DeadLock Ransomware Uses New BYOVD Loader Exploiting Driver Vulnerability to Disable EDR
Key Takeaways
- New loader: A previously unknown loader utilizing a BYOVD technique has been identified in recent DeadLock ransomware attacks.
- EDR evasion: The loader exploits a known flaw in a legitimate Baidu Antivirus driver to bypass kernel-level security measures.
- Custom encryption: DeadLock’s custom stream cipher with time-based cryptographic keys encrypts files, avoiding standard Windows cryptographic APIs.
A financially motivated threat actor is deploying the DeadLock ransomware attack using a novel loader that leverages the Bring Your Own Vulnerable Driver (BYOVD) technique to disable endpoint detection and response (EDR) processes.
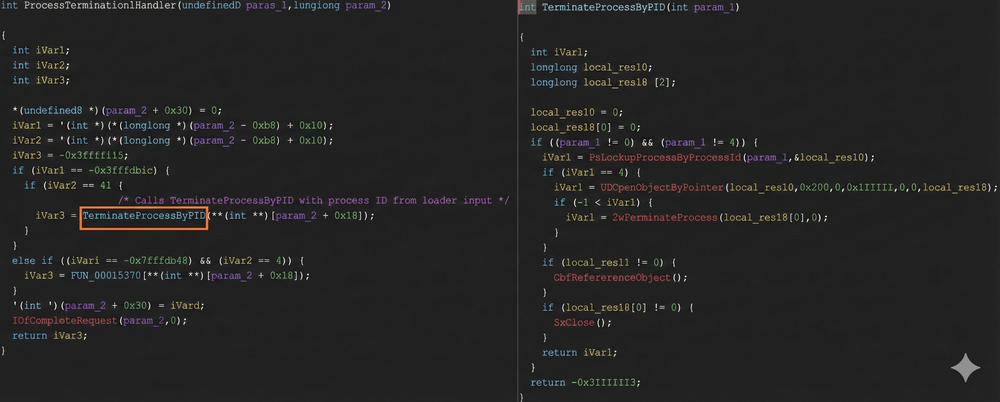
Disguised as "EDRGay.exe," the loader exploits a known Improper Privilege Management flaw (CVE-2024-51324) found in a legitimate Baidu Antivirus driver, "BdApiUtil.sys."
Pre-Encryption Defense Evasion
The loader establishes a connection with the driver and sends a specific IOCTL command to terminate targeted processes.
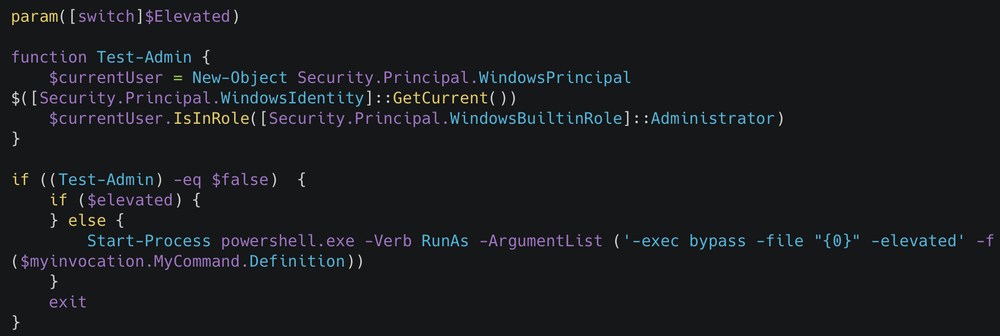
Talos Intelligence security researchers observed that before deploying the ransomware, the threat actor executes a PowerShell script designed to systematically dismantle the system's defenses and inhibit recovery.
The script bypasses User Account Control (UAC), disables Windows Defender, and terminates a comprehensive list of security, backup, and database services.
Crucially, it also executes commands to delete all volume shadow copies, preventing system restoration from backups. This preparation phase highlights the sophisticated, multi-stage nature of modern cybersecurity threats, where actors methodically impair defenses before encryption.
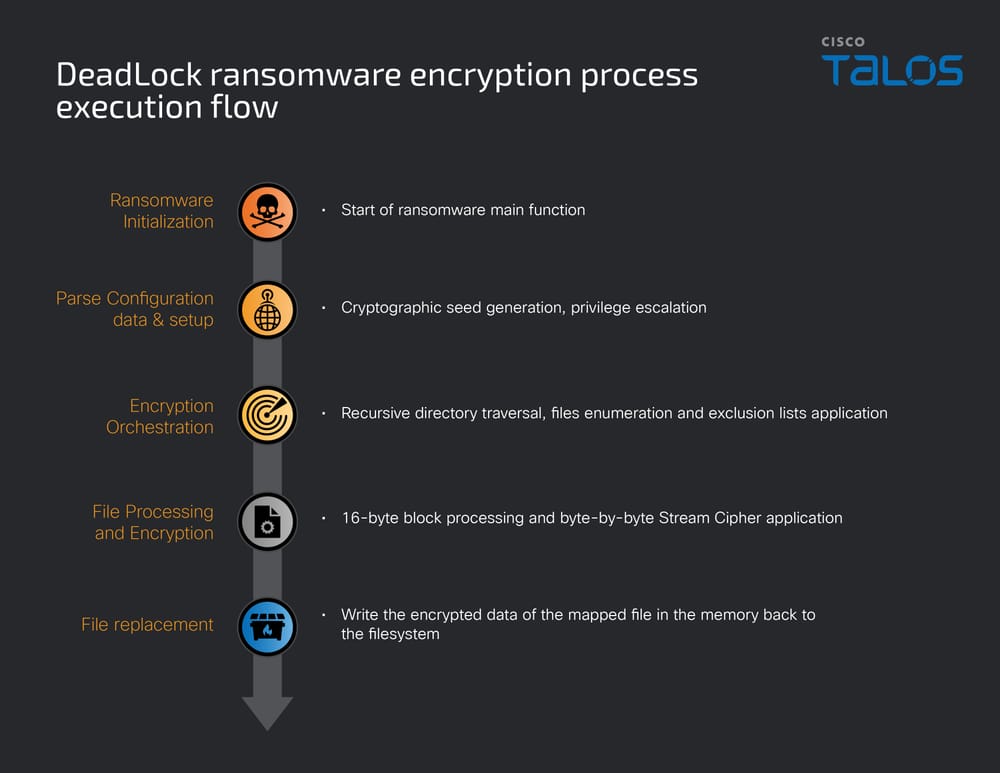
DeadLock Ransomware Encryption Techniques
The final payload, DeadLock ransomware, employs custom ransomware encryption techniques to maximize its impact. The C++-based encryptor uses a custom stream cipher algorithm that generates keys based on system time to avoid detection rather than standard Windows cryptographic APIs.
The ransomware's configuration includes extensive exclusion lists to avoid rendering the system unstable, ensuring the victim can still access the machine to pay the ransom.
After encryption, files are appended with the ".dlock" extension, and a ransom note is dropped in each affected folder, directing victims to make contact via the Session messenger.
The cybercrime world recently saw the Kraken ransomware group emerging with sophisticated tactics from the remnants of the HelloKitty ransomware cartel, and Qilin elevated its attack methods to include leveraging VPN credentials exposed on the dark web.