Mirai Evolves to Target More Routers and Video Recorders
- A new Mirai variant shows that the development of the dangerous botnet is active.
- The new version combines all exploits that were previously used in individual variants, so it’s more potent than ever.
- The target devices include routers, video recording devices, presentation systems, and various IoTs.
Trend Micro researchers report the discovery of a new Mirai variant that deploys a new set of 13 exploits that enable it to attack more routers as well as other devices with success. While these exploits were individually used in Mirai campaigns before, having them all bundled in one version is a first. Other typical characteristics include DDoS and backdoor capabilities that we have seen before on Mirai, so we’re talking about a variant that is most powerful and dangerous than ever before. The researchers discovered the new Mirai through their honeypots, so it is already out there in the wild.
First, the new variant scans the infected system for specific vulnerabilities in ThinkPHP, Huawei, or Linksys routers. The list of the 13 exploits also includes DVRs, NVRs, D-Link devices, and Netgear devices. The use of three XOR keys to encrypt data is still the preferred way to go for the new Mirai, while the URLs that are used are given specific roles such as “command and control”, “downloader”, and “dropper” links. Apart from managing to spread through the 13 vulnerabilities that constitute its arsenal, the new Mirai also incorporates brute-force capabilities that can be used to allow the malware to gain access to network devices as admin.
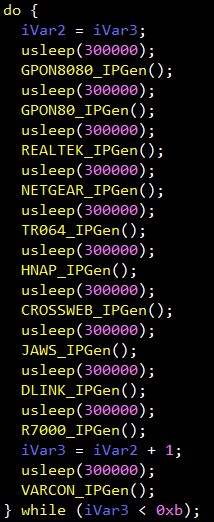
image source: blog.trendmicro.com
Back in March, we saw how Mirai was evolving to target enterprise environment devices such as IoTs, smart TVs, and presentation systems. By compromising these devices, Mirai managed to find its way deeper inside the corporate networks, propagating itself from then on to infiltrate and take over more valuable individual targets. With this latest Mirai variant, it becomes evident that the malware is actively developed and this is not likely to stop any time soon. If you want to stay protected, you should update your router firmware as soon as patches become available, as the exploits that are used by Mirai are known and have already been fixed.
Care to share your thoughts on the above? Feel free to do so in the comments down below, and also on our socials, on Facebook and Twitter.









