When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
5 Eyes, 9 Eyes, and 14 Eyes Alliance
Government surveillance plays a much bigger role in your online life than you might think. The 5 Eyes, 9 Eyes, and 14 Eyes intelligence-sharing networks influence how countries collect data, how they share it with each other, and how much digital privacy you actually get, especially when it comes to your VPN provider’s jurisdiction.
Why does this matter? Because these surveillance agreements can determine whether your online activity, metadata, or personal details end up in international intelligence systems. And if you’re trying to stay private online, knowing which alliance a VPN operates under can make a huge difference in your overall security.
In this guide, you’ll get a clear look at how these intelligence-sharing systems work, which countries pose bigger privacy risks, and how these alliances affect the safety of your VPN and other digital tools. You’ll also learn practical tips to stay secure, including how to choose privacy-focused VPNs, encrypted communication tools, and other strategies to keep your data safe from these far-reaching intelligence networks.
What Are the 5 Eyes, 9 Eyes, and 14 Eyes Alliances?
5 Eyes, 9 Eyes, and 14 Eyes Alliances are international surveillance partnerships where member countries collaborate to collect, monitor, and share intelligence data. This includes online activity, communications, and personal information for national security purposes.
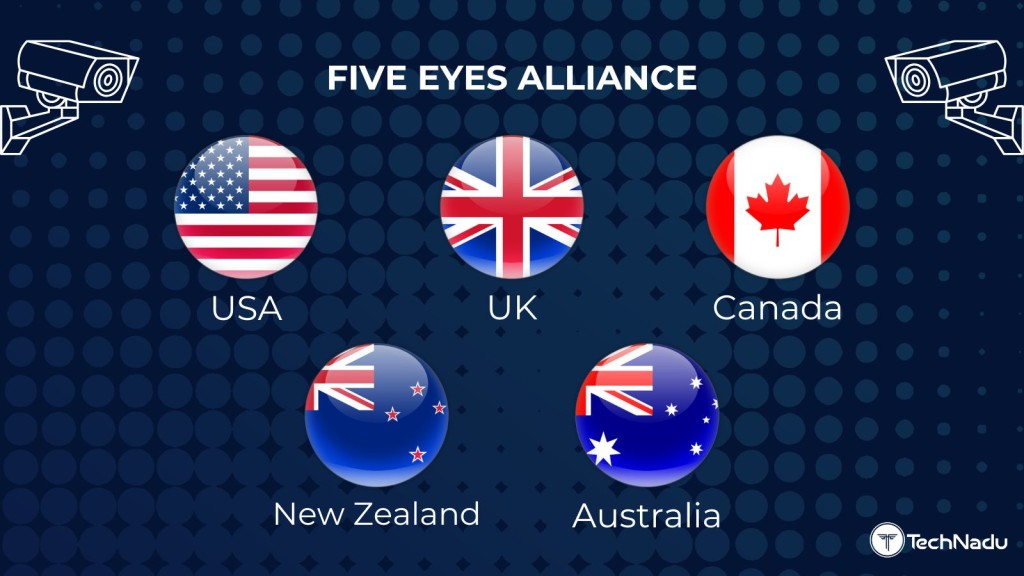
The first of these alliances was the Five Eyes Alliance (also known as FVEY), which was formed shortly after World War II and consisted of Canada, the US, Australia, New Zealand, and the UK. FVEY has always been shrouded in secrecy, and its existence wasn’t made public until 2005.
The original Five Eyes Alliance later expanded into the Nine Eyes Alliance with the addition of France, the Netherlands, Denmark, and Norway. Eventually, the Fourteen Eyes Alliance was formed after five more countries were added, including Belgium, Italy, Spain, Sweden, and Germany.
Today, countries in these alliances collaborate to varying degrees and gather mass surveillance data by tapping key infrastructure. So, what does this mean for you? Well, for example, your Internet service provider continuously logs your activity and allows government agencies to access that data.
Many intelligence alliances are typically based on a barter system. Five Eyes, Nine Eyes, and Fourteen Eyes are unique in that they allow a free flow of information instead of requiring an exchange of data.
What’s concerning is that these alliances are still expanding and could potentially include other countries in the future. Possible candidates include Japan, South Korea, Singapore, and India.
Differences Between the 5 Eyes, 9 Eyes, and 14 Eyes Alliances
Generally, the Five Eyes is considered to be the strongest due to a formal agreement between its members. However, the other alliances also regularly assist with intelligence gathering and sharing. Third-party contributors, consisting of friendly countries, also play a key role in making global mass surveillance possible.
Let us look at the details of each of these alliances and their different third-party contributors.
1. Five Eyes Alliance
The Five Eyes Alliance consists of five countries:
- United States of America
- United Kingdom
- Canada
- New Zealand
- Australia
Countries that are a part of the Five Eyes are under an agreement to share signals intelligence (SIGINT) with each other. This can include communication intelligence (Internet activity, emails, text messages, and phone calls) and electronic intelligence (signals from surface-to-air missile systems and radars).
The original purpose of FVEY was to gather counter-intelligence data against the Soviet Union after the Second World War. However, the alliance’s objectives evolved with a change in the international political landscape and the start of the war on terror.
Today, NSA (in the US) and GCHQ (in the UK) mainly direct their mass surveillance activities toward adversaries like Iran, Russia, and China. The other FVEY countries assist in the surveillance. That said, recent reports say that the US might be excluded from this alliance, due to the country's current position on withholding data from Ukraine.
2. Nine Eyes Alliance
The Nine Eyes Alliance consists of four additional countries on top of the countries present in FVEY:
- France
- Denmark
- Norway
- The Netherlands
The main goal of the Nine Eyes was to further build upon the intelligence-sharing network for national security. The additional countries in this alliance act as third parties and do not have a formal treaty with SIGINT agencies.
Hence, little is known about their official roles in the alliance. However, even though they are third-party participants, it’s important to remember that these countries are not exempt from mass surveillance.
3. Fourteen Eyes Alliance
The Fourteen Eyes further extend upon the Five Eyes and Nine Eyes Alliances by adding additional states collectively known as SIGINT Seniors Europe (SSEUR). This consists of the following countries:
- Germany
- Italy
- Spain
- Belgium
- Sweden
Like the Nine Eyes, the exact details of the agreement between the Fourteen Eyes and Five Eyes are unknown. What we do know is that countries in SSEUR regularly collaborate with FVEY to share and receive intelligence data. However, since they do not have a formal agreement, their level of responsibilities and rights in the alliance is unclear.
4. Third-Party Contributors
Several additional countries are suspected to be third-party contributors to the surveillance conducted by the Fourteen Eyes.
Possible third-party contributors include the NATO countries like:
- Greece
- Romania
- The Baltic States
- Hungary
- Iceland
- Other European nations
Countries that are generally globally allied among each other are also suspected to enable mass surveillance by the Fourteen Eyes. These include:
- South Korea
- Japan
- Singapore
- Israel
The History Behind the 5 Eyes
As previously mentioned, the 5 Eyes is not new, its history dates back to World War II. The alliance has matured over the last few decades, and its focus has constantly shifted from one target to another.
Let’s take a look at the brief history of the 5 Eyes Alliance and see where it stands today:
- In 1946, the United States and the United Kingdom signed an intelligence pact called the UKUSA Agreement. Soon after that, New Zealand, Australia, and Canada also joined, resulting in the birth of the Five Eyes Alliance.
- Members of the Five Eyes worked closely during the Cold War to share and intercept intelligence data on the Soviet Union using the ECHELON surveillance system.
- Overtime, ECHELON evolved, and the focus shifted towards new threats. For instance, it played a significant role in foiling terrorist threats after the 9/11 attacks on the Twin Towers. During the war on terror, ECHELON's main targets were countries like Saudi Arabia, Afghanistan, Iraq, and Syria.
- In the last decade, China has been among the main targets of the surveillance system because of its rising global influence. Five Eyes countries heavily compete with China in trade, manufacturing, and international relations.
- Similarly, in recent times, Russia has once again become a prime focus of surveillance by the Five, Nine, and Fourteen Eyes Alliances after its invasion of Ukraine in 2022.
- Today, countries in these alliances also spy on their own citizens by using each other as proxies to avoid breaking local privacy laws. Edward Snowden's 2013 revelations showed that the British GCHQ and the NSA in the US actively spy on their citizens using unlawful tactics.
Why Do Countries Request Data?
On the surface, they usually say it’s all about national security, keeping people safe, preventing attacks, and maintaining order. But in reality, the reasons go way beyond that, and the scope is much wider than most people think. Let's have a look at them.
What Governments Say They Actually Use Your Data For?
It’s not just one purpose; it’s a whole ecosystem of monitoring and analysis. Here’s how it typically plays out:
- Preventing terrorism and violent extremism: One of the biggest public justifications. They claim these requests help spot dangerous plots before they happen.
- Detecting cybercrime, fraud, and organized crime: Think hacking groups, identity theft rings, drug cartels, money laundering networks, data helps track the digital footprints.
- Tracking foreign intelligence activity: Governments monitor suspected spies or foreign agents by following communication patterns.
- Enforcing political stability or monitoring dissidents: This is where it gets controversial. Some governments keep tabs on activists, journalists, or political opponents.
- Profiling individuals or groups using long-term trends: Over time, data helps governments build patterns: who someone talks to, what topics matter to them, how they behave online.
- Helping allied countries with investigations: Agencies often share information with partner nations, like part of a worldwide surveillance club.
- Building predictive surveillance models: Think: algorithms that try to guess future behavior. It sounds futuristic, but many governments are already doing it.
What Data Do Eyes Alliances Collect?
So, when people talk about the Five Eyes / Nine Eyes / Fourteen Eyes surveillance alliances, it can sound super technical, but the truth is pretty simple: These agencies collect a ton of digital information, much more than most people realize.
And it’s not just about reading messages. A huge part of what they gather is metadata, which is basically the “data about your data.” Here’s what they commonly collect:
- Browsing History: This includes the websites you visit, how long you're there, and sometimes even what pages you click inside the site. It's one of the clearest windows into your interests and habits.
- Search Queries: Whatever you type into Google, Bing, or any search engine can be logged. Searches reveal a lot about someone like fears, plans, health concerns, interests.
- Email Metadata: They don’t always need the content. Knowing who you emailed, when, and how often can map out your entire social network.
- Phone Call Logs: Not the recordings but the logs. Who you called, how long the call lasted, and your approximate location at the time.
- Text Message: Metadata Again, not the message itself (unless specifically intercepted), but who you texted and when.
- Social Media Activity: Likes, follows, log-in locations, account connections, profile history, even if your account is private.
- Location Data: Your phone pings cell towers constantly. Apps and providers also record GPS data. This builds a timeline of where you’ve been.
- IP Logs: Your IP address shows your approximate location and when you came online. It also reveals what services or websites you connected to.
- Device Identifiers: Things like your device ID, MAC address, SIM number, basically the digital fingerprints of your gadgets.
- Video and VoIP Communications: Calls on apps like Skype, WhatsApp, Zoom, and others may have metadata collected (and in some cases, content when legally permitted or indirectly accessed).
When you put all of this together, metadata can create an extremely accurate map of your life,
your routines, relationships, interests, habits, and location patterns, without ever needing to read a single message.
Has Data Actually Been Shared Between Five Eyes Alliance Members?
If you’ve ever wondered whether countries inside the Five Eyes alliance actually share the data they collect, the short answer is: yes and for decades. And honestly, once you dig into it, the scale is way bigger than most people expect.
This isn’t speculation. It’s not conspiracy. It’s documented through:
- official agreements
- leaked documents
- government disclosures
- investigations by journalists and rights groups
Here’s what we know.
- ECHELON (Early Global Surveillance Network) - ECHELON was one of the first big signs that Five Eyes countries weren’t just cooperating, they were actively sharing intercepted communications across borders. It monitored phone calls, faxes, and satellite signals worldwide, and every member country contributed its regional captures to the shared pool.
- Snowden Leaks: Raw Data Exchanged Between NSA and GCHQ - Snowden’s 2013 leaks showed that the NSA (US) and GCHQ (UK) weren’t just passing around cleaned-up reports; they were swapping raw, unfiltered data streams. That includes emails, metadata, browsing logs, and other communications before any filtering or privacy protections were applied.
- PRISM & XKEYSCORE Shared Across Five Eyes - Mass-surveillance tools such as PRISM (which collected data from Google, Microsoft, Facebook, etc.) and XKEYSCORE (which let analysts search global internet activity) weren’t US-only tools. They were made accessible to all Five Eyes members, meaning allied countries could tap into the same data streams collected from major tech platforms.
- Australia Accessed NSA Data and Used It in Reports - Leaked documents revealed that Australia’s intelligence agency (ASD) had direct access to NSA-collected PRISM data, which it used to produce its own intelligence reports. This shows that sharing isn’t one-way. Smaller Five Eyes members also pull from US systems.
- New Zealand Collected Pacific Data and Passed It to NSA - New Zealand’s GCSB gathered large amounts of communications data from Pacific nations, then sent that data to the NSA and other Five Eyes partners. This effectively made New Zealand a regional data collector feeding the bigger system.
- The “Proxy Spying” Loophole Between Allies - Five Eyes members sometimes spy on each other’s citizens and then exchange the data so each country gets access to information it couldn’t legally gather on its own people. For example:
- GCHQ collected data on Americans → gave it to the NSA
- NSA collected data on Brits → handed it to GCHQ
In short, the Five Eyes alliance doesn’t just cooperate. It actively functions as a global data-sharing network where countries exchange massive amounts of intercepted communications, often with few public safeguards. The result is a system where surveillance extends far beyond national borders, and privacy protections can be quietly sidestepped through partner access.
Can a Company Fight Against the 14 Eyes Alliance If It Refuses to Share Data?
If the company operates inside a 5/9/14 Eyes country, it almost never does.
Authorities can issue:
- Legally binding data requests
- Surveillance warrants
- National security letters
- Gag orders that hide the request from the public
- Orders to hand over encryption keys, server images, or metadata logs
Refusal can result in:
- Fines
- Forced shutdown
- Criminal penalties
- Government takeover of servers
This is why many privacy tools operate in jurisdictions like Panama, the British Virgin Islands, Switzerland, or Iceland, where Eyes law enforcement cannot compel data access.
If a company is outside Eyes countries, it is not subject to their legal orders and can refuse. Simple, isn't it?
Can You Remain Anonymous If You Live in a 5, 9, or 14 Eyes Country?
Absolutely. It is possible to stay anonymous in a Five, Nine, or Fourteen Eyes country, but only if you’re intentional about it. Living within these surveillance alliances doesn’t automatically mean you’re exposed; it just means the default settings of your digital life aren’t designed to protect you. The real risk isn’t your physical location, it’s the tools and services you use every day.
Most people lose privacy because they rely on platforms that are legally obligated to cooperate with intelligence-sharing frameworks. For example, U.S.-based services fall under the jurisdiction of the NSA and programs revealed during the Snowden disclosures. If your data is stored in a country with aggressive surveillance laws, it can be accessed regardless of where you live.
That said, strong anonymity is still achievable with the right approach. It just takes discipline.
Do Servers Located Inside Eyes Countries Have to Comply With Data Requests?
Yes, absolutely. The physical location of a server is one of the biggest factors that determines what laws apply, and it has very real consequences for privacy. Even if a VPN or company is based in a privacy-friendly country, the moment one of its servers sits inside the U.S., UK, Australia, Canada, or New Zealand, it falls under the jurisdiction of that local government.
In practical terms, if a server rack is sitting in Virginia, London, Sydney, Toronto, or Auckland, that server must comply with that country’s surveillance laws, including warrants, subpoenas, secrecy orders, and national security letters. This is why many companies openly state in their transparency reports that server location can override the company’s own policies.
Physical Servers (On-Premise or Colocated)
When a company uses a physical, bare-metal server in a Five Eyes country, that server becomes subject to local laws such as:
- the U.S. CLOUD Act, which can force companies to hand over data stored on U.S. soil,
- the UK Investigatory Powers Act (“Snooper’s Charter”), which can require data disclosure and even bulk retention,
- or Australia’s Assistance and Access Act, which allows authorities to demand access or impose technical capability notices.
Because these laws apply to anything physically inside the country, the company’s nationality doesn’t matter. A Swiss, Panamanian, or Cayman-based company still has to comply if its hardware sits inside a Five Eyes jurisdiction.
Virtual or Cloud Servers (AWS, Google Cloud, Azure, etc.)
Cloud servers make this even more complicated. When a company hosts on Amazon Web Services, Google Cloud, Microsoft Azure, or other major providers, those providers can be legally compelled to assist government requests. This can include:
- providing full disk snapshots (server images),
- handing over metadata logs,
- mirroring live traffic,
- or giving administrative access to the machine.
This isn’t theoretical - major cloud providers explicitly state in their terms that they must comply with lawful requests, including those accompanied by secrecy requirements. Cloud hosting also introduces more potential access points since multiple parties (the cloud provider + the company renting the server) have some level of control or visibility.
Before we move onto the next section, let's understand the different between them in short:
How to Protect Yourself from 5 Eyes, 9 Eyes, & 14 Eyes Alliances
Even if local privacy laws in your country protect you, nobody can guarantee that the government is not using foreign agencies or proxies to spy on you. Nowadays, the Internet and social media are a big part of our lives, so online privacy is of prime importance.
Fortunately, there are several safety precautions you can take to avoid the mass surveillance tactics of the 5 Eyes, 9 Eyes, and 14 Eyes Alliances. So, let's discuss each of these methods in detail.
1. Using a VPN
A VPN hides your IP address and protects your online data using various security protocols. VPNs route your Internet traffic through their secure servers and temporarily assign you a different IP address that cannot be tied to you.
But here’s the catch…
Not all VPNs are safe.
Some claim to be “no logs,” but they’ve still handed over user data to authorities in the past, especially when they’re based in countries with heavy surveillance laws.
These cases show one thing clearly:
If a VPN is based in a 14 Eyes country (US, UK, Canada, Australia, etc.), the government can force them to log or hand over information and sometimes silence them with a gag order. So, how do you pick a VPN you can actually trust?
- Pick a VPN outside the 14 Eyes: Countries like Panama, Switzerland, Iceland, and Seychelles have better privacy laws. This makes it harder for governments to demand logs.
- Make sure they’ve had a real “no-logs” audit: A proper audit means an independent company checked their systems and confirmed they don’t store user data. More audits = more trust.
- Choose VPNs that use RAM-only servers: RAM-only (diskless) servers don’t save anything. When the server reboots, everything disappears. This makes it almost impossible for anyone to recover old data.
- See if they’ve passed real-world tests: Marketing claims mean nothing. Real proof means everything. Good signs include:
- A server was seized and investigators found nothing
- The company publicly proved they don’t keep logs
- Real incidents are more trustworthy than ads.
- Avoid VPNs with a history of giving data to authorities: If a VPN has handed over data once, they can do it again, regardless of what they promise.
- Make sure ownership is clear: A trustworthy VPN will openly list:
- who runs it
- who owns it
- where they’re legally based
- If this info is hidden, that’s a red flag. If you need the detailed information regarding the jurisdiction of VPNs and their background, then check our Jurisdiction Sheet. We have already run a thorough background check on more than 40 VPNs.
- Check for basic security features: A safe VPN should always include:
- strong encryption
- kill switch
- DNS leak protection
- secure protocols (WireGuard or OpenVPN
- Obfuscation
- If a VPN lacks these, skip it.
- Read the privacy policy (the real one): It should clearly explain:
- what they log
- what they don’t log
- how long anything is kept
- how they handle legal requests
- If the policy is confusing or vague, walk away.
- Avoid free VPNs: If a VPN is free, your data is the product. Paid services are almost always safer. And you may not believe it, but some VPNs actually cost you even less than a coffee, and that too good ones. We recommend you check out the pricing of all VPNs and then pick the best one as per your needs and budget.
Based on all the features above, we recommend the following top 3 VPNs based on security, jurisdiction, real no-logs audits, speed, transparency, and performance tests:
- NordVPN
- ExpressVPN
- Proton VPN
For full details on why these VPNs rank highest, check our complete guide on the best VPNs that are outside the 14 Eyes Jurisdiction.
2. Using an Anonymous Email and Alias
An anonymous email address or an alias can help you shield your identity on the Internet. Anonymous emails cannot be traced or tied to you. Furthermore, quality anonymous email services encrypt the emails, which means no one can view their content, even if they get intercepted during delivery.
ProtonMail is a popular secure email service that uses end-to-end and open-source encryptions like AES, OpenPGP, and RSA. You can also choose from many other options, such as Mailfence, Tutanota, and CounterMail.
If you are not using an anonymous email service, another good option is to use an alias online, which is essentially an assumed name. However, using an alias is situational and may not be desirable in professional settings.
3. Using a Burner Phone to Register for Services
We highly recommend using a burner phone when registering for non-essential services on the Internet, especially those suspected of logging and/or sharing user data. This helps secure your privacy because the burner number is not related to your identity in any way.
Burner phones also come in handy when purchasing goods from strangers on Facebook or Craigslist. Since you will dispose of the burner number after using it, you will not become the target of scam calls or spam advertisements in the future.
It is not recommended to use a burner phone for essential services that require your phone number as an added security measure because you may lose access to your accounts permanently. This includes services like iCloud, Google, and other similar accounts.
4. Using Encrypted Messaging Services
Standard SMS texting doesn’t use encryption, so it can be monitored by anyone looking to listen in on your private conversations. Encrypted messaging services require encryption keys to read messages’ content, and no one other than the sender and recipient will have this key.
Some messaging services that claim to support end-to-end encryption include WhatsApp, Wickr, and Signal. The most prominent one is WhatsApp, which is owned by Facebook.
From Snowden's leaks, we already know that the NSA has collected communications data from tech companies in the US like Facebook. This means that so-called “encrypted” services like WhatsApp could also potentially leak information. For instance, the FBI was able to recover Signal and WhatsApp data from Trump's attorney's phone in 2018.
5. Using a Privacy-Focused Browser
Using the Tor browser might be your best bet if you want maximum online protection. It is a good choice if you want to avoid fingerprinting on the Internet, as long as you use Tor’s standard settings. If you don’t install add-ons and stick to the default window sizing, it will be nearly impossible for someone to create your digital fingerprint.
Regardless of the browser that you are using, it is essential to follow some good privacy practices, such as:
- Deleting all your saved passwords
- Disabling browser cookies
- Using incognito mode when browsing
- Keeping the browser updated
- Using default settings to avoid fingerprinting
6. Avoiding Sharing Personal Information
This one might seem like a no-brainer, but it is best practice to avoid providing personal information to people or services you do not fully trust.
Using an alias is a good way to hide your actual name in many scenarios. To minimize sharing sensitive data, you can also use throwaway email accounts, assumed addresses, and burner phones when registering for non-essential services.
These methods ensure the safety of your personal information even if the service provider leaks it to government agencies, or in the case of a data breach. Limiting what you share online can keep you safe from stalkers and reduce the risk of getting doxxed, especially on social media platforms and online marketplaces.
VPN Benefits & Drawbacks: Inside vs. Outside Alliances
Final Thoughts
From all the information mentioned above, one thing is for sure - the 5 Eyes, 9 Eyes, and 14 Eyes alliances form one of the most far-reaching surveillance networks in modern history, spanning continents, legal systems, and intelligence agencies. From ECHELON and PRISM to modern metadata harvesting, these alliances operate across borders and often outside public scrutiny, making it difficult for individuals to know when, how, or why their information is being monitored.
The evidence is clear: Countries within these alliances regularly share intelligence, including raw data, and sometimes use each other to bypass domestic privacy laws. Companies operating inside 5/9/14 Eyes jurisdictions can be compelled to hand over user information and physical server location can override even the strongest privacy policies. This reality means that digital privacy isn’t determined only by where you live, but by the services you use and where those services store your data.
Still, privacy is not hopeless or unattainable. Individuals can protect themselves by making deliberate choices: using a trustworthy VPN outside the 14 Eyes (preferably RAM-only - we recommend NordVPN), adopting secure communication tools, relying on anonymous email and burner phones when appropriate, and minimizing the personal information shared online. Tools like Tor, secure email providers, and encrypted messaging services can significantly reduce your exposure, especially when combined with good digital habits.
That’s all we have prepared for this guide. If you have any questions, you can drop a comment below. Thanks for reading!