Critical Vulnerabilities in Connected Car Modems Expose Critical Vehicle Security Risks, Researchers Say
Key Takeaways
- Remote code execution: A critical buffer overflow vulnerability (CVE-2024-39432) in Unisoc modems allows RCE at the data link layer (RLC protocol).
- Protocol stack weakness: The 3G RLC protocol implementation enables attackers to bypass security mechanisms before engaging.
- System-wide compromise: Exploiting the modem can serve as an entry point to compromise the entire SoC, granting access to the vehicle's head unit and Android OS.
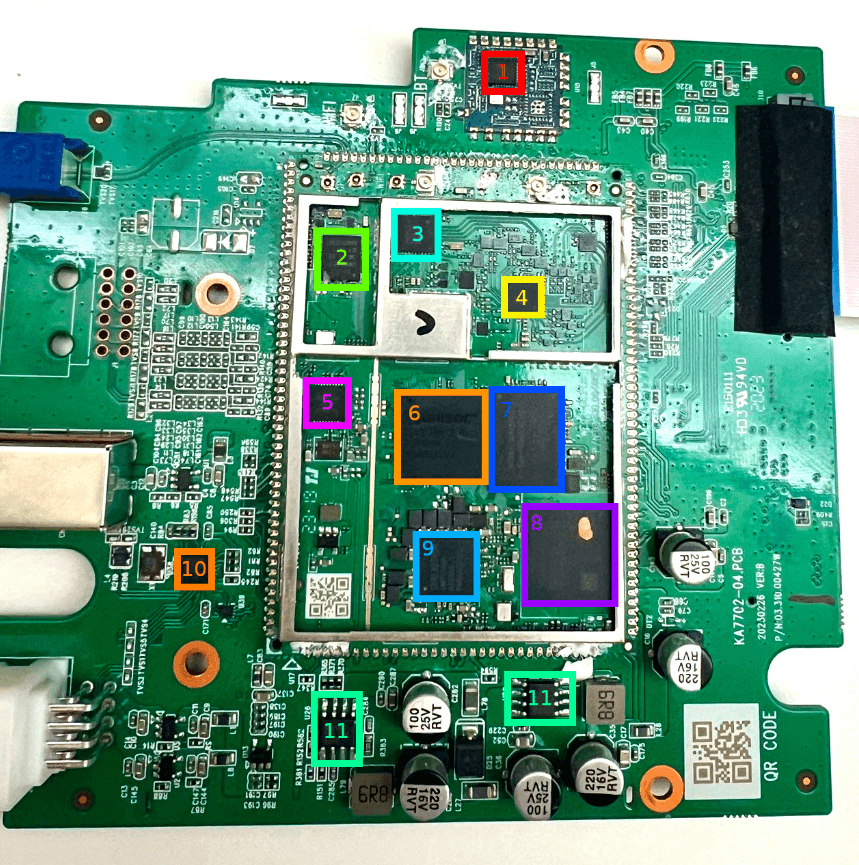
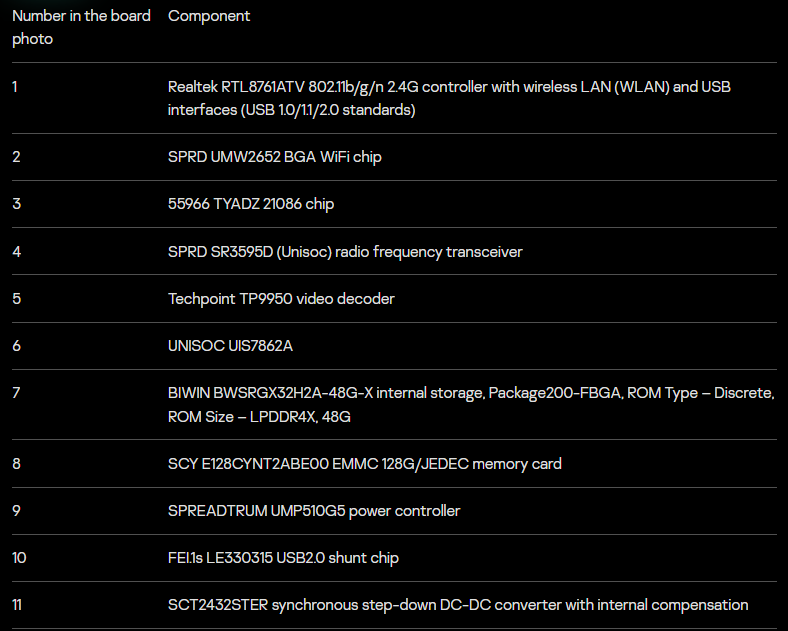
Significant car modem vulnerabilities within the Unisoc UIS7862A System-on-Chip (SoC) modem’s cellular protocol stack, a component frequently integrated into the head units of modern connected vehicles, could compromise entire fleets.
A recent investigation revealed a critical stack-based buffer overflow flaw located within the implementation of the 3G Radio Link Control (RLC) protocol.
Escalation from Modem to System Control
This vulnerability, designated as CVE-2024-39432, allows threat actors to execute arbitrary code remotely on the modem processor by manipulating data packet headers, bypassing established cellular security protocols at the earliest stages of connection establishment.
The implications of these automotive modem exploits extend beyond mere communication disruption, a recent security assessment by SecureList researchers has uncovered.
The research analyzed the head units of modern Chinese vehicles and demonstrated that compromising the modem's Communication Processor (CP) serves as a strategic foothold for lateral movement within the SoC.
Executing code on the modem was an entry point for a complete remote compromise of the entire SoC.
To access the Application Processor (AP), researchers leveraged hardware vulnerabilities, specifically a hidden peripheral Direct Memory Access (DMA) device. This allows attackers to perform lateral movement within the SoC and inject malicious code into the running Android kernel with high-privilege access to the vehicle's head unit.
“Bypassing 3G/LTE security mechanisms is generally considered a purely academic challenge because a secure communication channel is established when a user device (User Equipment, UE) connects to a cellular base station (Evolved Node B, eNB),” researchers said.
“This logic (for example, user applications, browser history, calls, and SMS on a smartphone) resides on the AP and is presumably not accessible from the modem.”
Implications for Connected Car Security
This discovery highlights severe cybersecurity risks in vehicles that rely on integrated SoCs for connectivity and infotainment, as attackers could execute remote code and subsequently control the head unit, potentially displaying arbitrary content or manipulating system functions.
As vehicles increasingly function as IoT devices, the isolation between cellular communication stacks and user-facing application layers remains a critical, yet vulnerable, security boundary that demands rigorous hardening against sophisticated protocol-level attacks.
In another RCE example, a Triofox unauthenticated access flaw was chained with an AV scanning feature abuse to deploy remote access tools last month.
In September, a Stellantis (Chrysler) data breach exposed customer information. Toyota suffered a data breach last year, and Toyota (Kirloskar Motor) was allegedly hit by a Black Nevas ransomware attack in August.