Malicious Firefox Extensions Found Abusing User Permissions
- Malicious Firefox VPN extension hijacks traffic, injects trackers, and risks user data privacy.
- Eight harmful add-ons identified, including fake games and tools for affiliate fraud.
- VPN Grab A Proxy Free redirects through attacker proxy, weakens HTTPS, and tracks users silently.
A recently uncovered set of malicious Firefox extensions is raising serious concerns about user privacy, with one extension posing as a VPN while secretly hijacking browser traffic and injecting tracking code. The most troubling of the group is “VPN Grab A Proxy Free,” which falsely claims to offer secure browsing but in reality enables full-scale surveillance of users.
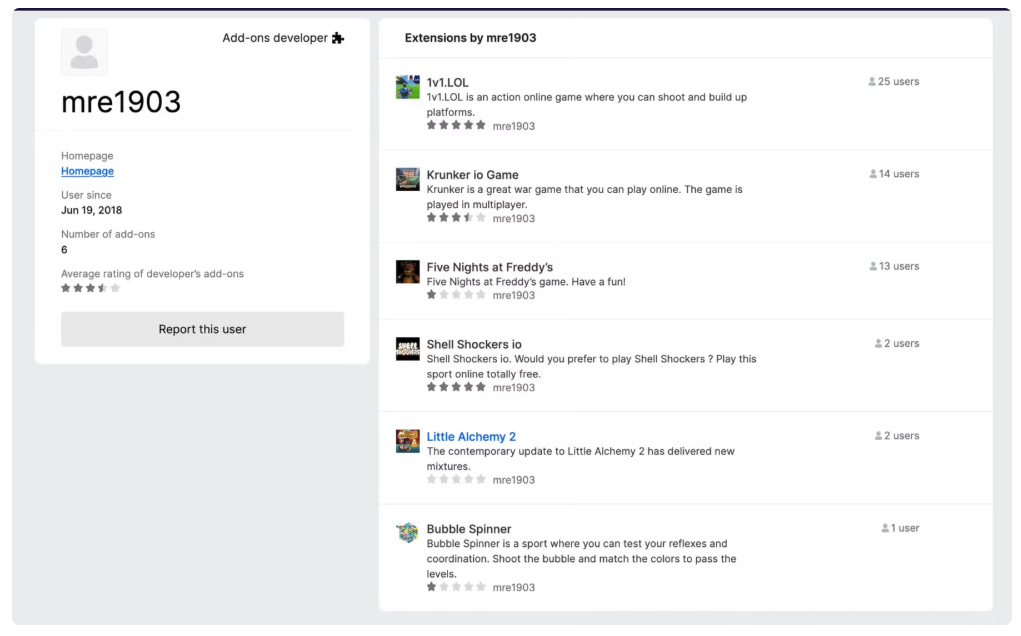
The threat was identified by Socket's Threat Research Team during an investigation into malicious browser activity. While initially investigating Shell Shockers, a fake gaming extension that redirected users to tech support scams, the team uncovered a broader network of malicious add-ons. This includes a mix of extensions operated by a known threat actor, mre1903, and others seemingly involved in affiliate fraud and credential theft.
“VPN Grab A Proxy Free” misleads users by advertising itself as a free VPN. Instead of protecting user traffic, it routes all browsing activity through a proxy controlled by the attacker using chrome.proxy.settings.set() to redirect data through grabaproxy[.]com on port 8080. On top of this, the extension silently injects invisible iframes into every web page. These iframes carry user identifiers, are styled to be completely hidden, and allow the operator to monitor user behavior, from login credentials and private messages to financial data.
By forcing all traffic through HTTP proxies, the extension also downgrades secure HTTPS connections, opening users to man-in-the-middle attacks. This significantly increases the risk of intercepted or manipulated data streams.
The VPN extension is one of eight malicious Firefox add-ons uncovered in the investigation. Other notable examples include:
- CalSyncMaster – a calendar sync tool that exploits Google’s OAuth login flow to steal access tokens, giving attackers long-term access to calendar data.
- GimmeGimme – a fraudulent shopping assistant that hijacks sessions on e-commerce sites like bol.com and coolblue.nl, redirecting users through affiliate links to collect commissions.
A collection of fake gaming extensions masquerading as titles like Krunker.io and Little Alchemy 2. These don’t offer real games and instead redirect users to scam websites, including gambling platforms and scareware pages with fake virus alerts.
The group behind several of these, mre1903, has reportedly been active since 2018. Their known activities date back to 2020 and continue to target Firefox users with increasing sophistication, sometimes using browser APIs like chrome.windows.create() to launch pop-ups during install, making users more vulnerable to scams.
Although Mozilla moderates its Firefox extension store, these findings show that some malicious add-ons are still slipping through. Firefox, popular among privacy-conscious users, is now facing scrutiny over the security of its extension ecosystem.
Experts recommend that users avoid extensions requesting broad permissions or access unrelated to their advertised features. It’s also advised to monitor for sudden proxy changes or unexplained browsing activity after installing new extensions. They recommend users to only use extensions of paid and reliable VPNs, be it for streaming, torrenting or gambling. This way, your data remains safe.