How the ‘HelloKitty’ Ransomware Manages to Succeed Even If It Lacks Sophistication
- "HelloKitty" is a ransomware strain that has achieved success without doing any of the “extras” of its counterparts.
- The particular strain is using strong encryption, specific targeting, and simplistic threat methods.
- Its authors haven’t even bothered to hide the termination of running processes, maybe because it’s not needed.
In this day and age, almost all ransomware families and RaaS platforms rely on double-extortion techniques like leaking stolen data on dedicated dark web portals or even threatening to keep on DDoSing their victims until they meet the ransom payment demands. However, one strain keeps things simple and straight-forward, reminding everyone what ransomware is all about, which is encryption. HelloKitty is a relatively new ransomware that doesn’t do any of the additional trickery, yet it still manages to bring down notable targets.
Most recently, the group compromised CD Projekt, the maker of "Cyberpunk 2077," stealing the source code of several released and also unreleased games and then allegedly selling them privately to secret buyers for a million USD. Researchers from the Sentinel Labs have taken a deeper look into how HelloKitty achieves success without having to overdo it with contrivance and sideline threats.
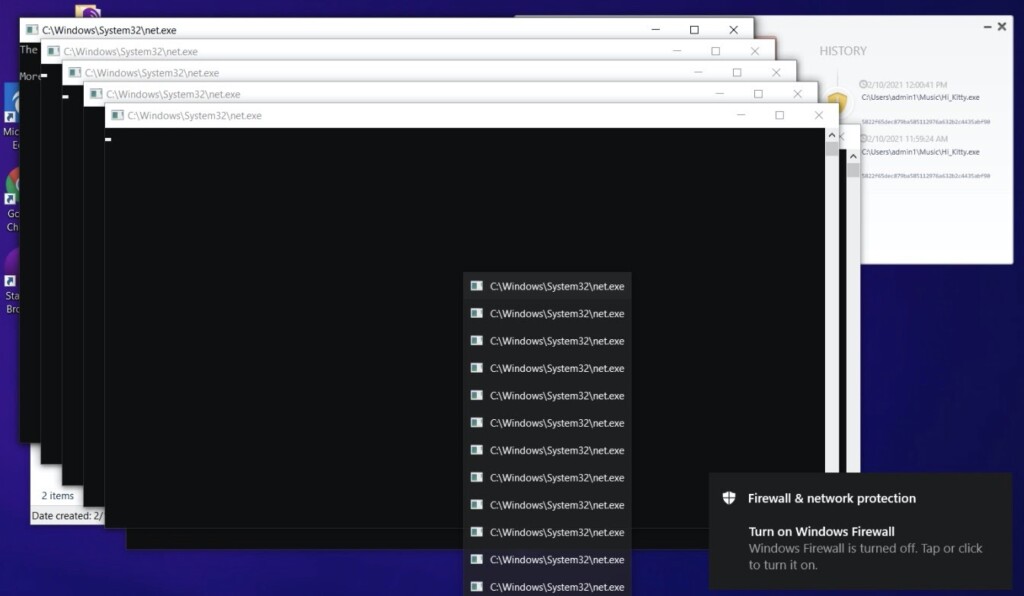
First of all, the delivery of HelloKitty payloads appears to be happening via a phishing email, but secondary infections in conjunction with other malware are also possible. The ransomware terminates all processes that would threaten to interfere with its malicious operations, like protection tools or resource-hogging services.
This is done pretty openly, as the CMD windows that are performing the killing tasks are presented in the foreground, making the infection pretty obvious to the victim. Because HelloKitty does everything quickly, and because it utilizes multiple services simultaneously to gather information about running processes and kill them, the user is left without much margin and also the capability to react to what’s happening.
On the encryption side, HelloKitty uses a combination of AES-256 and RSA-2048, and sometimes even NTRU+AES-128 (depends on the specific variant). The encryption scheme doesn’t have any flaws, at least none discovered yet, so there’s no free decrypter for it.
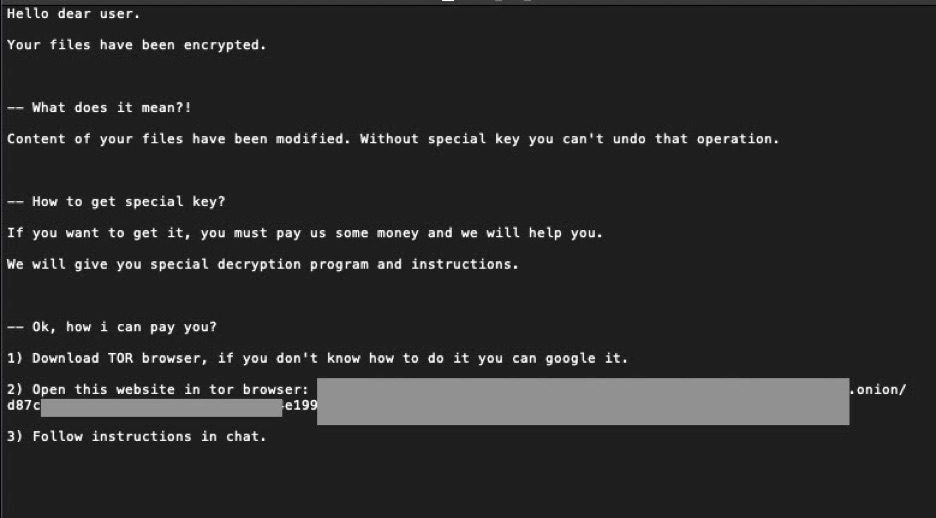
And finally, the ransom note is almost always tailored to the victim, indicative of specific and careful targeting, instructing them to visit a TOR-based portal where they can receive “step by step” support in paying the ransom. HelloKitty is often changing the onion address it uses for this purpose, so there’s no stable portal where anything gets published or announced.
All in all, this is a “back to basics” ransomware that reminds us what made this special category of malware so successful in the first place. HelloKitty proves that if the core functions of a ransomware strain are strong, it can have a successful operation even if there are no extras or any sophistication otherwise.