“ElectroRAT” Is Threatening to Steal Your Precious Crypto
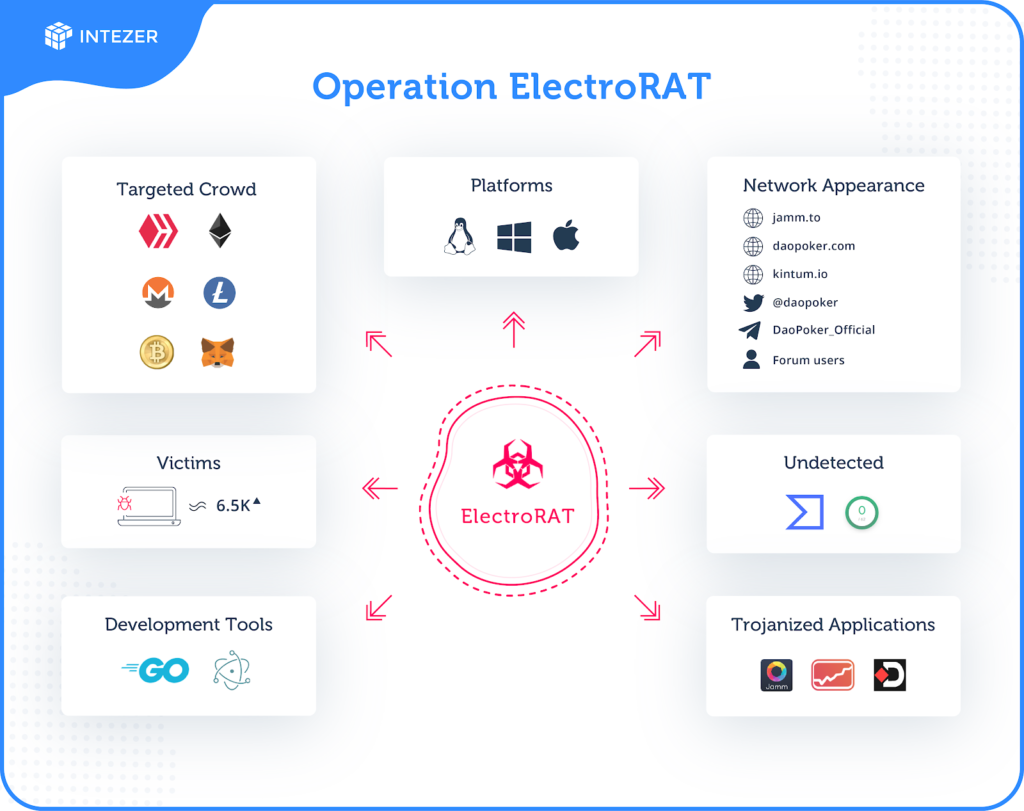
- A year-long campaign that has compromised about 6.5k crypto holders has been discovered.
- The actors are using a custom-made info-stealer that works across all major operating systems.
- The campaign was built around fake apps, scamming domains, and accompanying social media accounts.
As the value of virtually all cryptos is going through a meteoric rise at the moment, hackers are upgrading their efforts to steal whatever they can from the holders. According to a recent report by Intezer Labs, an operation which they named “ElectroRAT” is now underway, aiming to drain crypto wallets by using fake apps, scamming domains, and tricky social media accounts.
Based on the evidence, the operation has been underway since January 2020, but it was discovered only last month. So far, it is estimated that at least 6,455 cryptocurrency holders have fallen victim to ElectroRAT.
The actors have created three trojanized applications covering the three major OSes, Windows, Mac, and Linux. The applications are the “Jamm,” “eTrade,” and “DaoPoker.” The first two focus on trade management, while the third one is a poker app for people who want to play by betting crypto.
The campaigners have been promoting these apps on forums that are popular in the blockchain community, as well as via their social media accounts. The apps were built using the Electron platform, hence the name of the campaign.
These three apps contain info-stealers similar to “Amadey” and “KPOT,” written from scratch in Golang to achieve multi-platform functionality as well as to evade detection from AV tools. The victim doesn’t realize what’s happening under the hood and only gets to see a seemingly innocuous app with a friendly and contemporary GUI.
The “mdworker” that works in the background, though, is performing keylogging activities, takes screenshots, and uploads files from the disk to the C2. Moreover, it can fetch additional payloads or enable the actors to execute commands onto the victim’s machine remotely.
If you suspect an infection or if you have downloaded anything from ‘kintum[.]io,’ or ‘daopker[.]com,’ or ‘jamm[.]to,’ you should first kill the malicious processes and run an AV tool scan. After that, move your assets to a new wallet and reset all your passwords.
Finally, add MFA steps anywhere possible. Intezer Labs offers a free edition of its security and threat detection tools, which have the ElectroRAT threat indexed, so you may grab that one and see if anything comes up.