New Phishing Campaign Using the ‘NetSupport Manager’ RAT
- Unit42’s Cortex XDR caught a new phishing campaign in its net, which tries to drop a RAT on the victim’s system.
- The tool is the ‘NetSupport Manager’, which has been used for malicious purposes again in the past.
- The phishing mail tries to trick the recipient by mentioning order details and unauthorized payments.
Researchers at Unit42 have detected a new phishing campaign that attempts to plant the ‘NetSupport Manager’ RAT (remote access tool) onto its victims' systems. The bait is a malicious Microsoft Word document that is disguised as a password-protected NortonLifelock file. NetSupport Manager is a tool that is typically used by network and system administrators for legitimate purposes, but phishing actors deploy it as well since it enables them to gain unauthorized access onto the victim’s computer.
According to the report, the activity of the particular campaign first appeared in November 2019 and culminated in January 2020. The phishing email claims that the attached document contains important information for the recipient, and provides a password to open it. Usually, there’s also a mention of a person that is somehow associated with the recipient. As for the email subject, this is usually dealing with refunds, unauthorized transactions, or order inquiries. The message also informs that in order to enter the password, the user will have to enable macros on their Office suite.
Source: Unit42
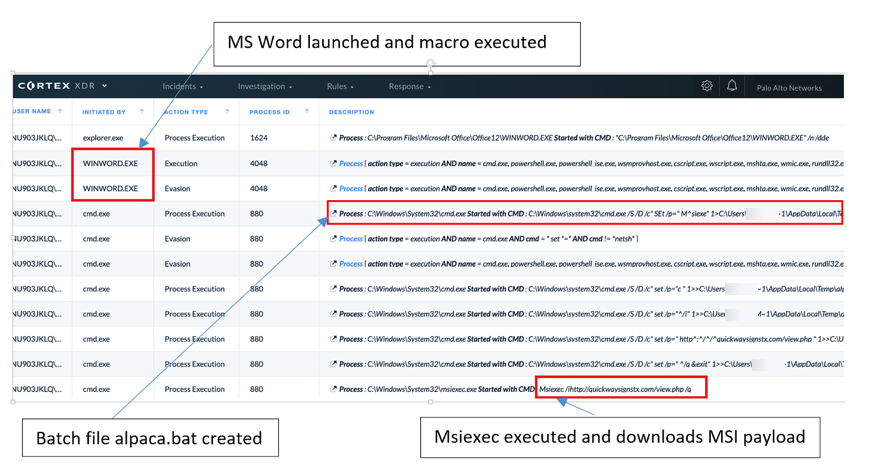
Once the victim does that and enters the correct password on the dialog box, the macro executes its nasty code which builds command strings and obfuscates them on VBA. The command strings launch an executable named ‘cmd.exe’, construct a batch file named ‘alpaca.bat’, and execute it. Next, an MSI payload is fetched through msiexec, which installs a PowerShell script, Eventually, that script installs the NetSupport Manager RAT and establishes its persistence by planting keys on the system registry. Before doing that though, it checks for the presence of Avast or AVG Antivirus and acts accordingly. If all goes well, the RAT tool establishes communication with ‘geo.netsupportsoftware[.]com’ and sends the geolocation data of the host.
Source: Unit42
Most likely, this campaign is fueled by cyber-espionage motives, as the goal of the actors is to roam inside the compromised systems and search for useful information. Most of the phishing emails end up in the inboxes of film producers and printing companies, so this indicates a narrow targeting approach. Finally, the actors are sending emails from domains that were registered only a day before or even less, so that they can get through the spam or phishing filters that may be in place. The use of NetSupport RAT for malicious purposes isn’t anything new, as FireEye reported something similar back in April 2018, while Zscaler discovered two campaigns deploying the particular RAT in November 2019.