Security Experts Concerned About Weird NordVPN Traffic
- NordVPN is still following weird data communication procedures that experts find hard to explain.
- The official explanation is that it’s all an anti-censorship mechanism to help people bypass blocks.
- Some experts agree that the communication looks odd, but believe it’s innocuous.
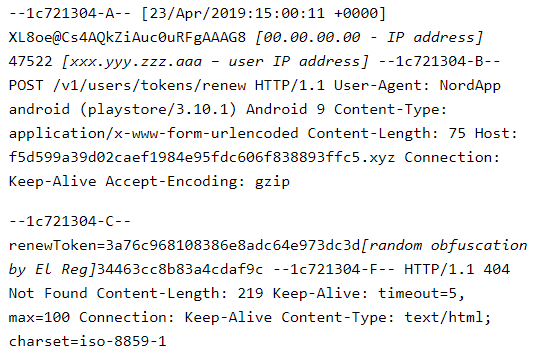
An increasing number of security experts warn that there’s a specific type of traffic deriving from the NordVPN product that looks alarmingly suspicious. What the people who have investigated this to up to a point claim is that the application is contacting three domains that are seemingly “garbage”, owned by no one (until recently), and generally doing what botnet machines that communicate with C&C servers do. NordVPN is outrightly denying that anything shady is going on, and has justified this as being a counter-blocking mechanism. However, this has not been the case until recently.
NordVPN had thanked the first person to disclose this issue to them, Ryan Niemes, giving him three years of free subscription, and acknowledging that this behavior is odd and shouldn’t be there in the first place. However, new reports, as well as confirmation from Niemes, indicate that NordVPN hasn’t changed anything in the weird communication (other than the domains). When reached again by “TheRegister”, NordVPN gave the same explanation about this being a workaround system for people who reside in countries with heavy internet restrictions. They have also added that no sensitive user data is sent in the context of this procedure anyway.
image source: theregister.co.uk
However, in Niemes’ blog post, the traffic that is sent via NordVPN looks quite sensitive, and in addition to that, there’s a clear indication that the client is about to receive a gzip file that could potentially be a malicious file. Whatever this file may be in reality, users should not receive such data as part of the operation of anti-censorship mechanisms. The director of Darktrace, Max Heinemeyer, has also added his two cents on the matter. As he says, the odd domains look like DGA-generated, they use suspicious TLDs (top level domains) that are generally used by botnets, and the VPN communicates with them in the same manner a C&C and malware would do, but it’s all likely to be “keep-alive” traffic. He says they have seen at least 188 cases regarding this matter last year, and NordVPN is not the only VPN product to do this.
Admittedly, things aren’t always what they seem, and a reputable vendor using “smoke and mirrors” for so long would be something too far fetched really. Last year, NordVPN was accused of logging user data, and to ease the public, they hired an independent auditor to check and confirm that they were really not. In our most recent review, we found no evidence of the product risking the user’s privacy or security in any way. That said, NordVPN is still highly recommended by TechNadu, but we’re keeping an eye on how the latest claims unfold, so stay tuned.
What do you think is the case with the NordVPN server communication? Let us know in the comments below, or by leaving your comment on our socials, on Facebook and Twitter.