New Lokibot Campaign Comes With Updated Tricks
- The latest Lokibot campaigns rely on social engineering the victims with blurred images.
- The obfuscation of the final payload has been upgraded with three levels of cloaking now.
- Lokibot has grown into a more sophisticated malware but still needs those macros activated.
Cisco Talos researchers have taken a deep dive into a recent Lokibot campaign’s specifics and discovered the new tricks that help threat actors achieve their goals. Lokibot is one of the most well-known and widely-used info-stealers, so any new improvement or addition to it has a potentially high and extensive impact on a large number of victims.
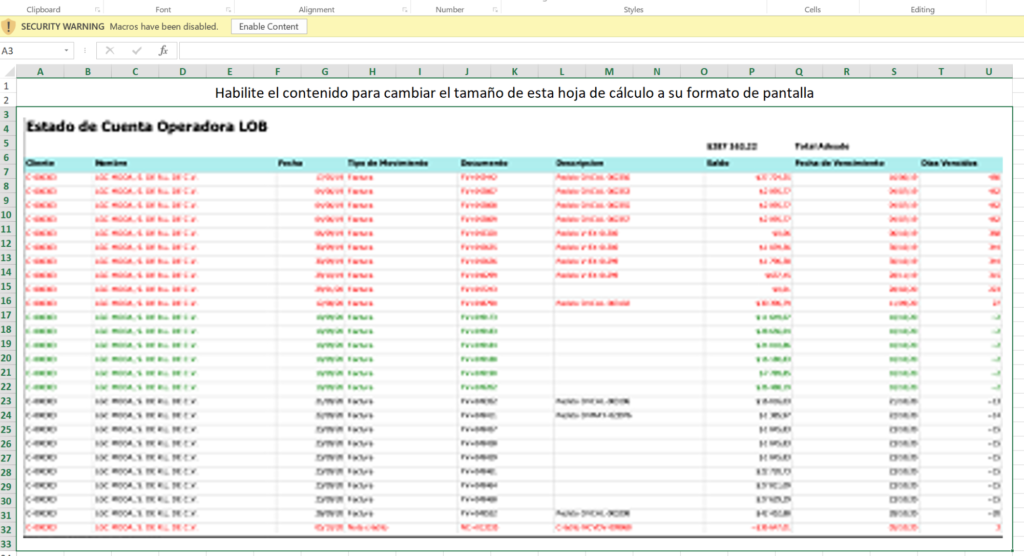
The new sample analyzed by the Talos team is blurring the images in documents to convince the recipients to enable macros on their office suite. This is crucial for the initial code execution, so it makes sense to focus on it.
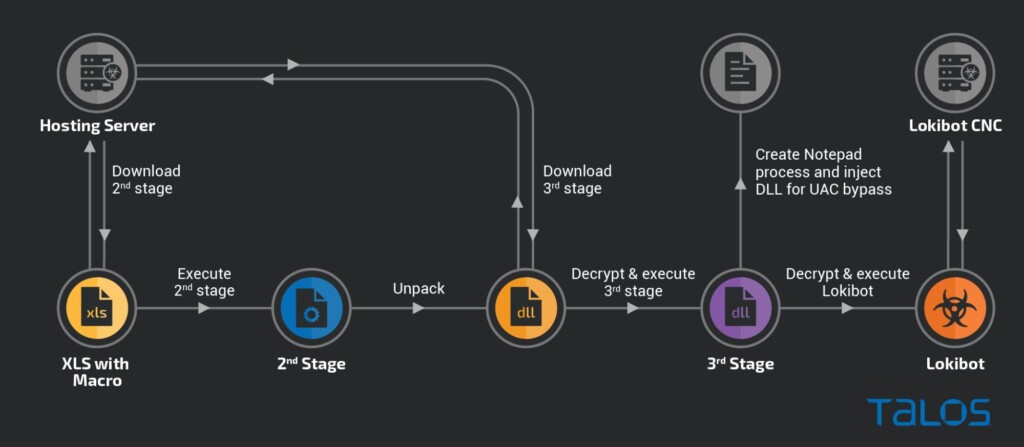
The attack begins with the arrival of an XLS document that accompanies a phishing email as an attachment. The macro that runs through the office suite is fetching a second-stage downloader, which, in turn, gets a heavily encrypted (three layers) Lokibot. A privilege escalation step is also involved at this stage, as shown in detail on the following infection chain diagram.
The trick of blurring the contained images, which supposedly display key information relevant to payments, is simple yet very powerful. The victim also sees a static message reading “Changing the size of this document, please wait,” so many fall for the trap of enabling content thinking it will make the image visible.
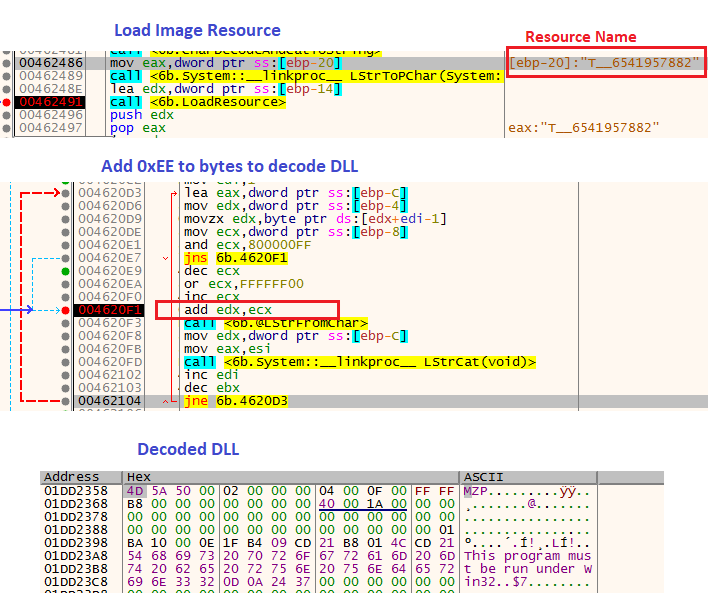
The second and third stages of the infection are written in Delphi, and the actors have bothered to “play” with image steganography, encoded DLLs, and long hexadecimal variable names. All of these methods are meant to help with obfuscation and detection evasion. At the same time, it also turns the analysis procedure into a challenging step-by-step decoding and reverse-engineering process.
While Lokibot, as most of the malware that’s circulating out there, is getting more sophisticated, the threat actors’ success still relies on social engineering the victims. The detection of Lokibot has certainly gotten harder, and the final payload is now undoubtedly very well hidden, but none of that matters if you just keep your office suite macros disabled at all times.
Remember, Lokibot can steal credentials from web browsers by using a keylogger that monitors browser and desktop activity. While this particular campaign uses emails to reach victims, others have used laced game installers, IM messages, forum posts, and torrent files, so there are multiple distribution channels to be aware of.