Shanya Packer-as-a-Service (VX Crypt) Fuels Modern Akira, Qilin, Medusa Ransomware Cyberattacks
Key Takeaways
- Emerging cybercrime tool: A new packer-as-a-service, Shanya, has emerged, offering sophisticated obfuscation features to cybercriminals.
- Ransomware adoption: The service is already being utilized by prominent ransomware groups, including Akira, Qilin, and Medusa, to deploy their payloads.
- Advanced evasion tactics: Shanya is used to pack malware, including an EDR killer, which attempts to terminate security products before deploying the final payload.
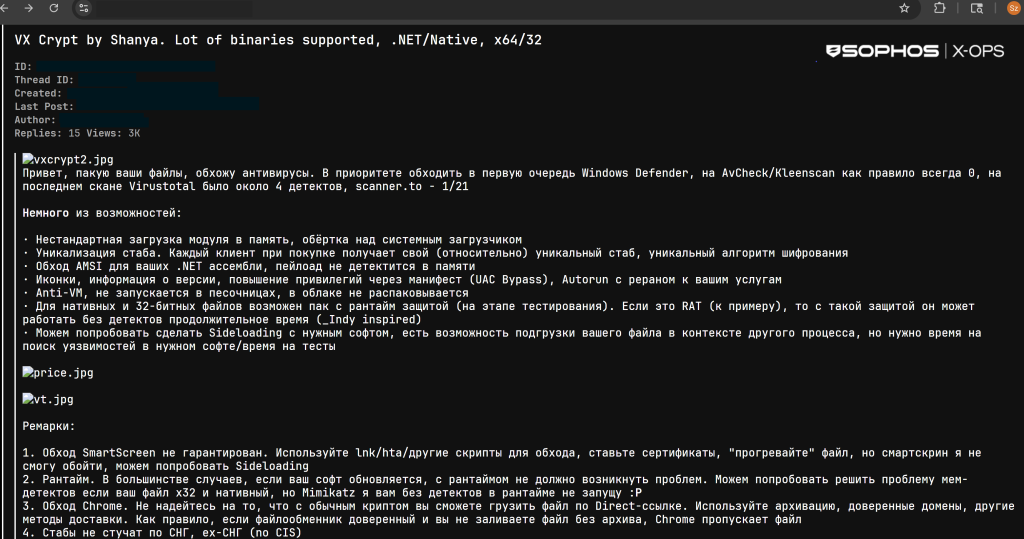
A new and sophisticated Packer-as-a-Service has been identified, providing cybercriminals with advanced tools to conceal malicious payloads and evade security solutions. The Shanya service, also referred to as VX Crypt, offers several capabilities that make it a powerful addition to the growing market of cybercrime tools designed to facilitate complex attacks.
Role in Ransomware and EDR Evasion
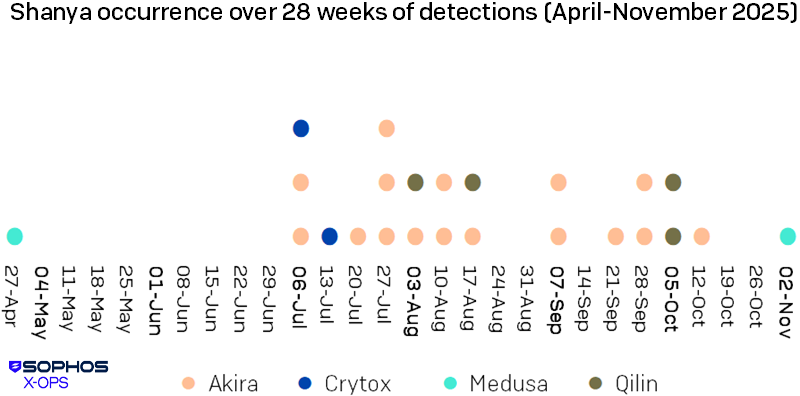
The Shanya packer is gaining traction in ransomware toolkits, having been adopted by multiple notorious ransomware gangs. New Sophos analysis shows it has been used in attacks involving the Akira, Qilin, Crytox, and Medusa ransomware families.
First observed being promoted on underground forums near the end of 2024, it offers features like:
- non-standard module loading,
- unique encryption algorithms for each customer,
- anti-analysis checks to thwart sandboxes and debuggers.
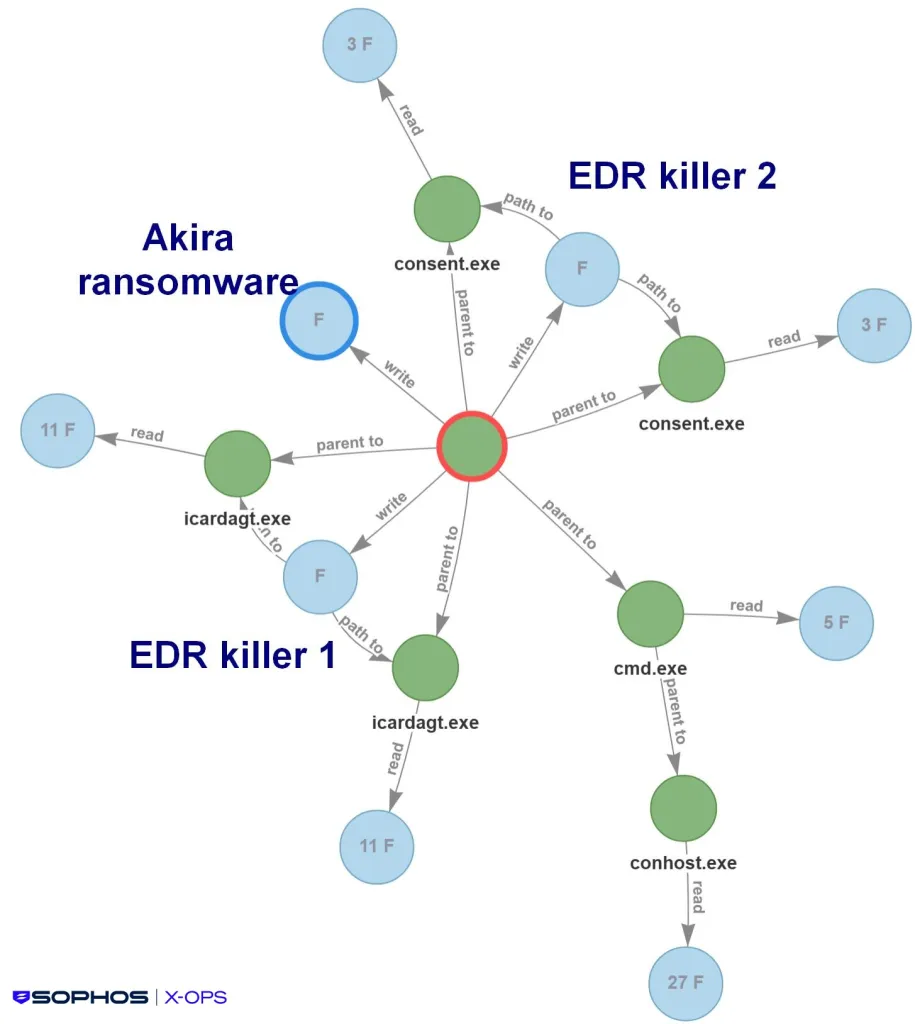
A primary use case for Shanya is to deploy EDR killer malware. This type of payload is designed to terminate the processes and services of security products running on a target system.
By disabling defenses first, attackers clear the path for the execution of their primary ransomware payload, significantly increasing the likelihood of success.
Sophisticated Obfuscation and Delivery Methods
The packer employs highly technical evasion methods, including API hashing, manipulating the Process Environment Block (PEB) to store configuration data, and using DLL side-loading to execute malicious code. The malware often overwrites a legitimate system DLL in memory with the decrypted payload and renames it to further avoid detection.
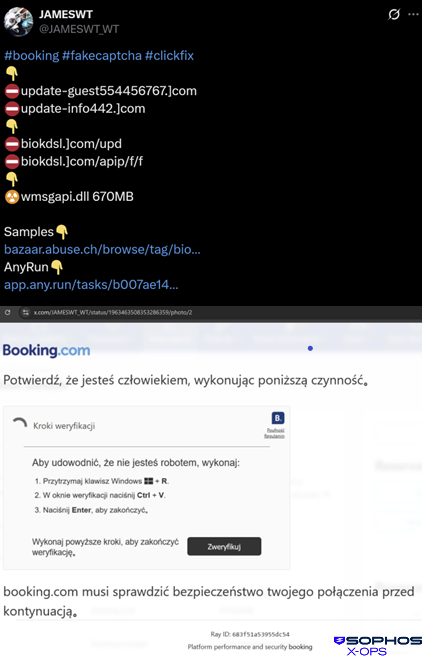
In observed attacks, the packer has been delivered via phishing ClickFix campaigns themed around booking services, using PowerShell scripts to download and execute the payload.
These advanced techniques demonstrate the evolving nature of malware delivery and the continuous challenge for cybersecurity defenses.
This summer, fake Booking.com sites distributed AsyncRAT and a ClickFix attack leveraged email invite lures and spoofed Microsoft Teams login pages. Earlier this year, the EDRKillShifter was used in RansomHub, Play, Medusa, and BianLian Ransomware campaigns.
An October report said Qilin Ransomware's evolving attack methods include leveraging VPN credentials exposed on the Dark Web.