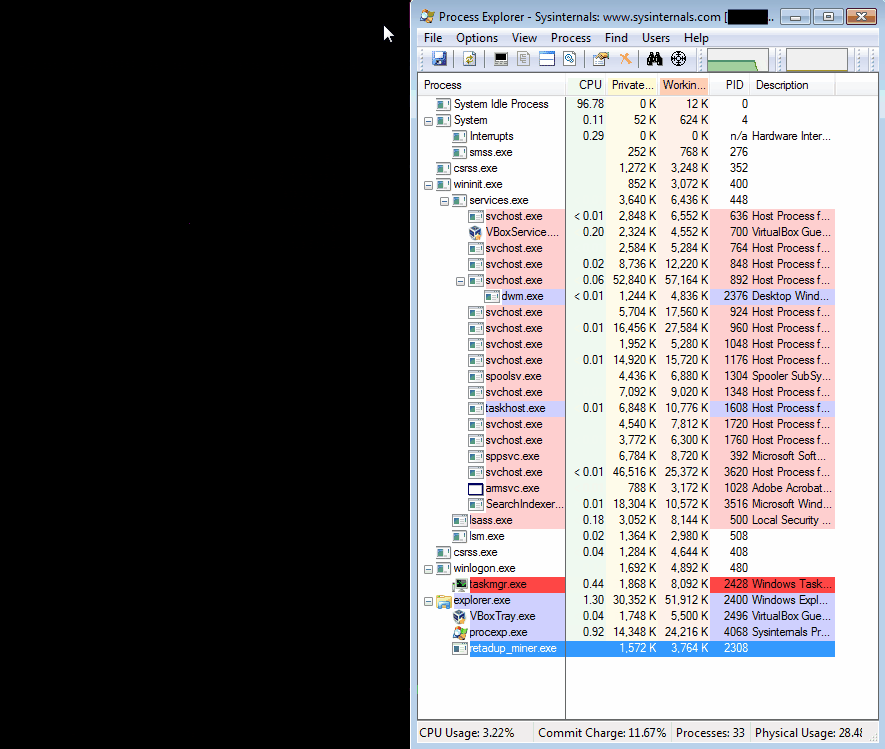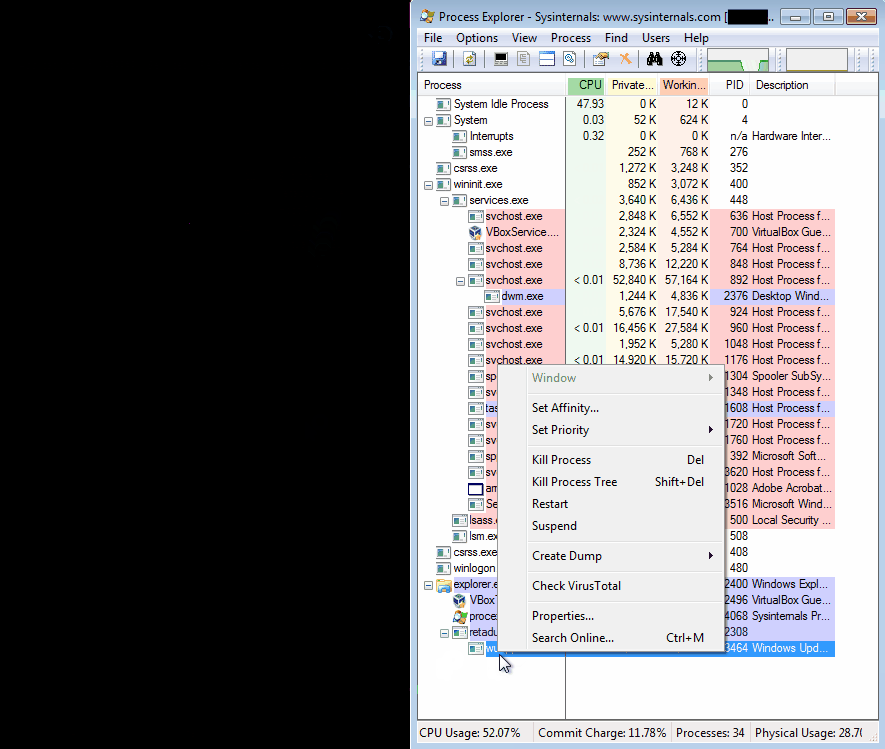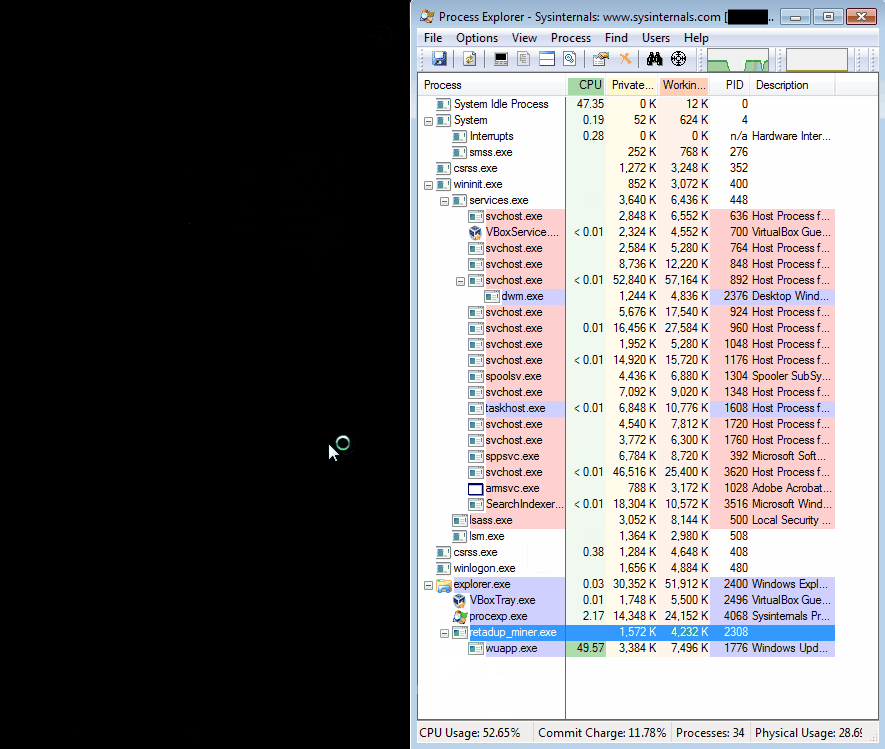
Retadup is a malicious self-replicating and auto-propagating worm that affects Windows systems (all versions) to mine cryptocurrency (Monero) for the account of its author, who has claimed it since last year on Twitter. After infecting over 850000 unique systems mostly in Latin America, Avast worked together with the French and U.S. law enforcement authorities and managed to stop the worm by causing it to destroy itself. Trend Micro discovered the worm back in April 2018, warning about its detection-evasion capabilities, as well as its polymorphism features.
Its my baby <3 https://t.co/E2dy6Dmpna
— black joker (@radblackjoker) April 27, 2018
Avast analyzed the worm and figured that its C&C infrastructure was based in France. They worked closely with the French police to take over one of the malicious servers and abuse it in a specific way that would neutralize Retadup. The French police did their part by compelling the hosting provider to share key data with Avast, who finally got a snapshot of the target server and were surprised to find that the contained executable files have been infected with the Neshta malware by mistake. In July, the legal proceedings were ready, so the C&C server was replaced with a disinfection server after Avast researchers abused a protocol design flaw in the target system.
Source: decoded.avast.io
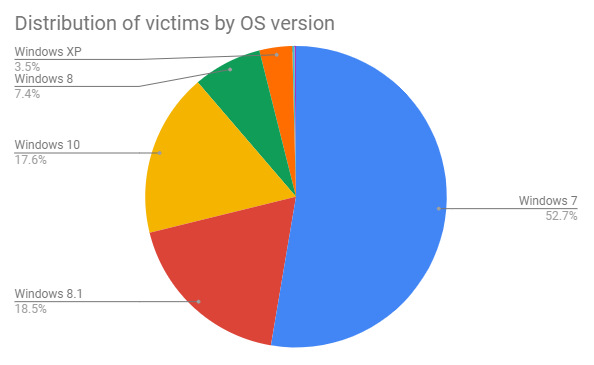
Having nullified the threat, the researchers analyzed the victim data that the worm was transmitting to the infrastructure and figured that over 85% of the victims were not using any anti-virus solution, and many of those who did had disabled it. More than half of the victims were using the soon to be unsupported Windows 7, while a significant 26% were using Windows 8 and 8.1. A notable 3.5% was using the wholly obsolete Windows XP system, so they were practically asking for a miner to take over their system resources.
Source: decoded.avast.io
The FBI was also involved because a small portion of Retadup’s infrastructure was based in the United States, so if it was ignored, the actor could potentially carry out a rebound from there. Speaking of which, the person has been identified to be a 26-year-old Palestinian. The real identity of the actor was tracked down by “Under the Breach” researchers, and as reported by ZDNet, they have found him through the domain registration data. The man was too proud of this creation, so he couldn’t keep a low profile and just reap the crypto mining fruits.
https://twitter.com/underthebreach/status/1166680142128848897
Were you infected by the Retadup worm? Share any details with us in the comments section below, or on our socials, on Facebook and Twitter.