Unprotected MongoDB Database Contains 275 Million Records of Indian Citizens
- A MongoDB database containing the PII of many millions was left exposed for at least two weeks.
- Hackers took over control of the MongoDB server and wiped the database clean, asking for ransoms now.
- The owner of the database remains unidentified, and no protective action was ever taken.
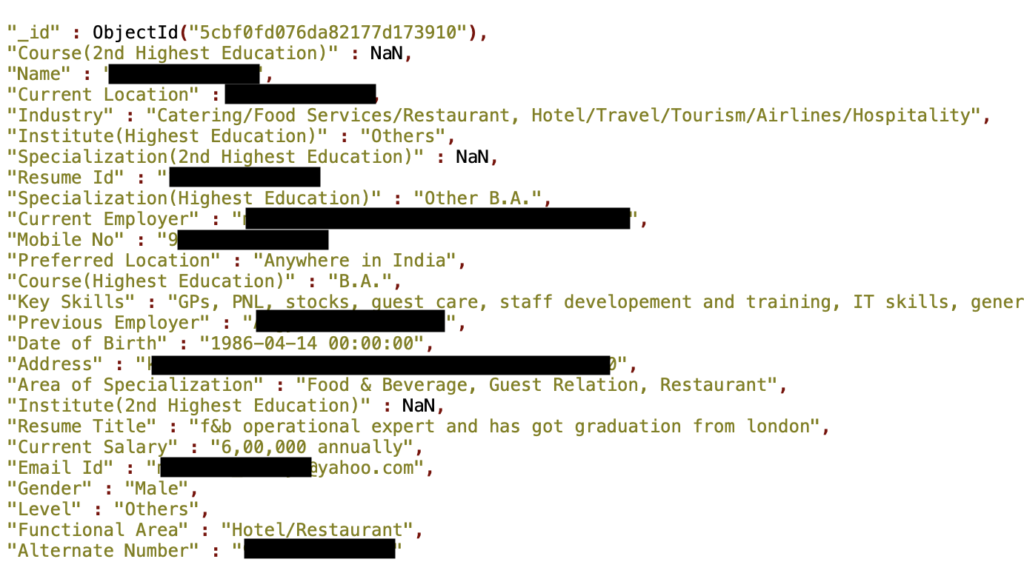
Researcher Bob Diachenko has discovered yet another unprotected and publicly indexed MongoDB database that contains more than 275 million records belonging to Indian citizens. The number of affected individuals may be less than the amount of the records, but it could potentially be 275 million as well. The PII (personally identifiable information) in each record includes sensitive information such as the name, email, gender, mobile phone number, and the date of birth. Moreover, there are profession-related details in each record, like the skills and functional area, employment history and current employer, the current salary, and the education level.
image source: securitydiscovery.com
The salary combined with the name is a cocktail of danger for those exposed, while the rest of the sensitive data may also be used for a series of malicious purposes. The researcher tried to act responsibly and inform the owner, but there was no indication about who that is, and reverse DNS provided no useful results on that regard. Hosted on Amazon AWS, the database has been left open to access since at least April 23, 2019. As the severity of the leaking data was immense, the researcher notified the Indian Computer Emergency Response Team, which is an office within the Ministry of Electronics and IT, but the database remained unprotected for another week.
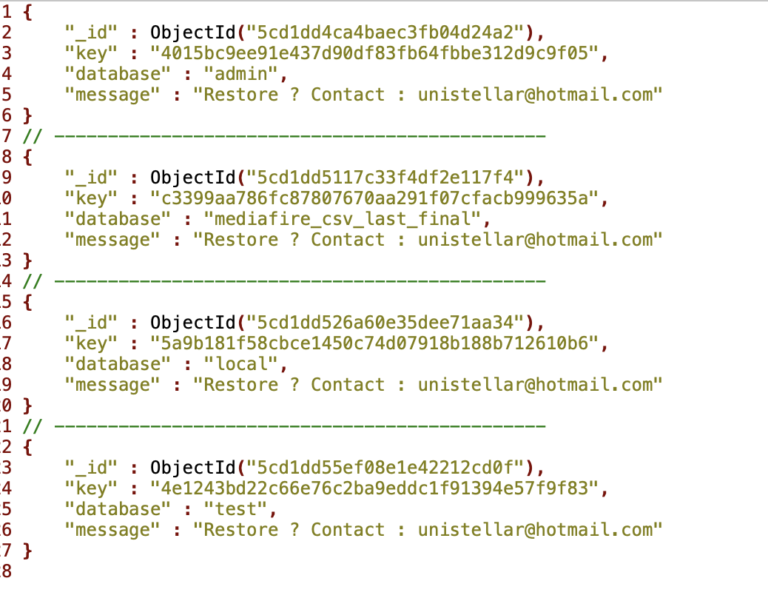
What happened then was the seizure of the database by a group known as “Unistellar”, who are now demanding a ransom in order to give the database back to the owner. Again, taking over this database was only possible thanks to the lack of any authentication steps which allowed the hackers to install ransomware on the MongoDB servers. Simply put, anyone could hop in and act as the administrator, which Unistellar did. Maybe the absence of the database entries will help in activating the owner finally, so hopefully, they will notice that they blundered after all.
image source: securitydiscovery.com
The people who had their sensitive data exposed though will need to ask for an explanation from the owner of the database in question. India’s CERT also demonstrated a level of negligence, as a full week passed before hackers located the database and stole all of its contents. Now, they could at least focus on tracking down the owner, as this would be the logical next step for the protection of so many millions of Indian citizens.
Care to share your thoughts on the above? Feel free to do so in the comments section down below, and also on our socials, on Facebook and Twitter.