Unpatched MS Exchange Servers Now Targeted by the ‘Prometei’ Botnet
- Authors of the ‘Prometei’ malware have updated their tool to target unpatched Exchange servers.
- The main goal of the campaigners remains the mining of Monero on very powerful systems.
- The botnet could be set to fetch a nastier payload, so this could turn to become more dangerous.
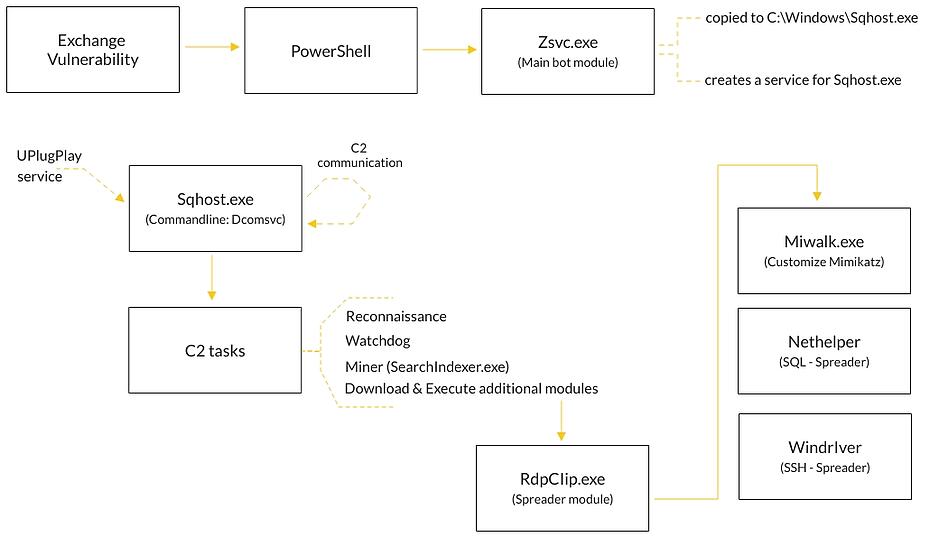
Admins of Microsoft Exchange servers who haven’t applied the fixing patches yet have just got yet another thing to worry about, and it’s a new botnet named ‘Prometei.’ The malware has been spotted on multiple occasions in the wild by the Cybereason Nocturnus Team, and it has been confirmed to target CVE-2021-27065 and CVE-2021-26858, two of the zero-day flaws that Microsoft fixed in early March. Also, these are the same flaws targeted and exploited by ‘DearCry,’ a ransomware strain that was hastily rolled out to attack Exchange servers before they had the chance to patch.
Prometei isn’t a novel malware, though, as there’s evidence that it might have been around since 2016. When it started, Prometei was just another Monero miner. However, its authors are adding more modules onto it, updating it to target whatever is hot in a given period.
The most recent samples make up for a sophisticated and stealthy backdoor that supports a wide range of exploit possibilities. Also, Prometei now supports both Windows and Linux, and it deploys the right payload depending on the detected OS.
While the installation of a Monero miner component to as many endpoints as possible remains central to Prometei, it is just one aspect of the menace.
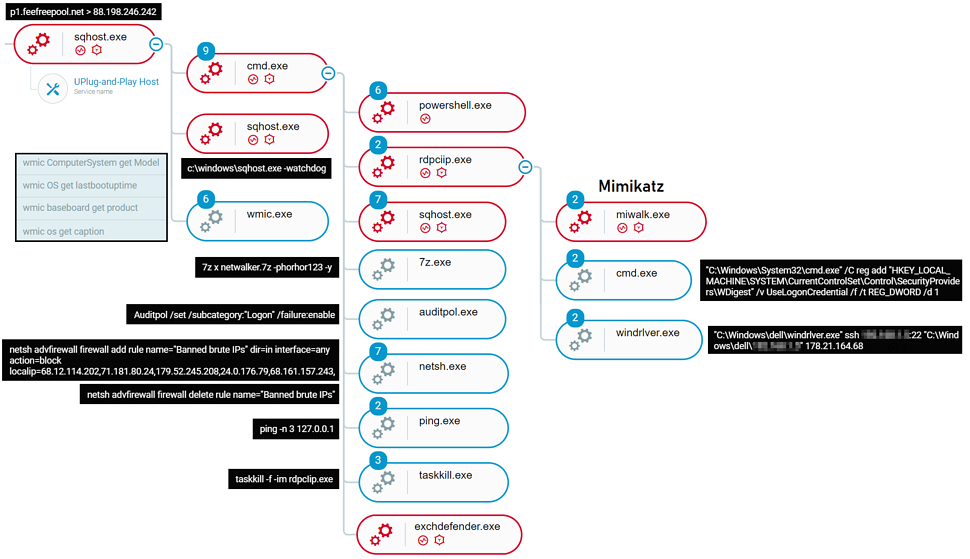
Other things that are happening include the harvesting of credentials, the exploitation of EternalBlue and BlueKeep, the installation and execution of the ‘China Chopper’ web shell, and the fetching of additional payloads and modules. The main bot module, ‘Sqhost.exe,’ supports a wide range of commands, including “stand-alone” native OS commands.
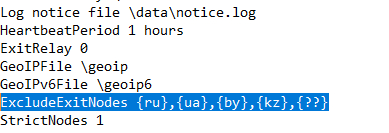
The actors appear to be solely financially motivated, so the full potential of the Prometei botnet is thankfully not harvested. Cybereason found signs of Russian language in the samples it analyzed, while systems based in Russia, Ukraine, Belarus, and Kazakhstan are specifically excluded in the configuration file. In summary, the actors are of Russian descent but aren’t state-supported or interested in espionage.
To conclude, Prometei is another example that highlights how malware authors and lower-level actors, in general, are adopting more sophisticated techniques to spread their malware. In this case, we have a Monero miner that can make significant amounts of money by capturing valuable resources of very capable systems that oftentimes fulfill critical business roles. If the actors wished, though, the damage could be a lot worse, and the adoption of Prometei by a group that has different objectives could take place at any time.