New “Mirai” Variant Is Exploiting Tenda Router Zero-Days
- New Mirai variant named “Ttint” exploits zero-days that remained unfixed for months now.
- The new malware is very capable, featuring 22 commands that can do a wide range of things to the target systems.
- The Tenda devices that are vulnerable to exploitation are quite popular and used mainly by gamers and home users.
A new Mirai bot variant called “Ttint” is wreaking havoc to Tenda routers by exploiting zero-day flaws in the devices. This new piece of malware is particularly nasty, combining a set of remote access tool features, spyware, and the Mirai-typical “denial of service” capabilities. The RAT alone implements no less than twelve functions triggered remotely and which hackers utilize to tamper with router DNS, set iptables, execute custom system commands, and set up malicious proxies.
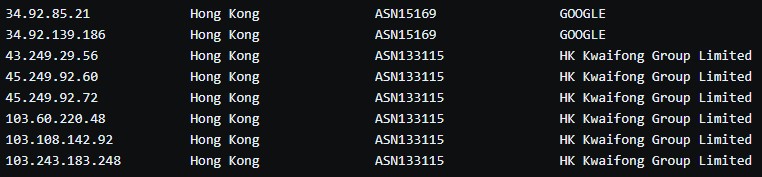
To avoid raising any flags from security products, Ttint passes its C2 communications through encryption tunnels using the WebSocket over TLS protocol. As for the C2 infrastructure itself, the attackers opt for a Google cloud service IP and also a hosting provider in Hong Kong. In general, though, the actors use a rich C2 infrastructure with multiple domain names, IPs, Mirai samples, etc.
The flaws that are exploited by the new Mirai bot are ‘CVE-2018-14558’ and the ‘CVE-2020-10978’. The second vulnerability is a zero-day discovered to be under active exploitation on August 28, 2020. The researchers of the ‘360 Netlab’ have reported it to Tenda with the relevant PoC since then. However, the flaw remains unfixed, and so Ttint is free to continue its malicious spread.
Related: New Mirai Variant Targets CVE-2020-10173 and Other New Flaws
The device that is vulnerable to this is Tenda AC15 AC1900 using firmware version 15.03.05.19. This is a pretty popular product that is promoted as an inexpensive yet high-speed dual-band router that features powerful signal amplifiers and seamless 5GHz connectivity.
Mirai is exploiting this popularity to enable hackers to execute a wide range of commands on the target device. More specifically, there are ten DDoS commands known from previous Mirai variants, and twelve new.
Ttint Bot Commands
One thing that Tenda router users can do is to check for firmware upgrades and apply them immediately. Secondly, they may add the IoCs provided by 360 Netlab manually on a blocklist. If Tenda fails to address the flaw now that the researchers proceeded with its full publication, using a different router model would be a wise thing to do.