Facebook Refuses to Fix a Bug that Allows Clickjacking Worms to Function
- Security researcher discovers an exploitable bug in Facebook’s mobile app.
- Facebook rejects the researcher’s report, claiming that the 'feature' can’t have serious security consequences.
- Researcher publishes everything to highlight the seriousness of the situation if malware links replaced spam links.
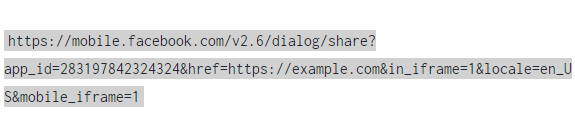
As reported by a Polish security researcher and analyst who goes by the Twitter username 'Lasq', Facebook is already ridden by clickjacking worms that automatically add spam links on the users’ walls. The researcher noticed a French-comic themed spam campaign through the multiple relevant posts on the walls of his online friends, so he decided to get to the bottom of it. The link led to a comic page that contained quite a lot of ads as well, but the strange thing was the automatic posting of the same link to the user’s wall. Lasq spotted an iframe tag that led to a series of re-directions that ended up to the final:
From Lasq's report
This is basically a 'Facebook share' URL, and as the researcher looked deeper into it, he noticed that it contained a mobile subdomain. After confirming that desktop browsers won’t let the worm work thanks to their DENY setting on the 'X-Frame-Options', he tried the Facebook app (mobile) and this time the DENY header was ignored. Proceeding further, the researcher experimented by adding other types of content in the iframe, only to discover that Facebook’s mobile browser only ignores the DENY header of the X-Frame-Options for the particular API call that the spammers were taking advantage of.
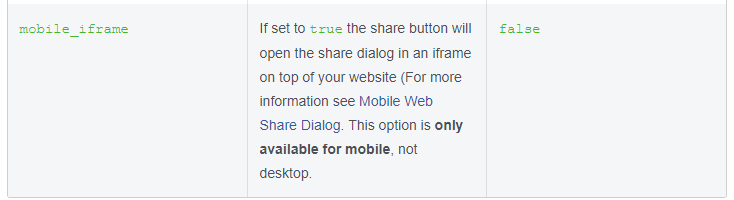
It is very likely that the spammers discovered this “bug” by simply reading the Facebook Developer documentation which seems to present it as a feature.
Mobile iframe parameter (from Facebook's Developer documentation)
Having concluded the investigation, Lasq reported the findings to Facebook’s Bug Bounty platform and it got rejected 12 hours after its submission. Facebook declined that the specific bug has any security implications, as the clickjacking doesn’t change the state of the account of the affected user. This led to the revelation of the whole story by Lasq, who highlights the fact that someone could abuse this poorly implemented “feature” to do much more serious harm to users through malware or phishing links.
When contacted by ZDNet on the issue, Facebook gave the following reply: “To help prevent abuse, we use clickjacking detection systems for any iframeable plugin product. We continuously improve these systems based on signals we observe. Independently of this report, earlier this week we made improvements to our clickjacking detections that mitigate the risks described in the researcher's report.”
Indeed, Facebook does have additional security precautions for its mobile app in place, in the form of a pop-up that asks the user to confirm the sharing of the spam link. However, the specific spammer group got around this precaution somehow, so the users do not get that additional confirmation step.
What is your experience with Facebook worms and spam campaigns? Let us know in the comments below, and also visit our socials on Facebook and Twitter to stay tuned with the latest developments in the tech world.