New Android Malware Called ‘TeaBot’ Is Spreading in Europe
- Dangerous new Android trojan TeaBot is spreading in Europe and is constantly adding more banks.
- The malware is distributed as TeaTV or VLC MediaPlayer and asks users to grant a galore of permissions.
- The actors are most probably interacting in real-time with the device, dropping the right overlays and stealing credentials.
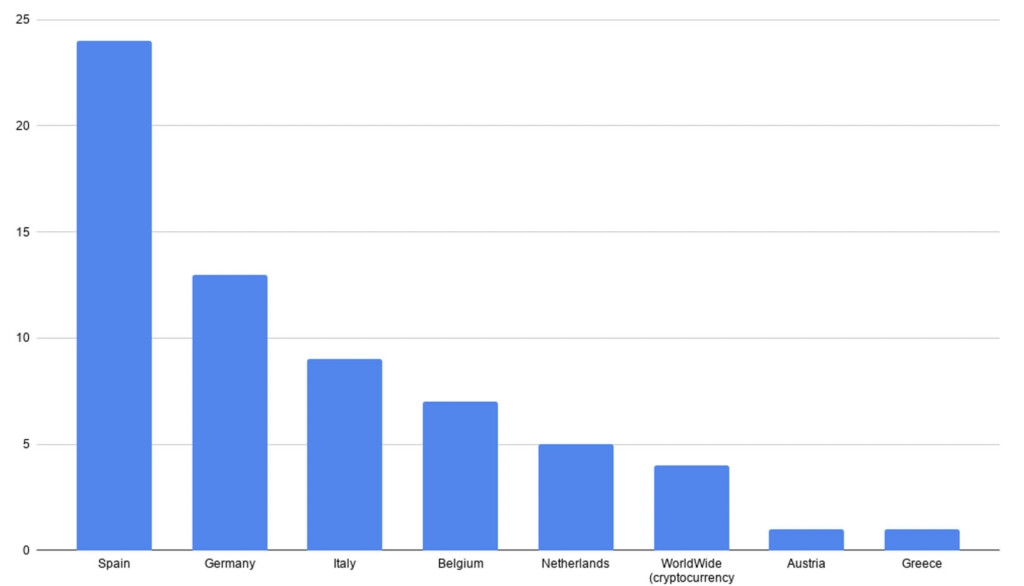
A team of researchers at Cleafy has discovered a new Android banking trojan which they call ‘TeaBot,’ and which has been spreading across European countries since January 2021. The goal of the malware is to steal user credentials and SMS messages and use them both for taking over banking accounts. According to the report, over 60 European banks are targeted, but the biggest volume of distribution is seen in Spain, Germany, Italy, Belgium, and the Netherlands. That’s in line with Flubot, but the researchers clarify that this is a novel malware.
The malware is being under active development and is gradually adding more banks and countries. For example, Italian banks were added in March, while Belgium and Netherlands were added as targeted countries at the beginning of May. This means the particular piece of malware may soon find its way to countries outside Europe, possibly the United States and the United Kingdom, two big “victim pools” that are currently missing.
The abilities of TeaBot include the following:
- Ability to perform Overlay Attacks against multiple banks applications to steal login credentials and credit card information
- Ability to send / intercept / hide SMS messages
- Enabling key logging functionalities
- Ability to steal Google Authentication codes
- Ability to obtain full remote control of an Android device (via Accessibility Services and real-time screen-sharing)
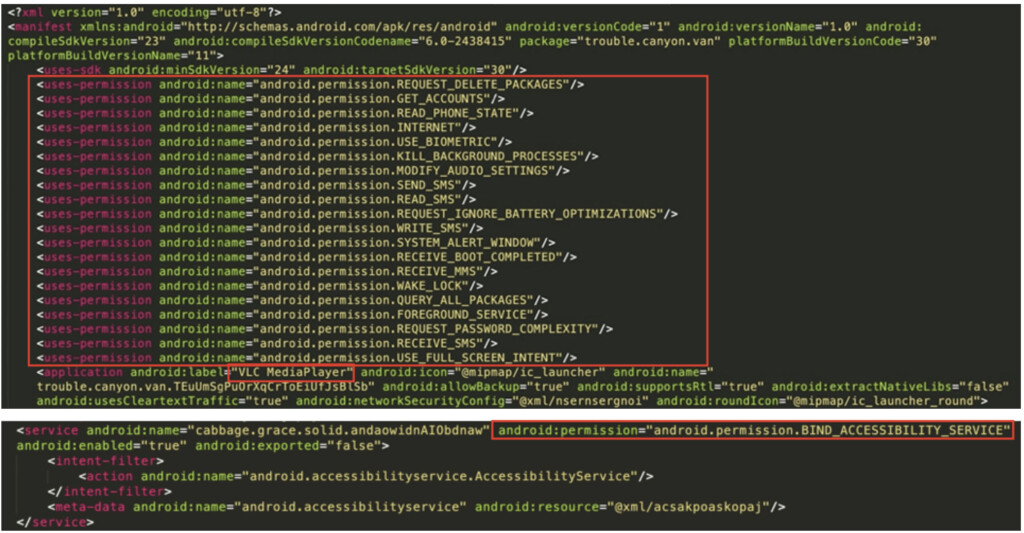
These are achieved by ensuring the granting of the following permissions upon installation:
- Send / Intercept SMS messages
- Reading phone book and phone state
- Use device supported biometric modalities
- Modify audio settings (e.g., to mute the device)
- Shows a popup on top of all other apps (used during the installation phase to force the user to accept the accessibility service permissions)
- Deleting an installed application
- Abusing Android Accessibility Services
After installation:
Observe actions
Retrieve window content
Perform arbitrary gestures (ignore battery optimizations)
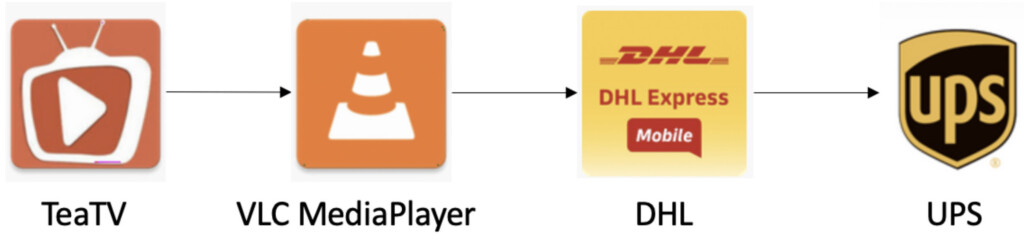
As for what app icons are used by TeaBot as a method of hiding from the user, these include TeaTV, VLC MediaPlayer, DHL, and UPS. It goes without saying that the authors may update this set and use other apps for imitation, so you should remain vigilant even if you don’t have any of these four on your app drawer. After all, the malware is removing its icon from the device once it is granted the requested permissions.
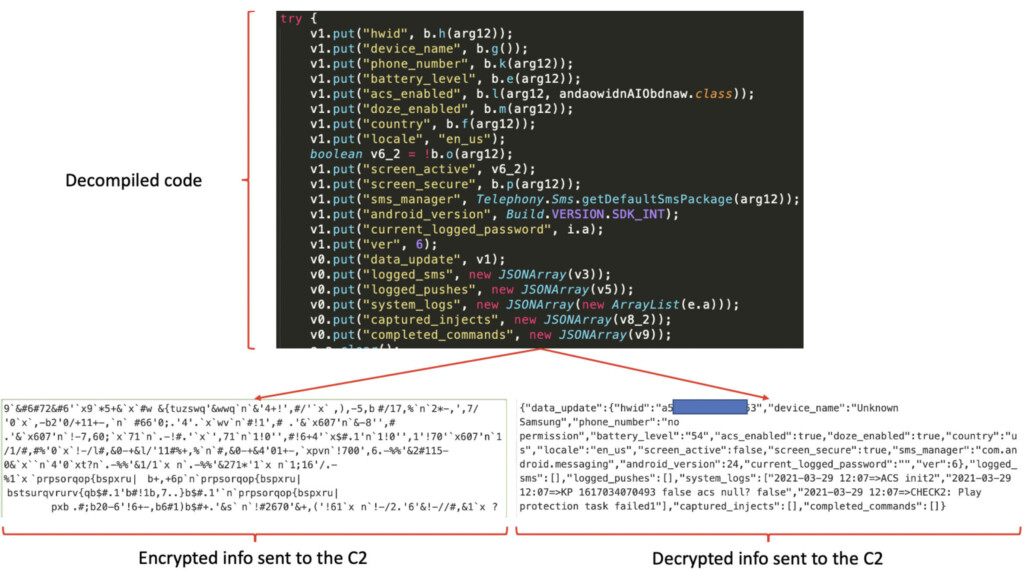
In terms of the TeaBot communications with the C2, the malware is sending POST and GET requests every 10 seconds, and the former is encrypted with the XOR algorithm. The researchers believe that TeaBot is configured for real-time interaction with the compromised device, that’s why the requests are so frequent.
To protect yourself against these threats, only download software from trustworthy and reputable sources, use Google Play, review the requested permissions carefully before granting, and use a mobile security solution. In this case, installing a media player like VLC shouldn’t be accompanied by requests to send SMS messages, reading the contacts list, or use biometric sensors.