CyberGhost VPN Q2 Transparency Report Covers DMCA, Security, Data Requests
- CyberGhost Q2 report shows that it received 97,887 DMCA complaints, but no user data was shared due to no-logs policy.
- Two police requests in May also yielded no data; RAM-only servers retain no user info.
- Bug bounty found 4 valid issues; Q2 saw global phishing, ransomware, and data leak concerns.
CyberGhost VPN has released its quarterly Transparency Report, covering the months of April, May, and June 2025. The report outlines the number of legal data requests the company received, the outcome of its ongoing bug bounty program, and several significant cybersecurity developments that shaped the digital landscape over the past three months.
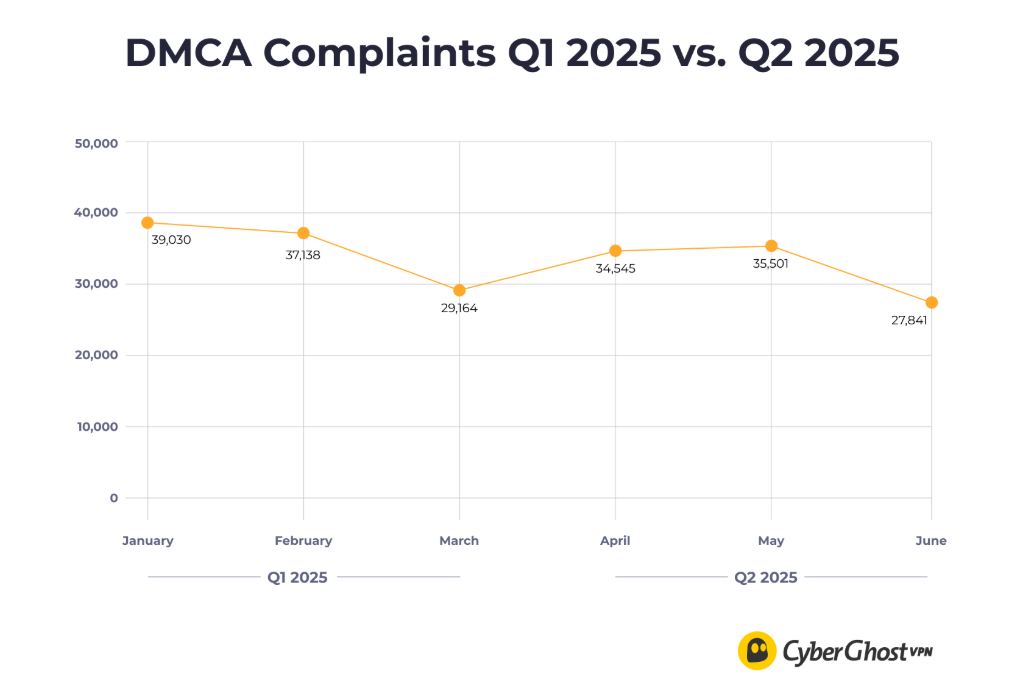
Between April and June, CyberGhost received a total of 97,887 DMCA complaints, slightly fewer than the 105,332 logged in the first quarter report of the year. These notices were submitted by copyright holders claiming that their content was shared without permission using IP addresses associated with CyberGhost’s network.
However, due to the VPN provider’s no-logs policy, it was unable to trace any activity back to individual users. CyberGhost emphasized that it does not collect or store browsing history, connection logs, or any identifiable user information. Its infrastructure is built around RAM-only servers, which reset regularly and leave no data behind.
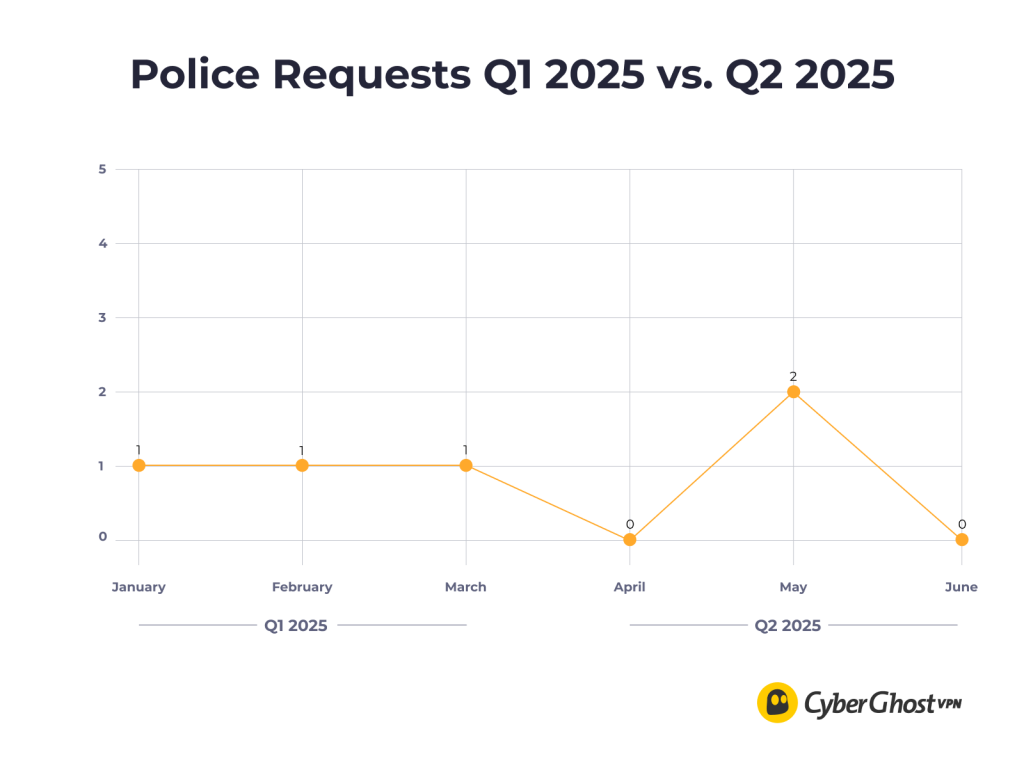
The company also received two police data requests in May. Law enforcement agencies sought user data linked to specific IP addresses involved in unlawful activity. As with the DMCA notices, these requests were declined on the grounds that no user data exists to be handed over. The company reiterated that, even when legally compelled, there would be nothing to provide due to its privacy-first infrastructure and lack of data retention obligations.
CyberGhost’s bug bounty program, which invites security researchers to identify flaws in its systems, yielded 81 submissions in Q2. Of these, 59 were unique and four were confirmed as valid vulnerabilities. The remaining reports were either duplicates, false positives, or edge cases. The company noted that while the majority of submissions don’t result in actionable fixes, the process helps keep its engineering team alert and ensures systems remain under constant review.
The report also provided an overview of global cybersecurity developments during the quarter. In April, a new ransomware group known as Qilin rose to prominence following the sudden disappearance of RansomHub. Qilin was responsible for 74 attacks in a single month, targeting software companies, manufacturers, and critical infrastructure, primarily in the United States. The group employed a strategy of stealing data before encryption, increasing pressure on victims to pay by threatening to leak sensitive information.
June saw widespread media coverage of what was initially reported as a breach exposing 16 billion login credentials. Upon closer inspection, the dataset turned out to be a collection of previously leaked information, compiled from older breaches, infostealer malware logs, and credential-stuffing lists. No new compromises had taken place, and the incident was more of a large-scale indexing event than an actual breach.
Also in June, a phishing campaign exploited user trust in familiar security prompts. The scam mimicked a Cloudflare CAPTCHA page and guided users through a fake verification process using keyboard shortcuts like Win+R, Ctrl+V, and Enter. The clipboard had been preloaded with malicious PowerShell commands, which quietly installed malware such as Stealc, Lumma, or NetSupport Manager. The domain used in the attack was registered in 2006, helping it evade scrutiny from automated threat detection systems.
With this CyberGhost Q2 report, CyberGhost aims to provide transparency around how it handles user data requests and how it responds to security threats. The company maintains that its infrastructure and policies are designed to protect user privacy by default, leaving it with no usable data to share, even when requested.