DOJ Announces Actions Against Alleged Key Member of Russian Cybercriminal Groups NoName057(16) and CARR (Z-Pentest)
Key Takeaways
- Indictment: A Ukrainian national has been indicted in the U.S. for her alleged role in two Russian-backed cybercriminal groups.
- Targeted groups: The operations targeted the Cyber Army of Russia Reborn (CARR) and NoName057(16), both known for attacking critical infrastructure.
- State sponsorship: U.S. authorities allege both groups were backed by the Russian government, with CARR allegedly funded and directed by Russia's GRU.
The U.S. Department of Justice has announced two indictments against Ukrainian national Victoria Eduardovna Dubranova, 33, who was extradited to the U.S. and is charged for her alleged supporting roles in the CARR and NoName057(16) hacking groups, which have conducted destructive cyberattacks against global targets, including U.S. critical infrastructure.
The indictments detail that Dubranova, also known as Vika, Tory, and SovaSonya, was allegedly involved in conspiracies to damage protected computer systems and tamper with public water systems. If convicted, Dubranova would face a statutory maximum penalty of 27 years in federal prison.
Destructive Attacks on Critical Infrastructure
According to the indictments, both groups operated in support of Russia's geopolitical interests. CARR, also known as Z-Pentest, reportedly founded and directed by Russia's Main Directorate of the General Staff (GRU), claimed responsibility for hundreds of attacks.
These include compromising public drinking water systems across several U.S. states and attacking a meat processing facility in Los Angeles in November 2024, resulting in physical damage and spoilage.
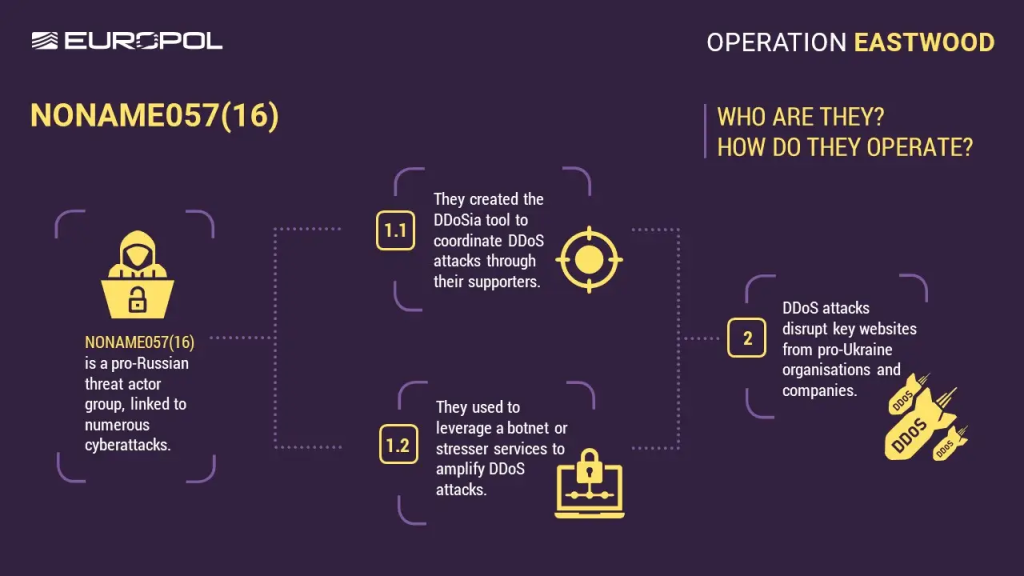
NoName057(16) is described as a state-sanctioned project that developed its own proprietary DDoS tool, "DDoSia," to attack government agencies, financial institutions, and infrastructure like railways and ports.
The group allegedly recruited volunteers and offered cryptocurrency rewards for participation. These operations highlight the tangible cybersecurity threats posed by state-backed hacktivist groups.
The CARR indictment charges Dubranova with:
- one count of conspiracy to damage protected computers and tamper with public water systems,
- one count of damaging protected computers,
- one count of access device fraud,
- one count of aggravated identity theft.
Coordinated Government Response and Rewards
In conjunction with the DOJ cybercrime actions, other U.S. agencies have issued a joint cybersecurity advisory (PDF). This advisory warns that pro-Russia hacktivists are targeting minimally secured systems to infiltrate operational technology within critical infrastructure.
The Department of State has also announced rewards of up to $2 million for information on CARR associates and up to $10 million for information related to NoName057(16).
Earlier this year, NoName and CARR launched a cyber attack on the sewage treatment plants in Poland. NoName057(16) was dismantled in July following an Europol-led crackdown on pro-Russian hacktivists striking NATO allies.
In other recent news, three Ukrainian hackers were arrested in Warsaw on charges of national defense threats.