Microsoft November 2020 Patch Tuesday Fixes Kernel Zero-Day
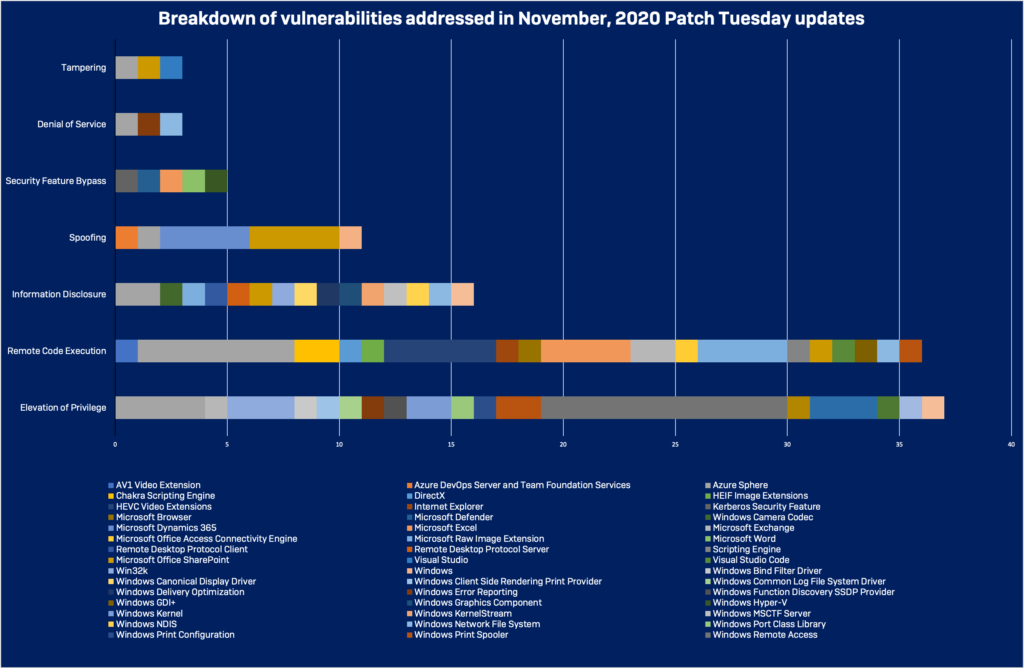
- Another month is gone, another Tuesday patch from Microsoft is here, fixing 112 bugs.
- Most of the vulnerabilities discovered and fixed this month are RCEs and privilege escalation flaws.
- Microsoft has adopted a new way of reporting CVSS details, which is more condensed and less detailed.
Microsoft has released this month’s “Tuesday Patch,” bringing on 112 security fixes, of which 18 are classified as critical, and another 92 are marked as important. Among them, there is the “CVE-2020-17087,” a zero-day Windows kernel flaw that was reported last month by Google Project Zero researchers and confirmed to be actively exploited in the wild. This is a nasty elevation of privilege flaw lying in the kernel’s cryptography driver (cng.sys), creating a sandbox escape opportunity for a local attacker.
Another critical vulnerability addressed through this latest patch is “CVE-2020-17051,” which has a CVSS severity score of 9.8. This is a remote code execution bug that doesn’t require user interaction or authentication on the target machine.
One more remote code execution flaw that was fixed with this patch is “CVE-2020-17052,” which requires user interaction to trick them into opening a specially-crafted web page using Edge or Explorer. By doing so, a memory corruption condition is created, opening up the way to further exploitation.
Related: Latest Windows 10 Update Boots Adobe Flash Player Permanently
The rest of the critical flaws are given in the list below:
- CVE-2020-17105 – AV1 Video Extension Remote Code Execution Vulnerability
- CVE-2020-17101 – HEIF Image Extensions Remote Code Execution Vulnerability
- CVE-2020-17106 – HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2020-17107 – HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2020-17108 – HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2020-17109 – HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2020-17110 – HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2020-17058 – Microsoft Browser Memory Corruption Vulnerability
- CVE-2020-17078 – Microsoft Raw Image Extension Remote Code Execution Vulnerability
- CVE-2020-17079 – Microsoft Raw Image Extension Remote Code Execution Vulnerability
- CVE-2020-17082 – Microsoft Raw Image Extension Remote Code Execution Vulnerability
- CVE-2020-17042 – Windows Print Spooler Remote Code Execution Vulnerability
Elevation of privilege flaws took the “lion’s share” this month, while remote code execution vulnerabilities also had a respectable count. Quite a few information disclosures and spoofing bugs were fixed this time, too.
One of the things that Microsoft changed this month is how they report details about the fixed bugs. In general, we can say that CVSS details have been limited to “industry standard” information, taking away detailed descriptions, the scope of the vulnerability, the ways/methods of its exploitation, and what the potential damage for the users could be. Microsoft explained why they opted for that, but the truth is that not everyone out there is happy with this change.
As always, make sure to back up your files and data before you apply the update, and do it as quickly as practically possible. Security patches shouldn’t be postponed for long, but at the same time, they should be treated with respect as they can break your system.