Aaron Bishop – U.S. Department of Defense Aaron Bishop has been named Deputy Chief Information Officer for Cybersecurity and Chief Information Security Officer at the…

We observed threat actors’ continued abuse of artificial intelligence, phishing, and identity impersonation using stolen credentials. Targets primarily included government systems and vulnerable individuals online. …
Key TakeawaysGotaTun security audit findings: Independent review found no major vulnerabilities in GotaTun v0.2.0 during January–February 2026 security assessment.Low-severity issues identified: Audit highlighted predictable session…

Key TakeawaysExploitation Charges: Zobaidul Amin, a Bangladeshi national, is making his initial court appearance in Alaska for operating an international child exploitation enterprise.Minors Abused: Amin…

Key TakeawaysCrypto Theft: The FBI arrested a suspect for stealing $46 million in cryptocurrency linked to the 2016 Bitfinex hack.Government Funds: The individual allegedly diverted…

Key TakeawaysPotential Compromise: The FBI has acknowledged identifying and addressing suspicious activity on its internal networks.Sensitive System: Reports suggest the activity targeted a sensitive network…

Key TakeawaysPersistent Presence: Iranian cyber group MuddyWater infiltrated multiple U.S. and Israeli networks, maintaining persistent access since at least early February 2026.New Backdoor: Attackers deployed…

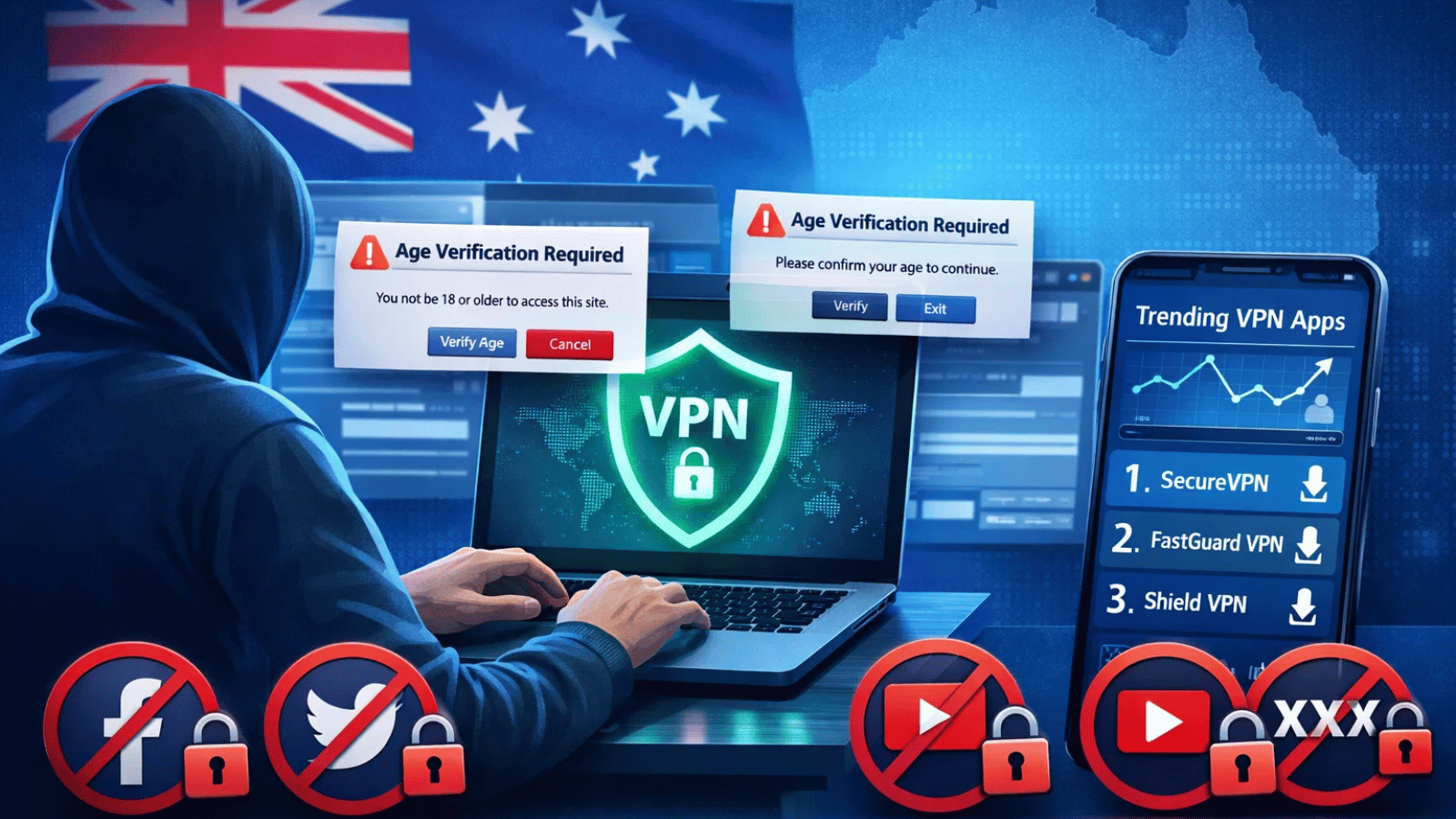
QUICK ANSWERExpressVPN MCP server launch: ExpressVPN launches first VPN MCP server enabling AI tools to manage VPN status, switch regions, and run diagnostics locally.AI integration…

Key TakeawaysGuilty Plea: Evgenii Ptitsyn pled guilty to wire fraud in connection with his role as an administrator for the global Phobos ransomware network.Ransomware Revenue:…
QUICK ANSWERPureVPN Network Expansion: Added 40+ global servers improving speed, stability, and regional connectivity for all users.Improved Latency and Stability: Shorter routing paths and distributed…

Key TakeawaysOfficial Inquiry: The UK's Information Commissioner's Office (ICO) is formally contacting Meta regarding significant data privacy concerns linked to its AI-powered smart glasses.Intimate Data…

Key TakeawaysCoordinated Campaign: Almost 150 hacktivist-led Distributed Denial-of-Service attacks have targeted 110 distinct organizations across 16 countries.Critical Sector Focus: Twelve threat groups primarily focused on…

Key TakeawaysPlatform Disruption: International law enforcement successfully executed a coordinated global cybercrime operation to completely shut down LeakBase, a massive illicit data repository.User Deanonymization: Authorities…

Key TakeawaysMassive Scale: The open-source CyberStrikeAI framework orchestrated over 600 unauthorized network intrusions spanning 55 countries.Targeted Infrastructure: Threat actors specifically compromised FortiGate appliances utilizing 21…

Key TakeawaysSurveillance Compromise: Suspected Iran-nexus threat actors are actively exploiting exposed network cameras, possibly for real-time assessments of battle damage.Targeted Hardware: The campaign targets known…
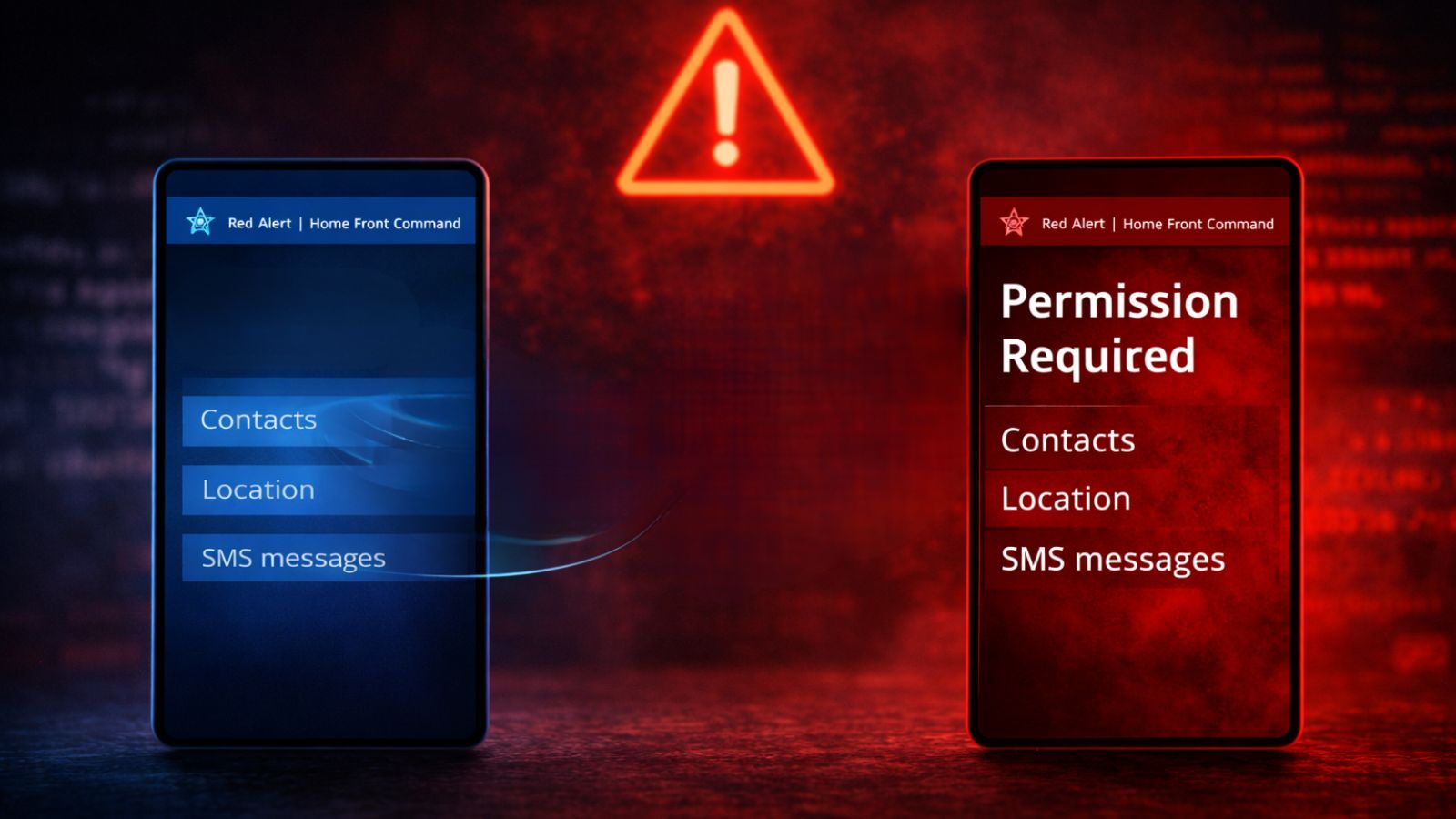
Key TakeawaysSMS Trojan: Threat actors are executing a RedAlert Trojan campaign using targeted SMS phishing to distribute a malicious Android application.Impersonation: The fake emergency alert…

Key TakeawaysExploit Proliferation: A sophisticated suite of hacking tools designed to compromise iPhones has been leaked and is now actively used by cybercriminals.Broad Impact: The…

Key TakeawaysExploited Authorization Flows: Threat actors are manipulating OAuth redirect URIs to route authenticated users to malicious infrastructure undetected.Sophisticated Payloads: The campaign deploys embedded ZIP…

Key TakeawaysNetwork Disruption: The Denmark School District experienced a prolonged internet outage stemming from an alleged internal vulnerability.Operational Impact: The lack of connectivity forced educators…