DNSpionage Updated With a New Malware Called ‘Karkoff’
- The DNSpionage campaign gets freshened with a set of new spoofing elements and a shiny new malware called “Karkoff”.
- The new tool can execute code remotely by communicating with the C2 server through HTTPS.
- The malicious actors use the same infrastructure, the same C2 server, and the same document macros.
Cisco Talos researchers have been following the DNSpionage campaign since November 2018, tracking the activities of the threat actors, trying to trace them, and also monitoring any important updates in the malicious toolset that is used. As the team warns, there’s a new malware tool that is being deployed by the DNSpionage actors that the researchers named the “Karkoff”. This malware was first spotted at the beginning of April and is currently fully deployed as an indispensable part of the infection chain.
image source: blog.talosintelligence.com
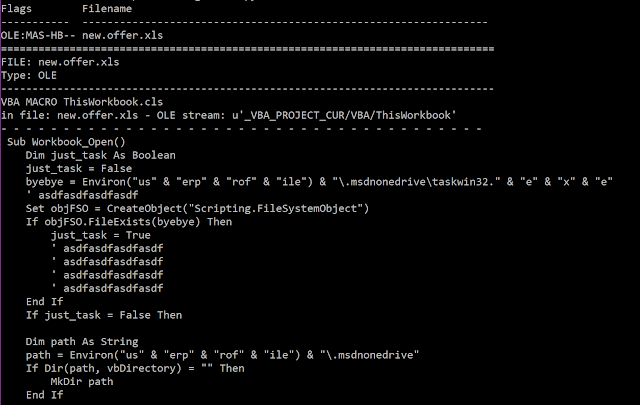
The infection chain starts with a new Microsoft Excel document that contains the same macro as before, with only slight differences in the use of the directories and the scheduled task names. The new payload that comes as a next step is Karkoff, developed in .NET, and being particularly small and lightweight. It supports C2 server-directed remote code execution through HTTP, HTTPs, and DNS communication. There’s no debug mode, and the malware is now dropped more carefully and more targeted based on the results of a WMI command that sends the system details back to the C2 server. The server is now mimicking the GitHub platform, while it previously was pretending to be Wikipedia.
image source: blog.talosintelligence.com
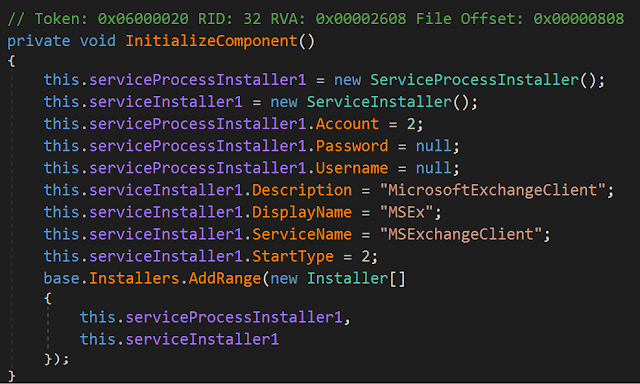
Karkoff sits in a Windows system disguised as a service named “MSExchangeClient”, and for the time being, there’s no real obfuscation in its operation. All commands that are executed by Karkoff are stored in a log file located on “C:\\Windows\\Temp\\MSEx_log.txt”, even including a timestamp for each entry. Should a company get infected by Karkoff, they will at least be able to trace back its activity and assess the damage done to their systems. Karkoff can dynamically adjust its configuration options based on the presence of AV tools in the infected system, like Avira and Avast anti-malware products. If these tools are installed and running, Karkoff will skip some of its actions to avoid detection.
image source: blog.talosintelligence.com
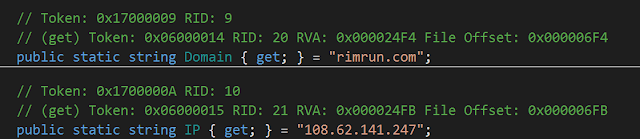
The Cisco Talos researchers have connected Karkoff with DNSpionage through the history of the IPs used for the C2 server domain (rimrun[.]com), identifying a clear infrastructure overlap. What this shows is that the DNSpionage is not only underway but also evolving to avoid detection. The new Karkoff malware is an example of that, while the subtle changes in the macro of the infection-initiation document are furthering the elusiveness. Right now, DNSpionage remains focused on the Middle Eastern region, targeting .gov domains in the United Arab Emirates and Lebanon.
Share your thoughts about Karkoff and who could be behind the DNSpionage in the comments section down below. Also, don’t forget to check TechNadu’s socials on Facebook and Twitter, for more daily tech news.