New Mirai Botnet Variant Expands the IoT Targeting Even Further
- A fresh Mirai variant adds nine more exploits in its galore of targeted vulnerabilities.
- The authors of Mirai incorporated some of the flaws mere hours after the details were published.
- Updating your IoT is your best bet, as there are fixes out for every exploit in the bot.
Mirai’s perseverance continues in 2021, as the nasty botnet that has been plaguing IoTs around the globe since 2016 has had yet another target-expanding update. We have seen that happening again and again, with new Mirai botnet variants adding exploits for routers, presentation devices, smart TVs, and video recorders.
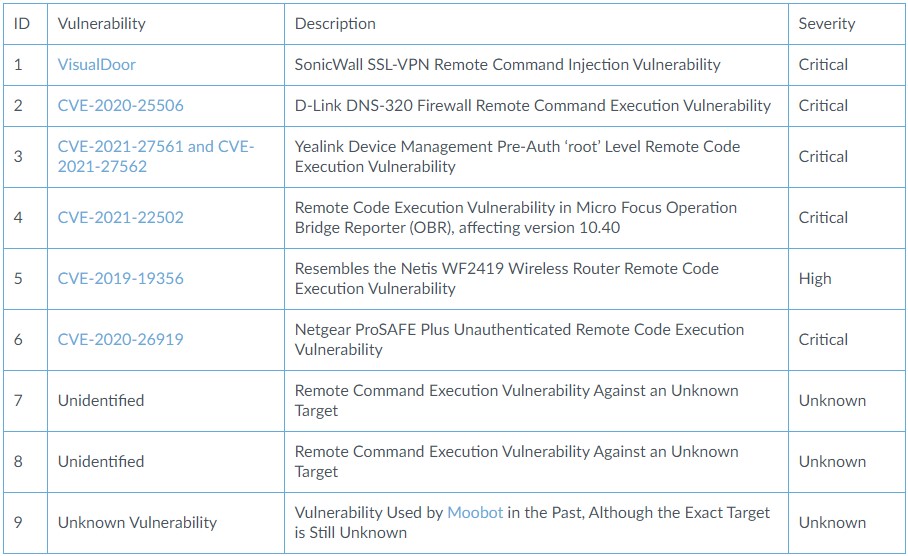
This time, we have a generic expansion into the networking equipment space. Based on the reports of Unit 42 researchers who discovered the new sample last month, the new Mirai variant has added the following exploits:
- VisualDoor (a SonicWall SSL-VPN exploit).
- CVE-2020-25506 (a D-Link DNS-320 firewall exploit).
- CVE-2020-26919 (a Netgear ProSAFE Plus exploit).
- Possibly CVE-2019-19356 (a Netis WF2419 wireless router exploit).
- Three other IoT vulnerabilities yet to be identified.
In some cases, the actors incorporated the exploits mere hours after the associated vulnerabilities had been published, underlining the authors' readiness in a clear way. The focus of the actors is obviously on critical or at least high severity flaws that can trigger remote code execution conditions, so Mirai remains a very dangerous botnet.
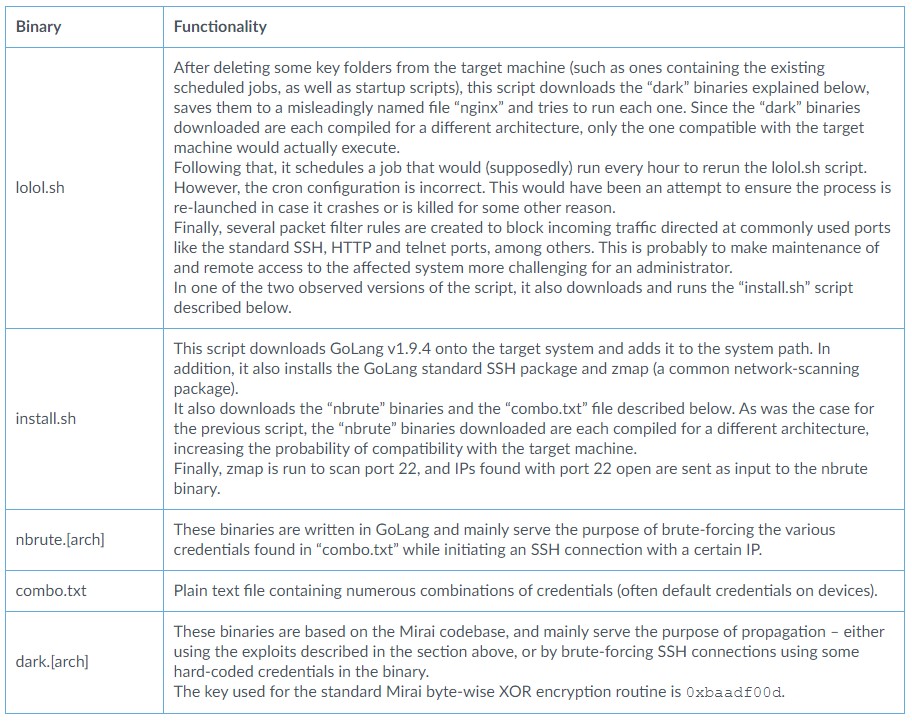
From the point of C2 infrastructure, Unit42 researchers noticed that the actors were changing URLs every week, and each time, the distribution lasted for three days or less. As for the binaries that are fetched from these URLs, these are the following:
To protect your IoTs and by extension yourself against Mirai, apply all available firmware updates on your devices, change the default credentials to something strong and unique, set up a separate network for them and isolate them from your most critical machines, and finally, simply take all IoTs offline when you’re not using them.
There's already a fixing patch available out there for all the vulnerabilities that are being exploited by Mirai right now, so updating your devices should do the trick. Until today, we have seen no Mirai variants incorporating zero-days, which would make the situation a lot different. In any case, the fact that Mirai’s authors are moving instantaneously underlines the need to patch as quickly as possible every time a new update is out.