When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
Warning: 4 Major Threats to Your VPN Security
Yes, a Virtual Private Network (VPN) is a great tool if you want to keep some degree of anonymity in a world of excessive government surveillance - not to mention online data security, when you consider there is a cyber-attack every 39 seconds.
But like everything else in life, VPNs aren’t perfect. In fact, we’ve previously covered what a VPN does not do to make it crystal clear that you’re not getting complete protection just by using one of these tools. There are quite a few things that put your VPN security at risk, and that’s exactly what we’ll be covering today – along with some possible solutions for each threat.
#1 Cookies
These small text files are downloaded to your device when you visit any website and agree to its cookie policy. The most basic information they can contain is the website’s name and your unique visitor ID. Next time you visit a page, these bits of info let the site know you aren’t a new visitor.
For the most part, cookies are harmless files that make your online interactions more convenient. Whether it’s online stores securing your transactions, remembering what you added to your shopping cart, or websites keeping you logged in – this is all made possible by cookies.
Now, these become a privacy problem when they’re used by advertisers to create personalized profiles about you. If you’ve ever seen an ad for sneakers after you’ve googled something related, cookies are to blame. The same applies if you’ve ever bought anything online and then kept getting ads for that specific item on other websites (such as Facebook).
Moreover, government agencies like the NSA can use the data stored in cookies to identify targets for hacking. The Washington Post does mention that this technique “lets NSA home in on someone already under suspicion.” But considering the NSA’s track(ing) record, it’s highly doubtful that they don't use cookie data from advertisers for surveillance purposes.
Needless to say, VPNs can’t protect you from cookies. However, there are quite a few tools at your disposal to deal with them effectively.
The Solution to Cookie Tracking
Cookies downloaded to your device can sit there for years at a time, depending on the expiration period set by the website. The best way to maintain your VPN security, in this case, is simply to delete them. Luckily, it’s nothing complicated – here’s a guide on how to clear your cookies for the most popular browsers.
On the other hand, it can get tiring to keep clearing your cookies every session. Sure, you could use Incognito Mode – meaning cookies are automatically deleted once you close your browser. But then you throw all the convenience of “harmless” cookies out the window:
- You have to log in to your most-used websites every single time you restart your browser. Using YouTube, email, and so on will become a nuisance.
- Know those irritating “Accept our cookies” prompts that you get for every new website you visit? You’ll have to see them again and again. Your privacy may benefit, but it may come at the cost of losing your marbles.
Related: Is Incognito Mode Better Than a VPN? (Not Really – Here’s Exactly Why)
One good alternative is to use a free tool like CCleaner to keep only cookies from your most frequently used websites. It can do so across all your browsers, so you don’t have to manually clear cookies for each one. This way, you can both enhance your privacy and maintain a degree of convenience in your daily browsing. VPN provider CyberGhost has a free Chrome and Firefox extension called Cookie Cleaner you can use as well.
#2 Web Beacons
Also known as web bugs, clear GIFs, or tracking pixels – though that last term gives you the best idea of what web beacons are. They are usually 1x1 transparent GIF files that are embedded in emails or websites. As their name implies, they are used to track your online behavior, generally in conjunction with browser cookies.
Whenever you load up a page, your browser needs to make multiple network requests to download all the images and media files present. This also applies to tracking pixels. The problem with this is that the request to download it also logs details about you, such as:
- Your IP address – a VPN can mask it, but not everything else on this list
- Your activities on the website that contains the beacon
- Whether you’re using a browser or dedicated email client
- The timestamp (and number of times) you accessed the web page or read a tracked email
- Your operating system – especially useful in tracking mobile users
- The screen resolution of your device (PC monitor or mobile screen)
Of course, more complex web beacons exist, such as ones using JavaScript APIs. The most infamous example is Facebook’s Pixel. If you haven't heard, Pixel can be used to track and serve you advertisements even if you don’t have a Facebook account. Belgian courts have deemed it illegal in 2018 and threatened the social media giant with fines of up to $125 million if they continued this practice. All this happened just a few months before the new GDPR rules kicked in.
How to Deal with Web Beacons in Emails
Certain email providers deal with tracking pixels by asking users if they want to load images in emails. For example, ProtonMail uses “This message contains remote content” with a “LOAD” button if you want it to display images or other external content.
Using a privacy-focused email provider like this also ensures you don’t fall victim to a data breach, like 3 billion Yahoo! users did in 2013 and 2014. These were considered some of the worst Internet privacy scandals of the 2010s.
Google, while not privacy-friendly in the slightest, also changed the way its email service works. Images (including any tracking GIFs) are first downloaded to Google’s servers before serving them in your emails. As a result, third-party advertisers are only able to see that Google’s IP address downloaded their tracking pixels. This also means web beacons can’t interact with cookies stored on your device.
How to Deal with Web Beacons in Your Browser
Third parties use tracking pixels for advertising and analytics purposes. If you visit website A, and website B has a beacon on A's page, your browser will send a request to website B to download the pixel. This is simplified, of course – we’d need several different alphabets if we were to list just how many advertisers track you at any given moment.
In any case, the best way to prevent this type of tracking is not to allow third-party content in the first place. You can do so by using a content blocker like uBlock Origin (uBO), and a script-blocker like uMatrix or NoScript for the JavaScript beacons.
Why uBO and not other ad-blockers? Well, a good example is how Adblock Plus allows advertisers to pay them to whitelist their ads and tracking. The extension is basically “Adblock” in name only. uBO creator Raymond Hill has stated that he does not accept donations of any kind, to prevent this exact thing from happening.
One final note. It's recommended that you only use uBO alone and not combine it with other ad-blockers, as they may interfere with each other. Using either uMatrix or NoScript in tandem is fine. Be aware that uMatrix has a bit of a learning curve, but once you use it for a while it becomes second nature.
A Note to Mobile Users
uBlock Origin only works on Firefox for Android. Unfortunately, iOS uses a proprietary extension system that makes add-ons from other platforms incompatible with it. Then again, Apple is ahead of the anti-tracking game, with Safari now blocking third-party tracking and cookies.
At the same time, we feel you should know that Safari is sending browsing data to Tencent – meaning it’s highly likely to end up in the hands of the Chinese government, despite Apple claiming otherwise.
As for Chrome on Android – well, that’s because it has no extension support whatsoever. Moreover, Google’s primary revenue stream comes from advertising. Letting you install an ad-blocker on their own software would significantly cut into their profits, especially when you consider that Chrome has a market share of 62% among mobile browsers.
How to Use uBlock Origin Effectively
After installing uBO, use the following steps to block most tracking pixels and ad trackers in general. What this does is basically activate community-driven filter lists for uBO. The community is quite active, so the lists benefit from frequent updates. Who would have thought that hating ads would bring people together?
Note: The screenshots were taken on Firefox (desktop and Android), but the process is the same in all supported browsers.
Desktop process
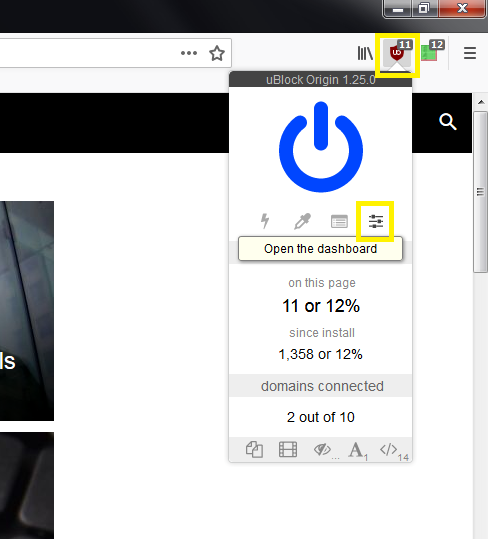
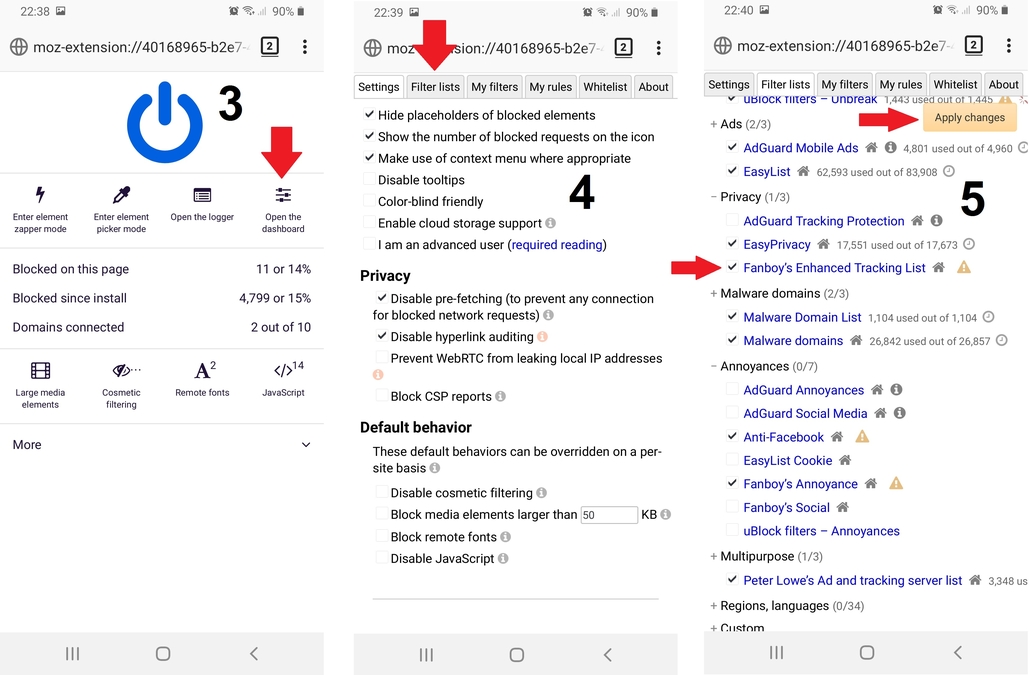
Click on the uBlock Origin icon in the top-right corner of your browser. Then click on the right-most button under the blue power icon.
This will open a new tab containing the uBO dashboard. In this section, click on the "Filter lists" button at the top of the screen.
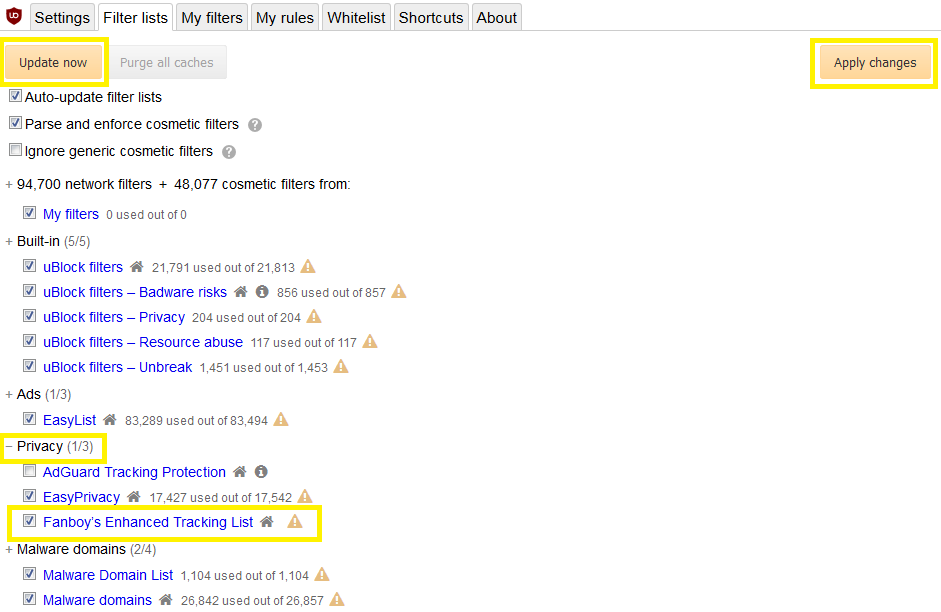
This new section will contain a myriad of filter lists, some activated by default (EasyList, Peter Lowe's Adservers, EasyPrivacy, and Malware domains). What you need to do here is click on "Privacy." This will reveal a few more filter lists.
Check the box to the left of "Fanboy's Enhanced Tracking List," then click "Apply changes" in the top right corner. Finally, click "Update now" at the top left corner to force every list to update with the latest filtering rules implemented by the community.
Mobile process
Activating extra uBO filter lists on Firefox for Android is fairly similar to the desktop version. Here's what you need to do.
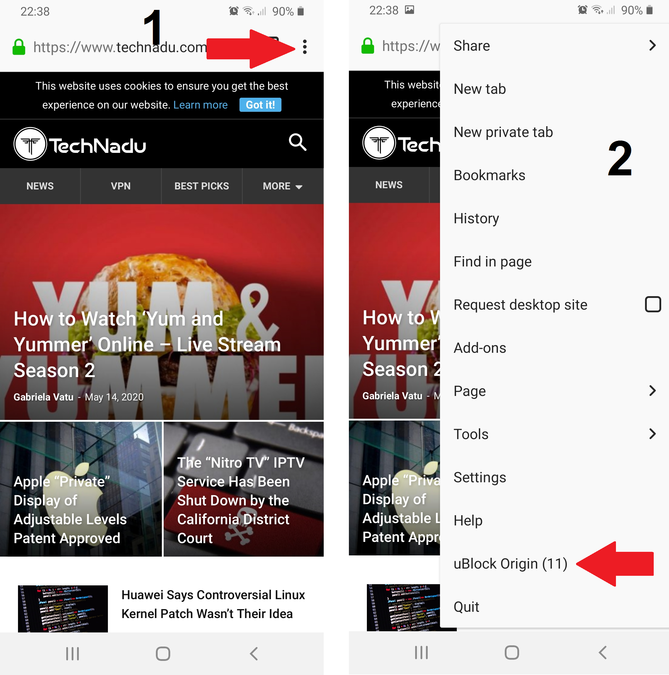
First, tap the three little dots in the top right corner of the screen. This will bring up the Firefox menu. Next, tap on the uBlock Origin button.
These steps will lead you to the uBlock Origin interface. It looks almost the same as the desktop version, though each button has a description underneath.
Anyway, tap on the "Open the dashboard" button. Then tap on these buttons in order: "Filter lists" > "Privacy" > checkbox for "Fanboy's Enhanced Tracking List" > "Apply changes."
That's it! Enjoy browsing without being tracked by over 200 different ad trackers and web beacons at once. Not to mention a cleaner interface for most websites, since there are no intrusive ads plastered everywhere.
Feel free to play around with filter lists as well. The small "home" button at the right of each list takes you to its respective community page, where you can learn more about what it does.
#3 Browser Fingerprinting
Just as all humans have a unique fingerprint, so can browsers provide a fairly unique electronic "fingerprint" to websites that request it. According to the Electronic Frontier Foundation (EFF), your browser could share a fingerprint with as few as 286,777 other browsers.
Considering that by the end of 2018 there were about 20 billion connected devices around the world, 286,777 is a pretty low number to narrow it down to. Sure, it can't point exactly to you, but the data gained from browser fingerprinting can be correlated with other information if somebody really has it out for you.
This is why journalists, whistleblowers, dissenters against oppressive regimes, and other high threat model individuals shouldn't rely solely on VPNs for protection and anonymization.
Other than that, advertisers can target people based on these small clusters of browser fingerprints. They might not be able to advertise specifically to "John Doe from Somewheresville, Wisconsin, age 36" - but they can match him with others based on their shared fingerprint.
Similarly, if you've provided your details to an advertiser in the past (e.g., you've bought something on Amazon or logged into YouTube), they could match your browser fingerprint with your name and shipping address. After all, providers can see what browser you've used when you logged all those details in.
Is All Browser Fingerprinting Bad?
Not exactly. In fact, it's often beneficial because it tells services what version of their website to serve you for full functionality. For example, your browser informs website X that you use Firefox for Android. This allows them to deliver you a mobile version of their website, as opposed to the desktop version.
It's also useful as a protective mechanism for your accounts. Just think of any time you've logged into Google or other services from a device other than your own. You usually get an email asking: "New login detected from [IP address/ location, browser X, Operating System Y] - is this you?" That's an example of positive browser fingerprinting.
What Data Does Browser Fingerprinting Reveal?
One example of a piece of data found in a fingerprinting test is your "WebGL Vendor & Renderer." This shows detailed information about your graphics card. Not only can this be used to identify you if cross-referenced with purchase lists of said card, but advertisers can use this information to market things like better hardware, video games, etc.
Now, this is just a hypothetical scenario. Advertisers and spy agencies analyze unthinkable amounts of data in the fingerprinting process and obviously won't disclose their methods to the competition or potential targets.
What analysts really look at is a combination of all the details found in these types of tests. The details include:
- Your User Agent - which contains your browser name and version, what operating system you use, device type, and other bits of useful information
- Your system language - can be used to narrow down your location, especially if you have it set to something other than English (usually the default language)
- Browser plugins - the more browser extensions you have, the more unique your fingerprint is
- The time zone on your system - the biggest telltale that you're using a VPN to spoof your location. More details at #4 on this list
And much more complex data you can study by using one of these tests:
Source: Pixabay
How to Protect Against Browser Fingerprinting
Unfortunately, you can't fully prevent this process. Smartphones are especially vulnerable since they can be fingerprinted using their internal sensors. Your only recourse, in this case, is to either:
- Not use smartphones, especially if your very livelihood is dependent on absolute privacy
- Use them only for the most basic tasks, while having uBlock Origin installed to prevent ad tracking, and using a VPN
On sensor-less devices, there are two primary methods of spoofing your browser fingerprint.
Install a Virtual Machine (VM)
VMs are basically emulated operating systems (OS) that you can run on your main one. For example, you can run Windows XP within Windows 10 to use old software and play games that are incompatible with today's' OS architecture.
You can even access the Internet through a VM, meaning browser fingerprint tests and other detectors will see that specific OS and settings - as opposed to your primary one. Moreover, VMs are great at isolating threats from your main system. For example, if your VM gets infected with malware, you can simply delete it and create a new one.
A free and open-source VM is Virtual Box, but there are also commercially available ones for more serious and enterprise needs.
Use the Tor Browser
The Tor Browser is basically a version of Firefox that includes all the benefits of script-blocking and anti-tracking discussed so far. Moreover, it has several other protections that work well against browser fingerprinting and enhance your VPN security.
For example, every Tor Browser user appears as if they use Windows 7 as their OS. Moreover, timezone and language preferences are blocked - reducing the chances someone might find your real-life location.
Some say that these settings work in favor of browser fingerprinting, as you are immediately identifiable as a Tor user. That's true, but consider this: in 2019 alone, the number of Tor users spiked at well over 3 million - averaging at about 2 million. That's certainly an improvement over the measly 286,777 number presented by the EFF.
Use All Three Methods in Tandem
Yes, you can combine VPNs, Tor, and Virtual Machines into one full privacy package. Just keep in mind that you should use the default version of the Tor Browser, with no additional extensions. Otherwise, that one minor deviation makes your browser fingerprint "more unique" than the other millions of Tor users.
And now, for the final threat to your VPN security, which was mentioned earlier. We've reserved it for last since it can be an issue even if you're not concerned about browser fingerprinting in general. And nobody would blame you since even security experts consider it kind of a headache to deal with.
#4 Your Local System Time
When you connect to a VPN server in a different country, you basically take on an IP from that country. This can be to your advantage if you want to trick a website or service that you're accessing it from the "correct" region.
However, browser fingerprints contain a browser characteristic called Time Zone. As you may have guessed, the Time Zone variable tells websites your actual local system time. Websites can easily detect that you’re using a VPN or a proxy if the VPN server time and local time are not in sync. Consequently, the service may block you.
This is made worse if you're relying on a VPN to spoof your location for safety reasons. Thankfully, all you need to do is to sync your time zone with the VPN server you're connecting to. Or, you can use the Tor Browser, which completely blocks websites from viewing your timezone preferences.
How to Enhance Your VPN Security - The Bottom Line
As you can see, VPNs need a bit of help to be fully effective. Luckily, it doesn't involve that much work. To recap, all you need to do is:
- Clear your cookies - either manually through your browser, or by using a tool such as CCleaner or the Cookie Cleaner extension. Alternatively, use Incognito Mode.
- Use anti-tracking tools like uBlock Origin, uMatrix, and NoScript - browse the Internet without worrying about ad trackers, beacons, or intrusive advertising.
- Try using Virtual Machines and the Tor Browser along with a VPN for maximum effectiveness against browser fingerprinting.
- Make sure your system time and the VPN server time are in sync so online services don't detect VPN usage.
Do you use any other privacy-focused apps and extensions? Let us know in the comments or on social media!