FrogBlight Android Banking Trojan Targets Turkish Android Users via Smishing and Fake Government Court File Portals
Key Takeaways
- New threat: A new Android banking trojan, dubbed FrogBlight, has been identified targeting users primarily in Turkiye.
- Deceptive distribution: The malware spreads through smishing campaigns and fake websites disguised as official government portals for accessing court case files.
- Advanced capabilities: It steals banking credentials and possesses spyware functions to collect SMS messages, contact lists, and file system data.
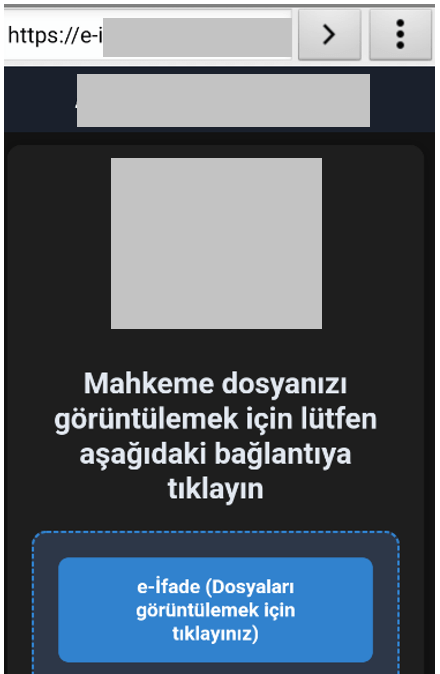
A new and evolving Android banking trojan named FrogBlight has been discovered in a campaign primarily targeting individuals in Turkiye. Initially observed in August 2025, this sophisticated mobile malware is distributed through smishing messages that lure victims with fake court case notifications.
These messages direct users to phishing websites impersonating official government pages, convincing them to download and install the malicious application. Once installed, the malware disguises itself as a legitimate government app or a common browser like Chrome.
Technical Capabilities and Credential Theft
FrogBlight is engineered to steal sensitive financial information with precision, according to the latest report from SecureList by Kaspersky. After a victim grants the necessary permissions, the malware opens a legitimate government portal within a WebView interface.
When the user attempts to sign in via their online banking provider, FrogBlight injects malicious JavaScript code to capture their login credentials. This data is then exfiltrated to a command-and-control (C2) server.
Beyond credential theft, the malware functions as spyware, capable of collecting and sending:
- SMS messages,
- Device information,
- Call logs,
- A list of installed applications.
Ongoing Development and MaaS Potential
The FrogBlight banking malware appears to be under active development, with newer versions incorporating additional features like keylogging, geofencing to avoid specific regions like the U.S., and anti-emulator checks.
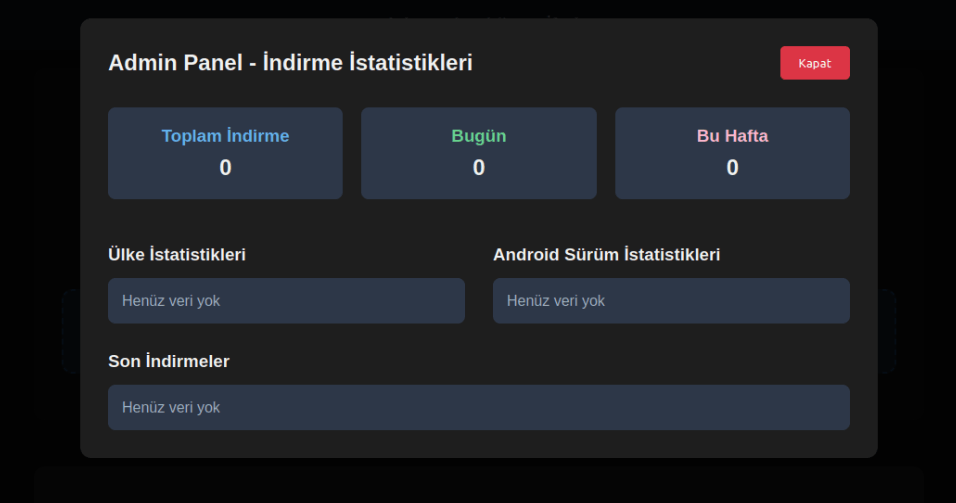
The communication protocol has also evolved from a REST API to WebSockets. The presence of a web panel for managing infected devices suggests that FrogBlight may be distributed under a Malware-as-a-Service (MaaS) model, potentially widening its reach and impact.
In April, a novel, advanced MaaS platform for Android was used in a phishing campaign impersonating banks.
In June, a new zero-day exploit by Stealth Falcon targeted Middle East government and defense entities. October reports noted the Maverick banking trojan was spreading on WhatsApp using worm-like propagation.