Kraken Ransomware Group Emerges with Sophisticated Tactics from the Remnants of the HelloKitty Ransomware Cartel
Key Takeaways
- Origins and tactics: Kraken, which emerged in February 2025, is a Russian-speaking double extortion operation linked to the former HelloKitty ransomware cartel.
- Cross-platform capability: Kraken is sophisticated and cross-platform, with distinct encryptors designed for Windows, Linux, and VMware ESXi environments.
- Advanced features: The ransomware includes unique features such as pre-encryption performance benchmarking and establishes persistence using tools like Cloudflared.
The Kraken ransomware group, first observed in February 2025, is a new and sophisticated Russian-speaking threat actor that appears to have emerged from the remnants of the HelloKitty ransomware cartel, as evidenced by references on its data leak site and similarities in ransom note filenames.
The group is opportunistic, targeting a wide range of business verticals and geographies, including the U.S., U.K., and Canada. Victims who refuse to pay are threatened with data publication on Kraken’s leak site.
Analysis of Infection Chain and Tactics
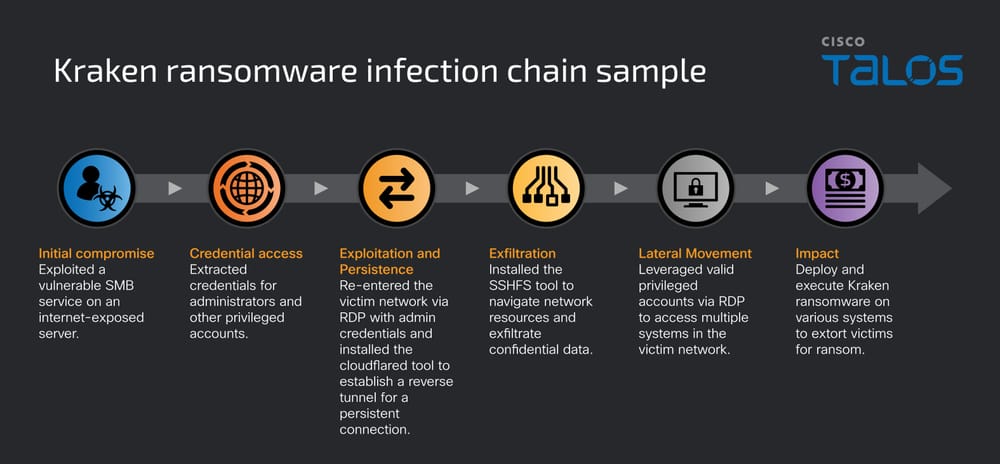
The Kraken group employs a multi-stage attack methodology. A new Cisco Talos cybersecurity report notes that, in one observed incident, initial access was obtained by exploiting a Server Message Block (SMB) vulnerability on an internet-exposed server.
After establishing a foothold, the attackers exfiltrated privileged credentials and used them to re-enter the network via Remote Desktop Protocol (RDP) connections.
Persistence was achieved by installing Cloudflared to create a reverse tunnel, while data was exfiltrated using SSH Filesystem (SSHFS).
The ransomware was then deployed and moved laterally to other systems. This advanced infection chain demonstrates a high level of operational capability.
A Sophisticated Cross-Platform Ransomware Threat
Kraken is a highly sophisticated, cross-platform ransomware with customized encryptors for Windows, Linux, and ESXi systems. It provides extensive command-line options for operational flexibility and uses a combination of RSA-4096 and ChaCha20 encryption.
A notable feature is its ability to benchmark a victim's machine to optimize the encryption process for speed and evasion.
This HelloKitty ransomware link and the group's advanced technical capabilities, including its creation of a new underground forum called "The Last Haven Board," signal a significant and evolving threat to enterprise environments. A few years ago, it claimed the compromise of CD Projekt, the maker of Cyberpunk 2077 and The Witcher.