Here Are 3 No-Log VPNs That Shared Data With Governments (Intentionally and Unintentionally)
A lot of VPNs say they don't keep usage or connection logs at all. However, this seems to have become nothing more than just a pretty good selling point nowadays. With this said, we can't help but wonder - how many of them are VPNs that share data with governments?
Well, we looked up over 100 "no-log" VPNs to answer that question for you. Check out this quick article to find out all you need to know.
A Quick Note Before We Start
We are aware that the VPNs we'll be discussing (such as PureVPN and IPVanish) shared user data because they thought it was the right thing to do. And given the context (which we'll discuss a bit later), we can't say we don't understand their reasons.
Plus, they did redeem themselves after the scandals. PureVPN had an independent third-party audit to certify they were a 100% no-log VPN. And IPVanish allegedly had a similar audit too, right before StackPath bought it.
However, false advertising is still false advertising. As a consumer, it's very unpleasant to randomly find out that the VPN you were using for months or years, which you though kept zero logs, actually stored user data. It's the kind of thing that damages the trust put in even the best VPN brands.
Honestly, if they would have been fully transparent about their logging policies, these services could have avoided the scandals they went through.
That's why we decided to write this article. Not to say something negative about these services, but to offer consumers the full picture before they buy a VPN that states it doesn't keep logs.
VPNs That Shared Data With Governments on Purpose
Luckily, there aren't as many of them as you might think. Out of the 100+ VPN services we researched, we only came up with two cases of VPNs sharing user data with the authorities: PureVPN and IPVanish.
PureVPN (Shared Data in 2017)
PureVPN, one of the big players on the global VPN market, was always adamant it kept no logs and respected user privacy.
However, in 2017, we all found out that wasn't the case. Not only did PureVPN actually kept logs, but they also shared the data with the FBI. From what we can tell from the article, PureVPN kept IP logs.
Don't get us wrong - the suspect wasn't innocent at all. He apparently stalked and harassed a woman incessantly. And he used PureVPN to try to mask his online identity.
But here's what we really have a problem with: to us, it looks like the FBI would have caught the suspect even without PureVPN's help. According to the article that we linked to above:
"He made a fundamental error by using a work computer for some of his campaigns, and even though he'd been terminated and the OS reinstalled on the machine, there were footprints left behind for investigators to associate Lin with the 16-month campaign against Smith."
What is also pretty worrying is the fact that PureVPN shared user data with a US agency, even though their HQ is in Hong Kong. So, they didn't have any obligation to give in to the US government's demands.
This wouldn't have looked so bad for PureVPN if they just didn't try to deceive consumers with their fake no-logs policy. Of course, as we said at the start, PureVPN had a third-party audit of their service to prove they really don't keep logs now. But their previous behavior still makes some VPN users wary of their service.
IPVanish (Shared Data in 2016)
Like PureVPN, IPVanish also said they didn't log any user data. And when the Department of Homeland Security sent the company behind the VPN at that time (Highwinds Network Group) a non-legally-binding summons, they said they weren't able to help because they didn't keep logs. At most, they confirmed the IP address associated with the suspect who was a user of this VPN.
That's precisely the kind of answer you'd expect to get from a no-log VPN.
But things got weird fast. According to the court affidavit, Homeland Security got in touch with Highwinds after the response. That's when the company recommended Homeland Security to submit a second summons, requesting more detailed subscriber information.
Well, that's when Highwinds did the complete opposite. They delivered a response with tons of user data.
Besides that, IPVanish offered additional information like the user's IP address. Also, they had logs about connection timestamps - specifically when the suspect used IRC networks.
So, yes, IPVanish lied about not keeping any logs. Obviously, the guy had it coming - he was involved in child pornography, after all.
But again, the company lied to its users.
Today, IPVanish' Privacy Policy says the same thing - that they don't "collect, monitor, or log any traffic or use of its Virtual VPN Network on any platform." And, to be fair, a different company owns them now, so maybe the claim is true.
But there aren't any independent third-party audits of the service to confirm that, so fully trusting this VPN to be "no-logs" is hard for now.
VPNs That Shared Data With Governments Unintentionally
By that, we mean a VPN provider who said it kept no logs ended up sharing user information with the authorities indirectly. Basically, it was out of their control, and they didn't do it on purpose.
It's a pretty interesting story, and the only provider we found to have been a victim of this is EarthVPN.
EarthVPN
The VPN provider said the company keeps zero logs. And their website continues to say the service doesn't store any user data to this day.
However, EarthVPN wasn't aware that their data center apparently kept logs.
Here's what went down - an EarthVPN user made bomb threats, and thought he was anonymous because of the "no-logs" thing. Well, the police managed to quickly find out who he was after seizing the server EarthVPN rented from the data center. Since the data center kept IP transfer logs, the police had the user's real IP address.
Once again, the guy got what he deserved. But this scandal highlights that VPN users aren't the only ones who need to do their research. VPN providers also need to make sure they only work with data centers that have zero logs if they want to advertise themselves as no-log VPNs.
If you want more information about this VPN, here's our EarthVPN review. However, please keep in mind the service no longer works according to user reviews. So, the VPN is pretty much dead - despite the fact that the website is 100% operational.
Do VPNs in 5/9/14 Eyes Countries Automatically Share User Data?
This is a pretty common misconception. Just because a VPN has their HQ in a 5/9/14 Eyes country, this doesn't mean they'll freely give away your data to the authorities. If you're not sure what countries are in 5/9/14 Eyes alliances, here's the full list:
- The US;
- The UK;
- Australia;
- Canada;
- New Zealand;
- Denmark;
- France;
- The Netherlands;
- Norway;
- Belgium;
- Germany;
- Spain;
- Sweden;
- Italy.
Sure, the 5/9/14 Eyes stuff is a privacy concern. After all, the countries in those alliances share intelligence with each other. Also, they spy on each other's citizens.
However, there really isn't any specific law in a 5/9/14 Eyes country that forces VPN providers to store user data. It's up to the provider if they want to keep logs or not.
Of course, governments can take drastic measures - like monitoring the private cables of data centers, for example. But if the VPN provider has regular independent audits of the service to prove it is a legit no-logs VPN, things should be fine.
And don't forget, PureVPN didn't have their HQ in a 5/9/14 Eyes country, and they still shared user data with the FBI.
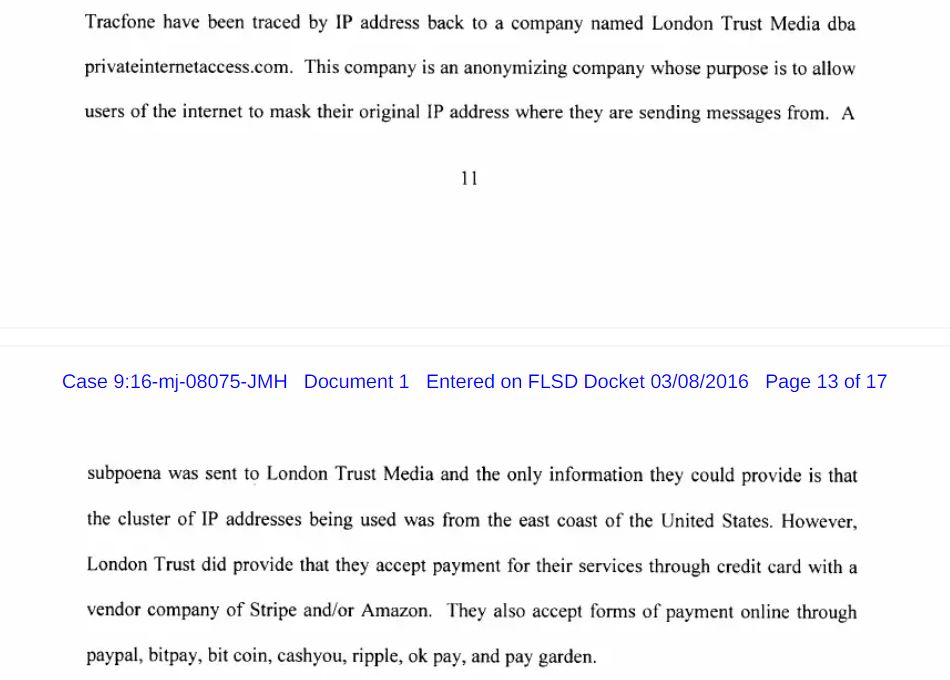
On the other hand, Private Internet Access (a VPN based in the US) was involved in the United States of America vs. Preston Alexander McWaters case. The court documents make it clear the VPN got a subpoena, but they weren't able to provide any user data because they didn't keep logs. The best they could do was confirm their server IP addresses and say what payment options they accept.
Warrant Canaries Would Come in Handy
Whether a VPN keeps or doesn't keep logs, a warrant canary can help build and maintain trust with consumers.
Basically, a warrant canary is a legal statement from the VPN provider which says they haven't received any subpoenas, gag orders, or warrants from government agencies asking them to disclose user information.
In this case, it would normally be a web page on the VPN provider's website that should receive regular updates at specific dates.
Warrant canaries aren't mandatory, but they can help alleviate consumers' fears about VPNs sharing data with governments.
So Which No-Log VPNs Can You Trust?
There are a few providers you can trust that don't store logs. We have a guide on that topic if you want to check it out. We're always monitoring what is happening with those VPNs, and will update the article if one of them shares user data with governments. If you ever have any leads about stuff like that, feel free to message us.
If you're in a hurry, here's the list of no-log VPN services that are reliable at the moment:
- ExpressVPN - They had their server seized by Turkish authorities. They weren't able to find anything, confirming ExpressVPN doesn't keep logs.
- NordVPN - The service suffered a server breach, but there were no activity logs. Also, NordVPN completed an in-depth penetration-testing security audit after the incident. They also started undergoing a second no-logs audit.
- Surfshark - Like ExpressVPN, Surfshark has their HQ in the British Virgin Islands, meaning they don't need to comply with any mandatory data retention laws. Surfshark also makes it clear they keep zero logs in their Privacy Policy.
- CyberGhost - A great VPN that keeps no logs, has favorable jurisdiction (Romania), and their own NoSpy servers that are independently operated by the CyberGhost team.
- VyprVPN - They had an independent company (Leviathan Security Group) perform a no-log audit of their services. The document backs up the no-log claims from VyprVPN.
- PIA - Like we already mentioned, there are legal court documents that prove PIA keeps zero logs.
- ProtonVPN - ProtonVPN made their software open-source so that anyone can inspect it, and also published the results of an independent security audit from Mozilla. And, like VyprVPN, the service is from Switzerland, a country with favorable privacy laws that don't even require VPNs to store connection logs.
The TL;DR Version
Out of 100+ no-log VPNs, we only found instances of two VPNs sharing data with governments on purpose - PureVPN and IPVanish. Besides that, there was also EarthVPN, but they didn't disclose user data intentionally. Instead, they worked with an unreliable data center.
Do you know of other no-log VPNs sharing data with the authorities? Send us a message on social media or leave a comment below. We're looking forward to learning about more cases like this.
As a note, we know that HMA also shared data with the FBI. However, HMA isn't a no-log VPN since they keep connection logs.