450,000 QNAP Devices Remain Vulnerable to Documented RCE Flaws
- Four QNAP Photo Album vulnerabilities that were discovered and fixed last year are still affecting 450k instances.
- The researcher who discovered it now published the proof of concept code, so patching has become imperative.
- The implications of using a vulnerable version include the accessing of your files by unauthorized users.
Researcher Henry Huang warns about the fact that approximately 450,000 QNAP NAS instances that are indexed by Shodan remain vulnerable to the highly critical exploit chain consisting of CVE-2019–7192, CVE-2019–7193, CVE-2019–7194, and CVE-2019–7195. The researcher has scanned random samples of the 564k QNAP instances and found that 80% of them have “Photo Station” enabled, so by a statistical estimation, the number of vulnerable instances is approximately 450,000. All Photo Station versions below 6.0.3, 5.2.11, and 5.4.9 are vulnerable to the exploit chain mentioned above. QNAP had published a security advisory for this way back in November 2019.
QTS administrators are advised to log in, go to Control Panel > System > Firmware Update, click on the “Check for Update” under the Live Update tab, and let the system do the rest. Alternatively, you may visit the QNAP website, go to Support > Download Center, and then pick the right firmware pack for your specific device. On the Photo Station, admins may find the update on the “App Center,” which can fetch and install the latest available update automatically.
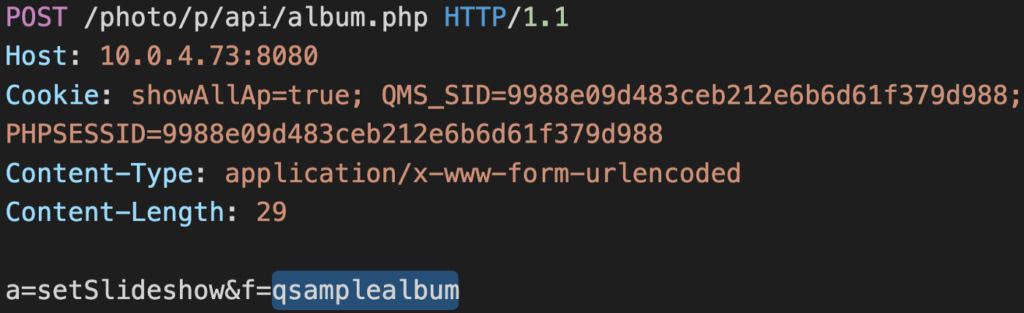
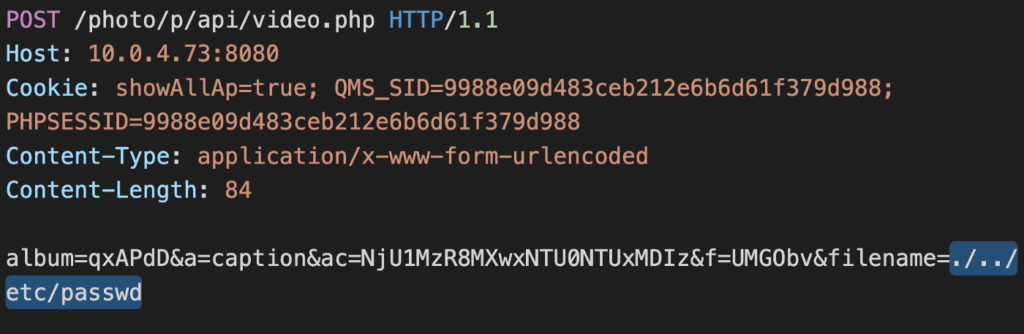
So, what is the danger exactly? Photo Station is an online photo album where users may upload, organize, and share photos and videos with others (family members, friends, colleagues). It supports image tags, slideshows, date filters, sharing history, GPS mapping, timeline, and more. The problem is that someone can access these instances without having to authenticate, thus accessing the personal files of other people. The first flaw concerns an API exploitation where an attacker can replace the album ID of a private collection with that of a publicly accessible album meant to be used in samples. This is a bypassing trick that results in information disclosure and eventually leads to privilege escalation.
Source: Medium.com
Source: Medium.com
Other vulnerabilities include the injection of arbitrary PHP code to the session for authentication tampering, while the other two concern the writing of code to random locations. All four have been reported to QNAP last summer, and the company pushed fixing updates on December 12, 2019. This is the first time that the proof of concept code has been published, thus, if you still haven’t upgraded your QNAP, do it immediately. There are about 450,000 vulnerable instances still indexed online, so crooks will now engage in a race to try accessing and possibly even downloading as many albums as possible.