SonicWall Issues Warning on Fake VPN App Stealing Data Such as User Logins
- Fake SonicWall VPN app steals user logins, risks remote access data exposure.
- Distributed via spoofed websites using SEO tricks and signed fake certificate.
- Modified files collect VPN credentials and send them to a hacker-controlled server.
SonicWall has issued a critical alert about a fake version of its NetExtender VPN client being used by hackers to steal user credentials and VPN configuration data. The malicious software is being spread through fake websites designed to look like SonicWall’s official platforms.
According to SonicWall and Microsoft Threat Intelligence Center (MSTIC), attackers are distributing a trojanized version of the NetExtender SSL VPN client, which is typically used for secure remote access to corporate networks. If compromised, it could expose both employee data and wider business systems.
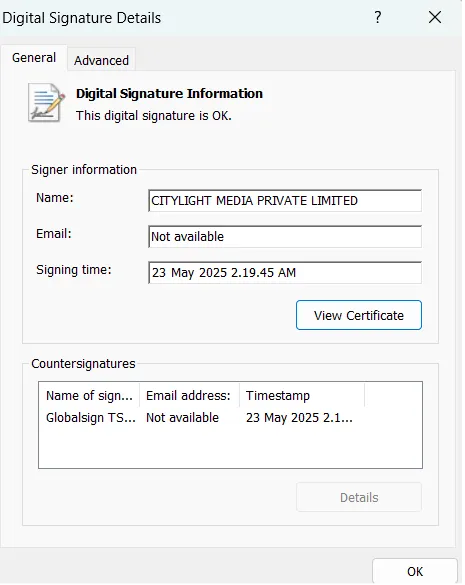
In their investigation, researchers found that the spoofed VPN installer is signed with a certificate under the name "CITYLIGHT MEDIA PRIVATE LIMITED." This gives the malware a false sense of legitimacy that can bypass basic cybersecurity protections.
The attackers reportedly used techniques like SEO poisoning and malvertising to promote the fake website. These methods can trick users into clicking on malicious links that appear at the top of search engine results, especially in sponsored ads, making the threat difficult to detect at first glance.
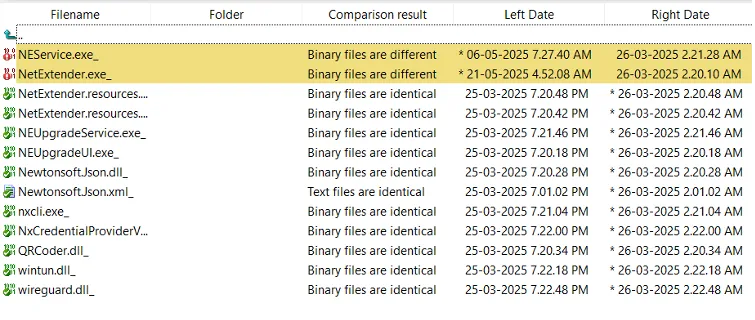
Once installed, the fake VPN client operates like the real one, except it secretly collects sensitive information. Two executable files were altered in this scheme: NEService.exe, which was modified to bypass digital certificate checks, and NetExtender.exe, which was altered to capture login credentials and configuration data.
SonicWall explained that when users enter their VPN login details and hit "connect," the information, including username, password, and domain, is extracted and sent to a remote server controlled by the attackers. Even earlier in February, SonicWall SSL VPN sessions were exposed to hijacking due to a critical vulnerability.
The company strongly urges users to only download its software from official sources: sonicwall.com or mysonicwall.com. Downloading from other sites, especially those found via ads or unfamiliar URLs, carries a high risk of infection.
As of now, both SonicWall’s internal tools and Microsoft’s security platforms are capable of detecting the compromised software. However, many third-party antivirus solutions might not yet be updated to recognize the threat. Under such circumstances, using the best paid VPNs is highly recommended for ultimate security and privacy.
With cybercriminals targeting remote access tools more aggressively, SonicWall recommends users stay vigilant and use trusted antivirus programs to guard against these increasingly sophisticated attacks.