The ‘DearCry’ Ransomware Is a Hastily Built Copy of ‘WannaCry’
- Researchers at Sophos find that ‘DearCry’ is probably just a hasty copy of ‘WannaCry.’
- The ransomware doesn’t use much sophistication, but it remains a serious threat for unpatched systems.
- Microsoft has released a one-click automatic mitigation tool that could help against ‘DearCry.’
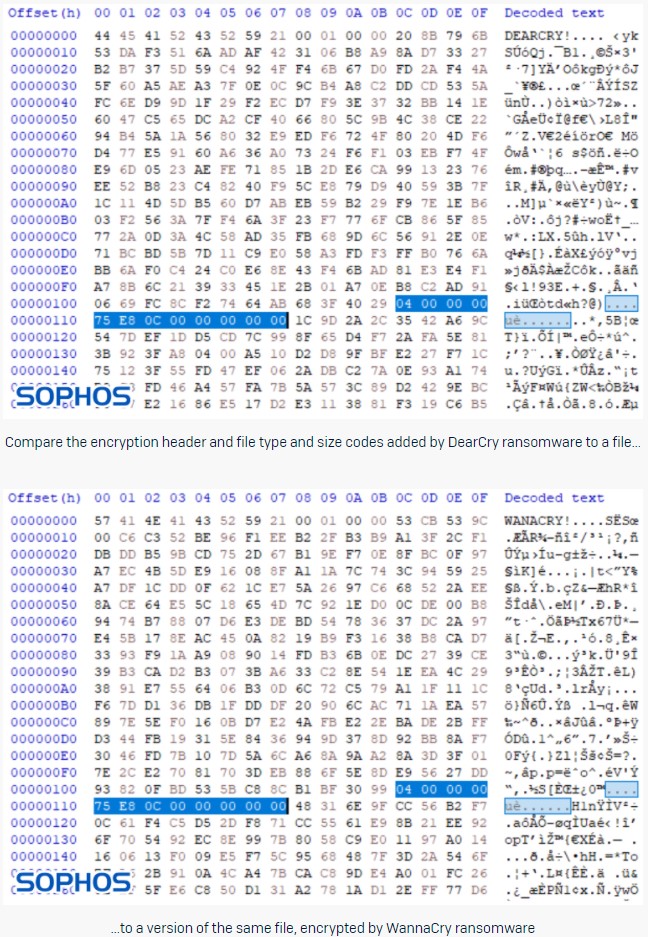
The ‘DearCry’ ransomware that was built specifically to exploit vulnerable Microsoft Exchange servers appears to be the work of an unsophisticated author who just copied stuff from the various WannaCry samples that fly around on the net. It doesn’t feature any hiding capabilities, doesn’t use signed binaries to evade AV detection, is packed with no obfuscation at all, and uses the same encryption headers as WannaCry. All in all, it appears to be a hasty work of a beginner, created to compromise as many Exchange servers as possible before admins have the chance to patch them.
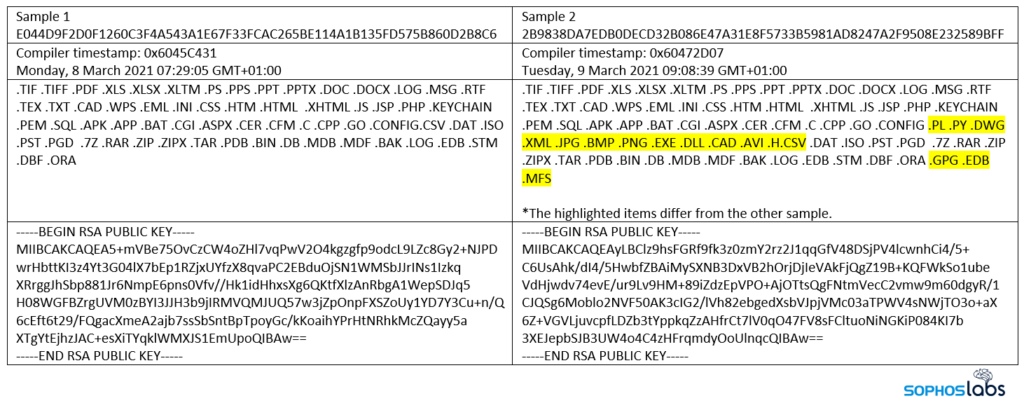
That is according to the analysis of researchers at Sophos, who dived deeper into two samples of ‘DearCry’ found circulating in the wild only last week. Their report explains that detecting and stopping DearCry should be straightforward for most network defense solutions, yet this is not always the case. If the ransomware is allowed to encrypt files, it will do the job by using the AES-256 symmetric encryption algorithm that is embedded in the malware through an OpenSSL library.
Unfortunately, the private key is retained by the attacker, and it’s not embedded in the code, so the threat remains serious, and an infection wouldn’t be easy to deal with. The two samples analyzed were similar but still featured some minor differences in the filetypes that are targeted. Considering that even web shell-related files are targeted, the attackers appear to be more interested in destruction rather than persistent presence on the compromised machines.
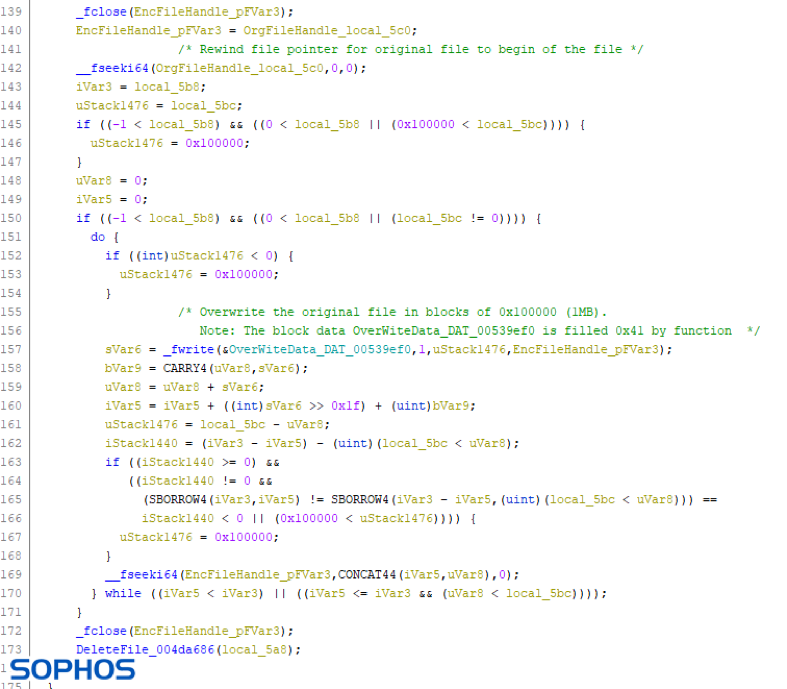
One key aspect of the encryption scheme, which also lets in a ray of hope for the victims, is that DearCry is actually creating copies of the files, encrypting them, and deleting the originals. Because the deletion is geared towards performance, the wiping isn’t definitive, so in some cases, the victims could restore the original and unencrypted files by using data rescue software.
In the meantime, and as Exchange patching continues to be an enormous problem, Microsoft has released a one-click on-premises mitigation tool to help admins who can’t apply security updates still secure their Exchange servers. The tool will automatically mitigate CVE-2021-26855, which is one of the vulnerabilities leveraged by DearCry, together with CVE-2021-27065. This is obviously a temporary solution until patching is possible, but it is highly recommended for those who don’t have IT teams and don’t know what to do.