When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
What Is a Site-to-Site VPN? How Does It Work?
Due to the growing threats of cybercrime, security concerns are shared among all businesses. One of the biggest challenges companies face is maintaining secure communication as they expand to multiple office locations.
This is where site-to-site VPNs come into play. Site-to-site VPNs establish a secure connection between multiple networks. This can be a business with several offices in different locations or a large network of corporate companies that work together.
In this article, you will learn what a site-to-site VPN is, how it works, and the benefits of a site-to-site VPN. After that, we will take you one step ahead and explain what makes it different from remote access VPNs, its limitations, and other types of VPNs.
What Is a Site-to-Site VPN?
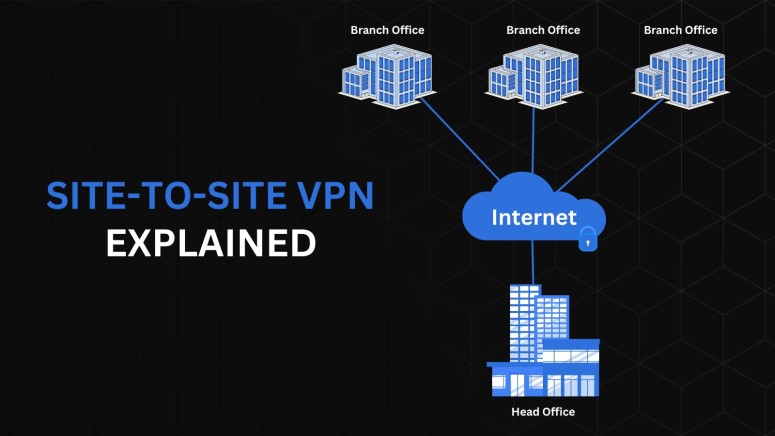
A site-to-site VPN is a technology that securely connects local area networks (LANs) in different locations over the public Internet. This setup is particularly beneficial for businesses or government agencies with multiple offices, allowing employees at different sites to share resources and information securely.
This type of VPN creates a secure, encrypted VPN tunnel between two or more LANs. For instance, consider two offices in different cities. A site-to-site VPN will allow these offices to communicate and share data as if on the same local network.
The data is encrypted at the gateway of one office and sent through the Internet to the gateway of the other office, where it is decrypted. This process ensures that sensitive information remains secure while in transit, making site-to-site VPNs an essential tool for modern, distributed organizations.
How Does a Site-to-Site VPN Work?
A site-to-site VPN works by establishing a VPN connection between local area networks (LANs) in different geographical locations. This ensures that data transmitted between these networks is encrypted and protected from external threats.
The process begins with setting up VPN gateways at each site, typically integrated into Internet routers. These gateways encrypt and decrypt the data transmitted between the networks.
For example, when an office in City A sends data to an office in City B, its gateway encrypts this data before it travels over the public Internet. Upon reaching City B, the gateway decrypts the data, making it accessible to the intended recipient within that LAN.
This encryption is crucial for maintaining data security, especially when sensitive information is involved. As the data travels through the VPN tunnel, it stays unreadable and secure from eavesdroppers and prying eyes. Such security is essential for businesses or government agencies that handle confidential user information.
Moreover, the site-to-site VPN setup does not rely on a client/server model. Hence, employees do not need to install specific VPN apps on their devices. Instead, they can securely access and share resources as long as their devices are connected to the LAN that is part of the site-to-site VPN. This makes site-to-site VPNs a very resource-friendly solution.
What Are the Benefits of a Site-to-Site VPN?
Site-to-site VPNs offer many benefits to organizations with multiple office locations, such as increased data protection, simplified network architecture, easy onboarding, improved resource sharing, and easy access control.
Let’s take a look at each of these benefits in detail.
- Enhanced Data Protection: A site-to-site VPN secures sensitive information and protects its integrity while being transferred between different sites. To do this, it establishes a VPN tunnel, employs robust encryption, and makes data appear as indecipherable code. This way, the data becomes unreadable to attackers.
- Simplified Internal Network Architecture: Site-to-site VPNs make it easy for network administrators to maintain internal IP address configurations across multiple locations. That is because there is no need to convert an internal IP address to an external one when communicating with another site.
- Easier Access Control: Managing access to network resources becomes more straightforward with a site-to-site VPN. Since the VPN distinguishes between internal and external traffic, setting up access control rules is more efficient. This enhances the overall network security.
- Easy Onboarding: The non-client/server model of site-to-site VPNs facilitates easier onboarding of new users and devices. Users can connect to the network without needing specific client software, making the process more user-friendly and less dependent on device compatibility.
- Simplified Resource Sharing: A site-to-site VPN enables seamless resource sharing across different office locations. It creates a unified network environment where employees, regardless of their physical location, can access and share resources as if they were in the same office, fostering better collaboration and productivity.
What Are the Limitations of a Site-to-Site VPN?
Site-to-site VPNs have limitations such as limited scalability, lack of privacy, and inefficient routing. Depending on the network, site-to-site VPN configuration can also be quite complex. Hence, organizations must consider these factors before implementing a site-to-site VPN. Let’s talk about these limitations in detail.
- Limited Scalability: One of the primary limitations of a site-to-site VPN is its scalability. The VPN provides point-to-point connectivity, requiring a unique connection for each pair of connected sites. As the number of sites increases, the complexity and the number of required VPNs grow exponentially, making it less ideal for organizations with a rapidly expanding number of sites.
- Limited Privacy and Security Measures: Although site-to-site VPNs encrypt data in transit, they only protect data as it travels between gateways. The LANs on either side of these gateways may still be vulnerable to cyber threats. Once the data is decrypted and sent to a device within the LAN, it could potentially be exposed, especially if the internal network lacks robust security measures.
- Limited and Inefficient Routing: The architecture of site-to-site VPNs can lead to inefficient routing, especially in networks that use a hub-and-spoke model. In such setups, all traffic passes through the headquarters site for security inspection, which can create network latency and put additional load on the central network, leading to inefficiencies.
- Complex Configuration and Management: Managing and setting up a site-to-site VPN can be quite complex. Each VPN tunnel requires individual configuration, monitoring, and management. This complexity is compounded in more extensive networks with multiple sites, requiring significant resources for proper maintenance and troubleshooting.
Site-to-Site VPN vs. Remote Access VPN: What’s the Difference?
The major difference between a site-to-site VPN and a remote access VPN is that they have different use cases. Furthermore, they are both suitable for different network environments. Let us compare both to understand their difference.
- Site-to-Site VPN: This VPN type connects entire networks to each other. For instance, it links the local area networks (LANs) of two office locations, allowing them to communicate as if they were on the same network. The connection is established through a VPN tunnel, which ensures maximum security with the help of encryption. This allows different offices of an organization to share info securely.
- Remote Access VPN: Unlike site-to-site VPNs, remote access VPNs are designed to connect individual users to a network. This type of VPN is commonly used by remote workers who need to access company resources securely from outside the office. The user installs a VPN client on their device, which encrypts the data before sending it to the VPN server on the company's network. This setup is particularly beneficial for ensuring secure access to company resources from any location.
What Other Types of VPNs Exist?
Apart from site-to-site VPNs, there are other types of VPNs, such as remote access VPNs, intranet site-to-site VPNs, and extranet site-to-site VPNs.
Here’s a detailed overview of each of these VPNs.
- Remote Access VPNs: These VPNs are designed for individual users who need to access a network remotely. Remote access VPNs establish a temporary connection between a user and a central location, typically a data center. This type is widely used by remote workers or employees on the go, providing them with secure access to company resources. The connection usually employs Internet Protocol security (IPsec) to ensure data encryption and security.
- Intranet-Based Site-to-Site VPNs: This type connects multiple local-area networks (LAN) to form a wide-area network (WAN). Intranet-based site-to-site VPNs are used within a single organization to link various office locations, allowing them to share resources securely as if they were in the same physical location. This setup is beneficial for companies with resources and processes distributed across multiple offices.
- Extranet-Based Site-to-Site VPNs: These VPNs are used by multiple organizations that wish to share specific resources while keeping others private. Extranet-based site-to-site VPNs enable different entities to connect to the VPN and selectively share what they choose with each other. This type is ideal for collaborative projects between companies where data sharing is essential but maintaining data privacy is equally crucial.
Final Thoughts
The primary purpose of site-to-site VPNs is to connect multiple sites securely, such as different office locations. Such VPNs don’t require users to install a client on their device, making them very efficient in a business-like organization. They are quite different from remote access VPNs, which are geared towards remote workers and require a client.
That said, organizations must consider certain factors before choosing a site-to-site VPN, such as the encryption level and the provider's trustworthiness. We recommend NordLayer, a network security solutions service by NordVPN, designed to protect in-house and remote employees, control access to company resources, and more.
That’s all from our side regarding site-to-site VPNs and their importance for businesses with multiple locations. If you want to share anything, feel free to comment below.