GrayBravo Expands CastleLoader Malware Operations with Distinct Activity Clusters, Impersonates ‘Booking’ and ‘DAT Freight’
Key Takeaways
- Targeted clusters: Four distinct activity clusters leveraging GrayBravo's CastleLoader malware target industries ranging from logistics to hospitality.
- MaaS ecosystem: The diverse tactics and victim profiles across these clusters reinforce the assessment that GrayBravo operates a sophisticated MaaS ecosystem.
- Evolving tactics: Tactics include "ClickFix" social engineering, impersonation of legitimate brands, and the use of malicious signed MSI installers.
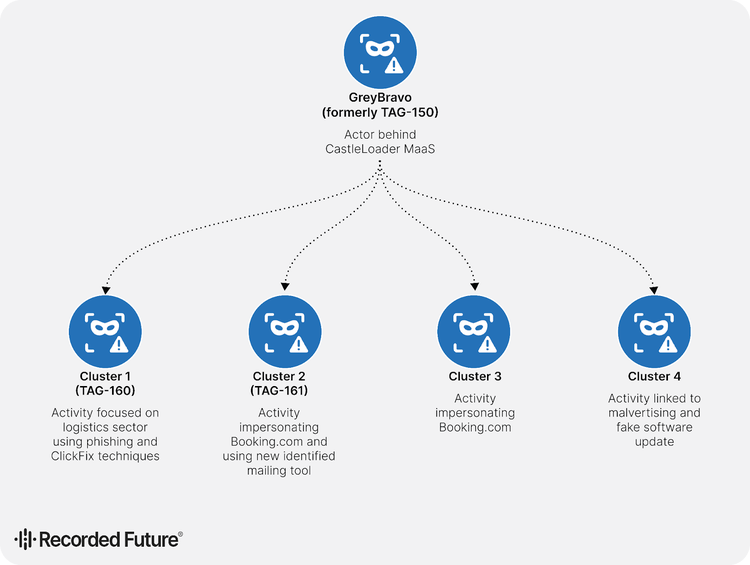
New research indicates that the threat actor known as GrayBravo (formerly TAG-150) has significantly expanded its operations, with its CastleLoader malware now being deployed across four distinct activity clusters targeting specific industries, including logistics and hospitality.
Notably, the threat actor impersonates known entities such as Booking.com and DAT Freight.
Logistics and Hospitality Industries Under Fire
Each cluster exhibits unique tactics, techniques, and procedures (TTPs), reinforcing the theory that GrayBravo is operating a scalable Malware-as-a-Service (MaaS) ecosystem, the latest The Recorded Future report said.
These clusters are:
- TAG-160 targets the logistics sector,
- TAG-161 uses Booking.com-themed lures across a wider range of victims,
- a third also impersonating Booking.com independently from the previous group,
- a fourth distributing CastleLoader through malvertising and fake software updates.
One of the most prominent clusters, tracked as TAG-160, focuses heavily on the logistics sector. Attackers in this cluster use sophisticated phishing lures that impersonate legitimate logistics firms and abuse freight-matching platforms such as DAT Freight & Analytics and Loadlink Technologies.
By spoofing emails and re-registering legitimate domains, they effectively deceive victims into executing the malware. Another cluster, TAG-161, targets a broader audience by impersonating Booking.com.
This group employs "ClickFix" techniques, tricking users into copying and pasting malicious commands, to deliver payloads such as CastleLoader and Matanbuchus, and utilizes novel phishing email management tools to coordinate its attacks.
Evolving Activity Clusters and Mitigation
The discovery of these CastleLoader activity clusters highlights the evolving nature of the threat. Beyond logistics and hospitality, other clusters employ malvertising and fake software updates to distribute payloads.
The infrastructure supporting these operations is multi-tiered and robust, often leveraging compromised legitimate internet services. Security professionals are advised to:
- Implement strict email filtering,
- Block indicators of compromise (IoCs) associated with known loader infrastructure,
- Monitor for unusual connections to services like Pastebin or Steam Community profiles, which are often used for command-and-control (C2) communication.
In other recent news, a new packer-as-a-service called Shanya emerged. It offers sophisticated obfuscation features to cybercriminals and is already used by the Akira, Qilin, and Medusa ransomware groups.
Fake Booking.com sites distributing AsyncRAT were seen in June, when scammers targeted the brand with generative AI phishing campaigns. A ClickFix attack leveraged email invite lures to send users to spoofed Microsoft Teams login pages in August.