Keybase Review – A Unique Yet Highly Complex Privacy & Security Solution!
We don’t have to tell you that we live in a rapidly-evolving digital world. Each day, we get to hear about new digital services promising to improve and simplify our lifestyle. However, we also get to hear about exposed PII data, millions of leaked credentials and hacked social media accounts. Therefore, it’s not surprising that many are looking for a way to secure their digital identities, safeguard their private communication, and anonymize their file sharing. Even though we have numerous digital services for each of those individual needs, we also have something called Keybase. This is an all-in-one encryption tool for “things that matter” – as its official website says. However, what exactly is Keybase? What can you do with it? What kinds of data can it protect? Don’t worry, we’ll answer all those questions. So, we wish you a warm welcome to our Keybase review!
Before we go beyond this application’s surface, let’s first introduce you to Keybase. Via the following table, you’ll get to learn some of the basics about this digital tool.
When doing reviews, just like this one, we like to dive deep. This means that we tend to inspect various aspects of any software, which translates to lengthy reviews. In case you only want the highlights, you’ll find those in the following table.
Finally, we’ve reached the end of our introductory segment. Make sure to keep on reading and join us as we explore everything that Keybase offers. So, let’s begin, shall we?
Keybase – TechNadu’s Hands-On Review
We need to tell you that we’ve tested Keybase on a macOS computer and an iPhone. However, everything said below also applies to other versions of this application – for other platforms.
Background, Jurisdiction & Reputation
There’s no reason not to trust Keybase – however, we don’t like the fact that the company behind this product is somewhat shrouded in mystery. However, it’s been around for several years now, without any worrisome data leaks. Our Score: 8/10.
Let’s start with the basics. Since Keybase is all about encryption and privacy, it’s crucial to know more about its country of origin, the company behind Keybase, and everything there’s to know about the application’s development path.
Jurisdiction & Applicable Laws
One thing is certain – Keybase is a secretive company. Perhaps this is imperative in this case, as we’re talking about an ultra-secure solution designed to grand you the ultimate privacy of your communications and files. However, we believe that in order to build some trust, a company such as Keybase should be more transparent.
Upon trying to find more information about Keybase, we found that its HQ is in New York – however, this information can’t be verified. In terms of its industry, it belongs to the ‘Information Technology and Services’ category and has between 51 to 200 employees. There’s very little information about Keybase on LinkedIn and strangely enough, there’s no information about the company in Bloomberg’s database. Among other useful information, some of the co-founders of this company are Chris Coyne and Maxwell Krohn (the provided links will take you to these individuals’ Keybase profiles), previously involved with OkCupid.
It would be also interesting to note that Keybase has managed to raise $10.8 million via a Series A investment led by Andreessen Horowitz. However, we didn’t get to hear anything related to additional investments or the company’s performance since (and the initial investment happened in 2015).
So, should you trust this company with your personal information? Well, at the moment – there’s no reason for us to tell you otherwise. However, we’re not huge fans of Keybase’s secrecy, and with this said – we do recommend exercising caution.
Previous Data Leaks
You should know that there are no reports indicating that Keybase and its servers were ever breached. However, there was a problematic situation back in 2017 related to the application’s bug on Android.
More precisely, users of this application were notified that their private keys might have been uploaded to Google’s servers via automatic backups. This was a highly worrisome situation, as public keys are used to encrypt conversations and other private data. Once the bug was resolved, users were asked to generate new private keys.
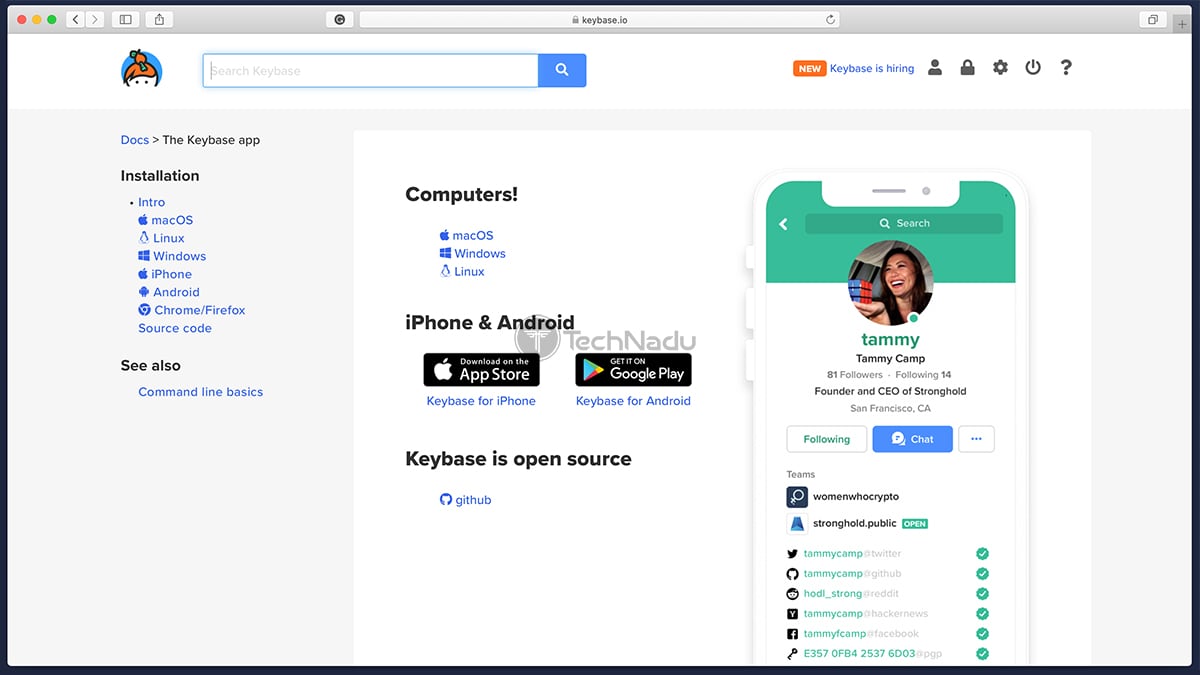
Supported Platforms & Devices
Keybase isn’t exactly a brand-new service, as it’s been available for several years now. So, it’s not surprising to see it offering a whole slate of applications for mobile and desktop platforms. Our Score: 9/10.
Keybase is trying to be an all-in-one solution, and therefore - it's available on plenty of platforms and devices. Let’s take a closer look.
As you can see, Keybase offers native applications for plenty of platforms. In addition, it provides you with extensions for Web browsers. This means that once you set everything up, it should be easy to stay on top of your messages, files, and everything else that Keybase helps you with. Also, it’s important to be said that none of these applications are in ‘beta’ – these are mature applications with plenty to explore from the get-go.
Next, we shouldn’t forget to mention that certain options of Keybase are available via Terminal commands – which comes in handy when installing the applications, verifying your identity, and in numerous other uses. This might present a problem for those looking for an easy solution, but we’ll talk more about the installation process in the following segment.
Installation & Initial Configuration
The process of getting started with Keybase isn’t an easy one – as you need to sign-up for a new account, download as many Keybase apps as possible, generate a PGP key and verify as many online profiles as possible (to prove your identity). Our Score: 5/10.
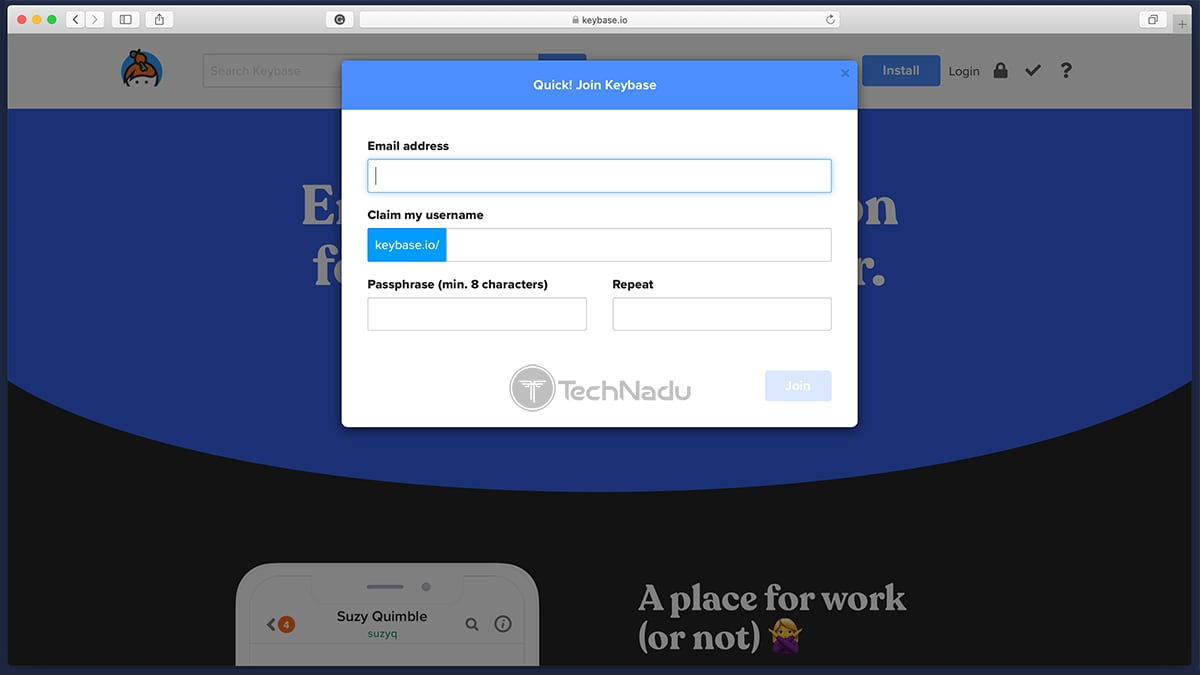
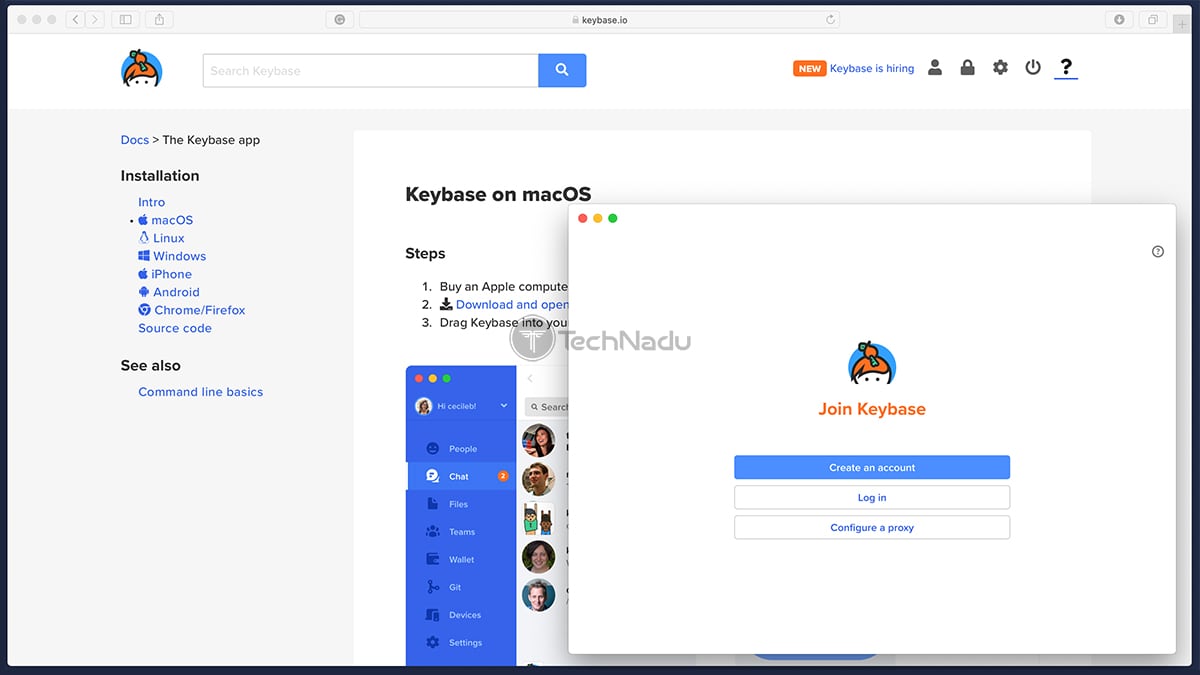
As you can imagine, the first step towards using Keybase includes registering for a new account. This is done on the official Keybase website, by going to Login > Join Keybase. You’ll need to input your email address, and then come up with a username and password.
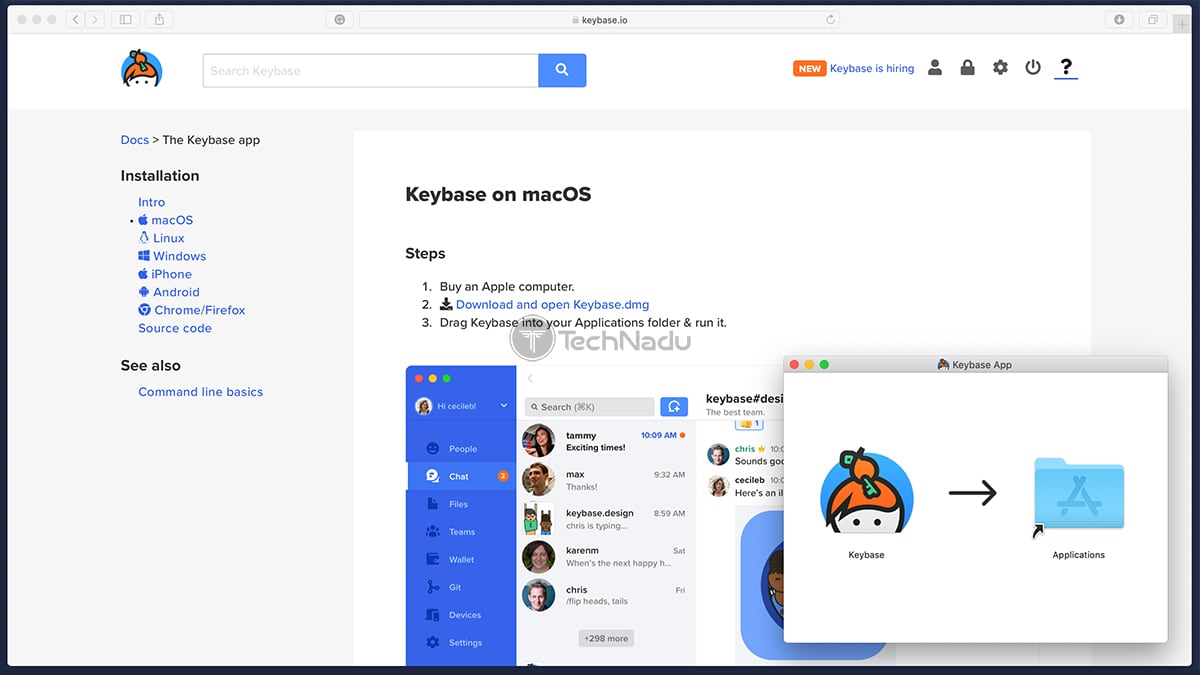
Once done, you will get to see your account’s dashboard – with a button saying ‘Action Required’ on the left. You’ll be asked to install Keybase, so click on the link you’ll find there – and you’ll see a page containing links to different versions of the applications. Then, proceed to download and install the app as you would normally do.
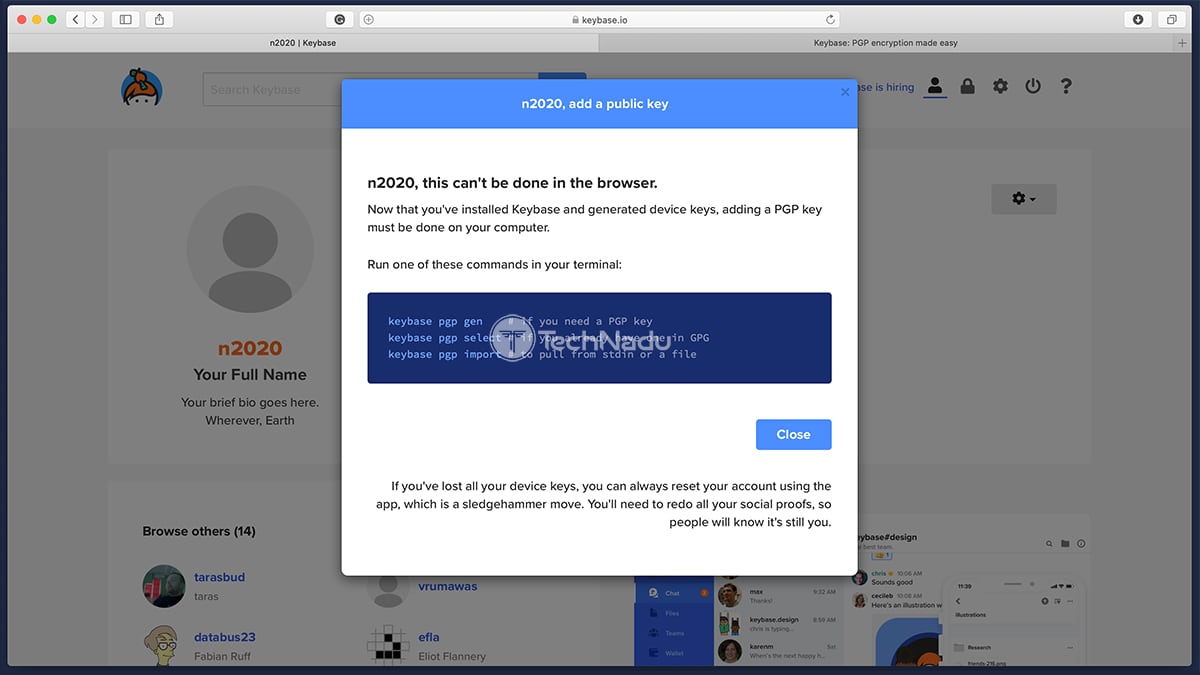
Next, you will be asked to create a PGP key. PGP stands for ‘Pretty Good Privacy’ – and it is used to encrypt your personal data. PGP usually works via a set of keys, where you have a public key (to encrypt your data) and private key (to decrypt data). So, to create your PGP key – you need to click on ‘Add a PGP Key’ found on your Keybase dashboard (on the official website). This is where you need to run one of three possible commands in your terminal (available on all desktop operating systems). So, go ahead, and open your terminal app and simply input one of the possible commands – to create a new PGP key, to verify your existing key, or important from a file.
Many of you will want to create a new PGP key – so you’ll need to go with the “keybase pgp gen” command. Once you input this command into your terminal, you will be asked for your real name and your public email address – and this information will be publicly visible in your new key. So, go through all the questions asked by your terminal, and your PGP key will be automatically added to your Keybase profile.
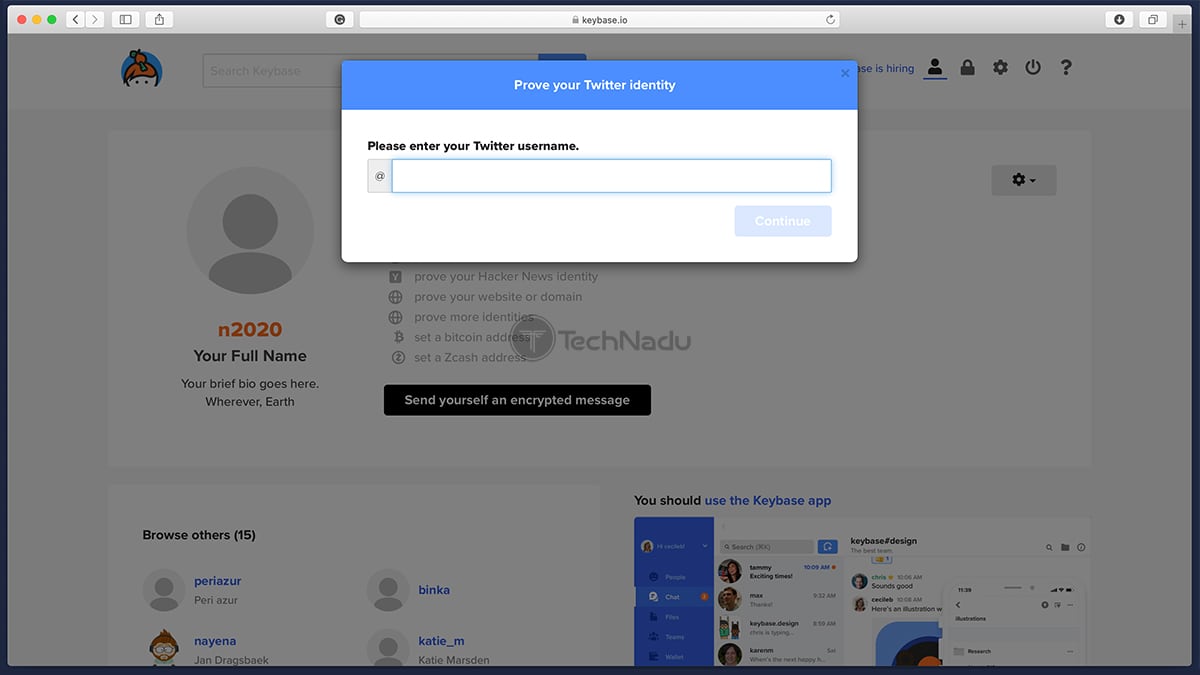
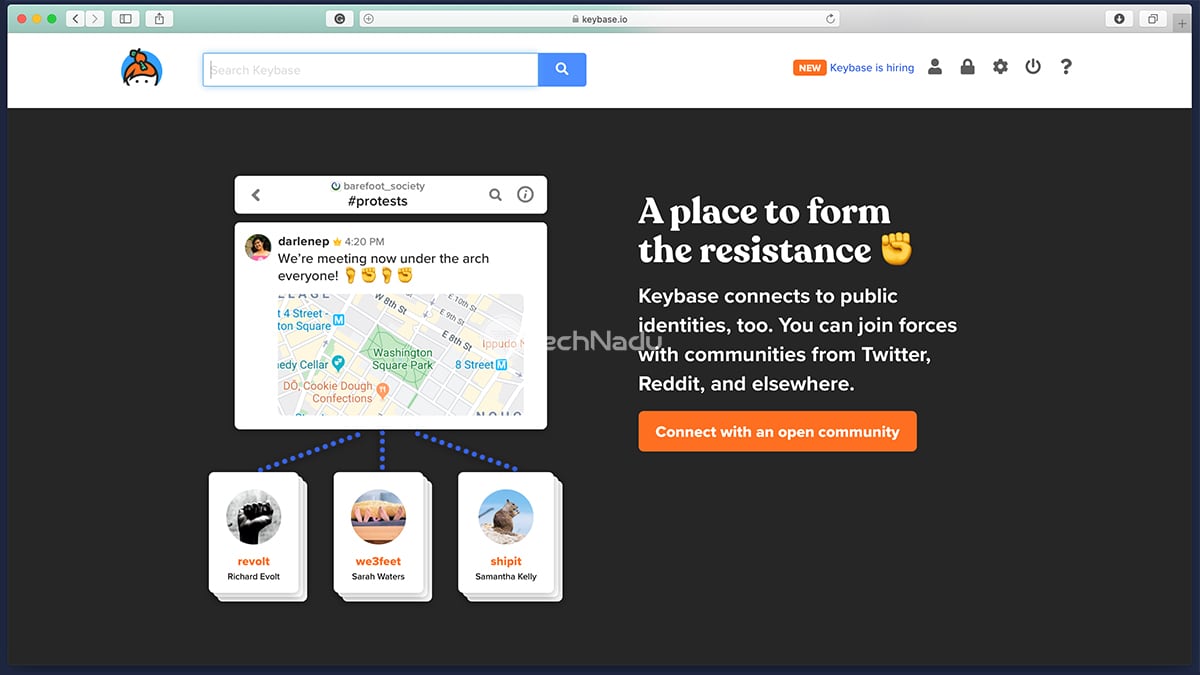
And now, we come to the final segment. So far, you’ve created a Keybase account, downloaded the Keybase app on at least one of your devices, and you’ve created a secure PGP key. The final step is to prove your identity, where Keybase right now supports Twitter, GitHub, Reddit, Hacker News, and a sizeable list of other online services. As you can see, Keybase allows you to verify your digital profiles and to prove your online identity. This means that in theory, an attacker will need to access all of your social accounts to impersonate you or verify other identities. And this is precisely what Keybase is all about – providing you a way to verify yourself online, talk to other verified Keybase users, and keep all of this communication under wraps.
User Interface
Just like with everything related to Keybase – you need to take your time to truly understand what’s happening here. However, once you learn the ropes, you’ll realize that Keybase comes with an intuitive UI (with some minor annoyances, still). Our Score: 8/10.
Once you finally set everything up – you can go ahead and check out the Keybase applications on your computer and smartphone. As you’ll see, Keybase follows a uniform design across all its supported platforms, which should ease up the transition.
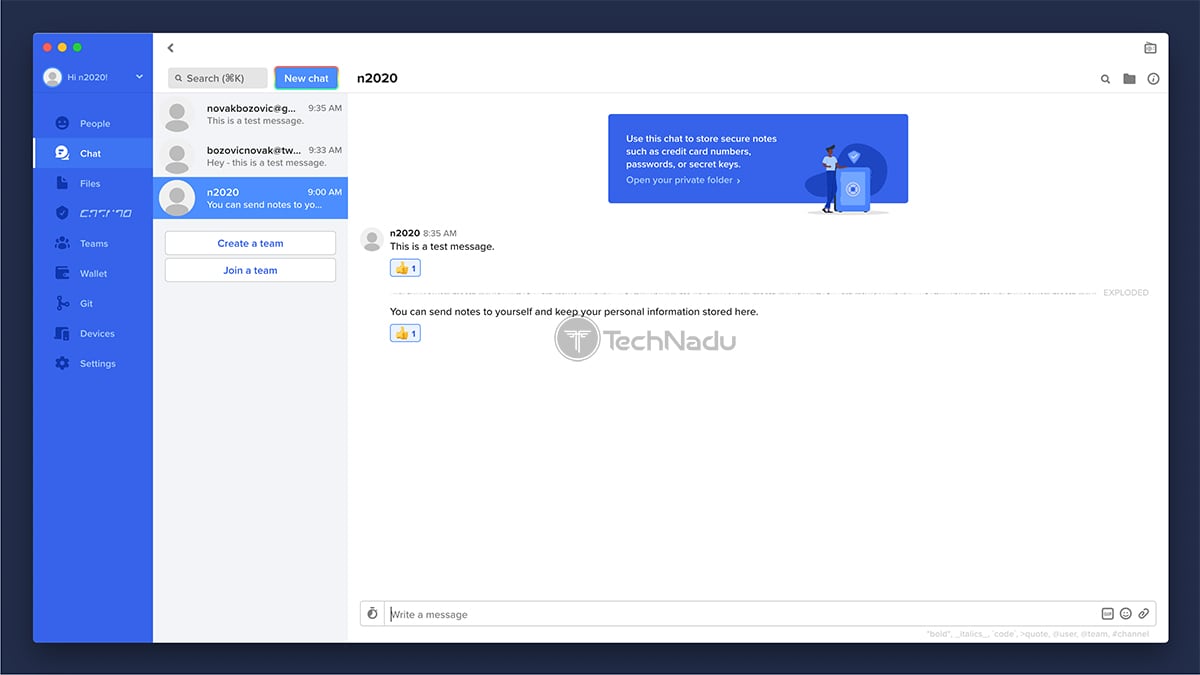
On macOS, you will get to see a simple app – at least when it comes to its general UI. On the left side, there’s a series of tools, which we’ll explain soon. As you click on any of these, the rest of the UI will change depending on the selected option. This is how you can easily switch between your messages, files, and more.
So, let’s see what each of these options holds.
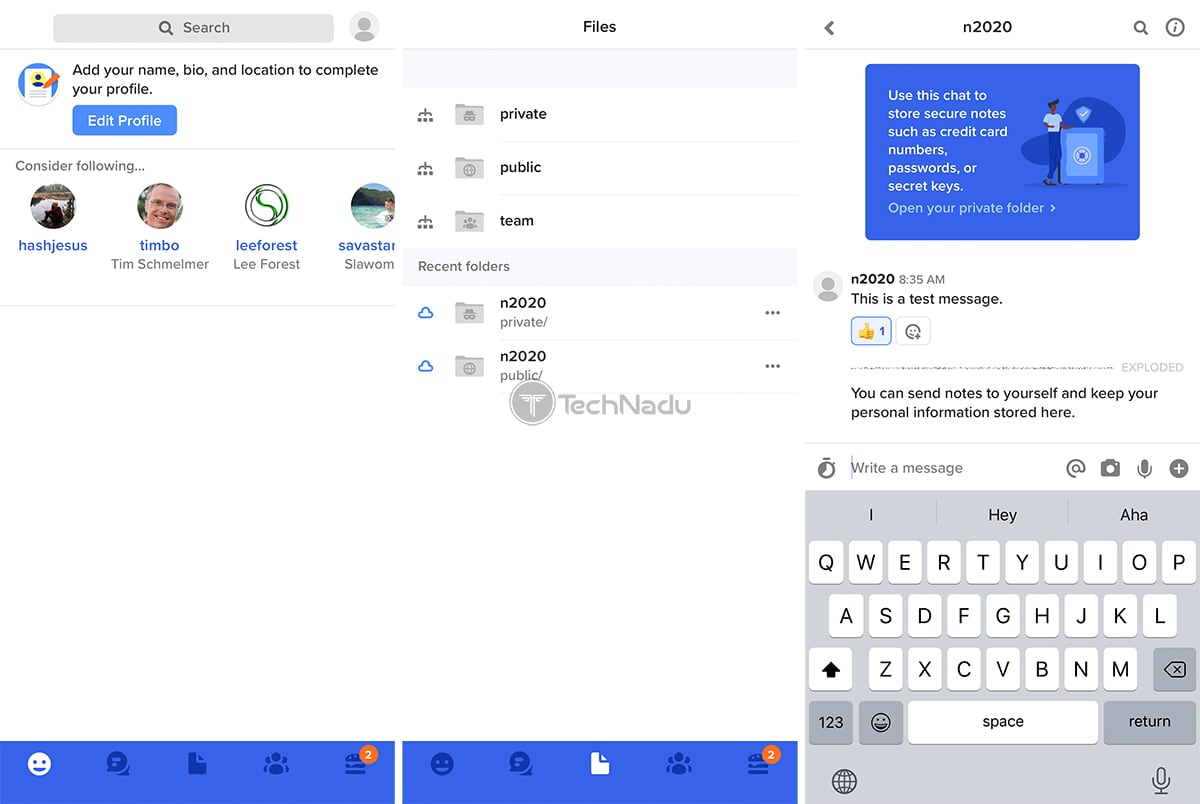
- People: First, you’ll want to follow other people on Keybase, especially if you want to communicate or work with them on a regular basis. This section of Keybase allows you to search through the service’s database of users, and you can narrow down your search based on different social media networks and individual websites.
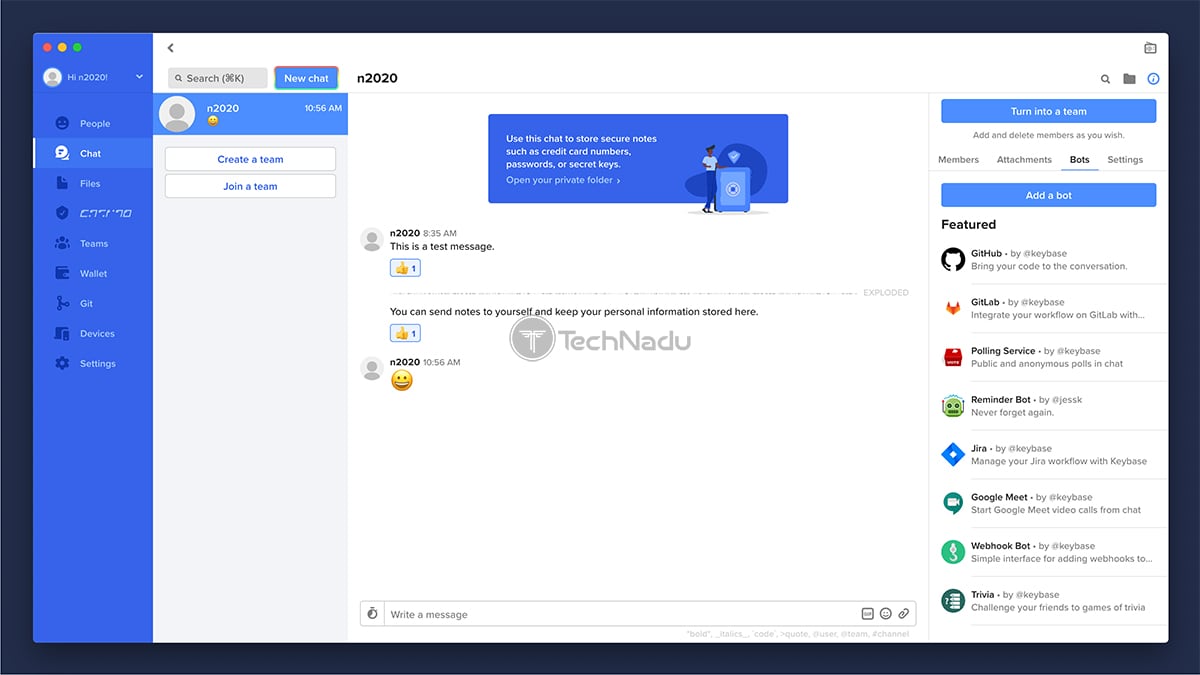
- Chat: This is where you can communicate with other users. Remember that all your communication comes with end-to-end encryption, and this is where you can exchange more than just text messages. You can send and receive files, GIFs, all kinds of attachments, and you can send “exploding” messages as well.
- Files: Keybase allows each user to upload up to 250GB of data – and this is separated into public, private, and team files. Everything you share or upload here is encrypted – no matter if you upload something to your private or public folder.
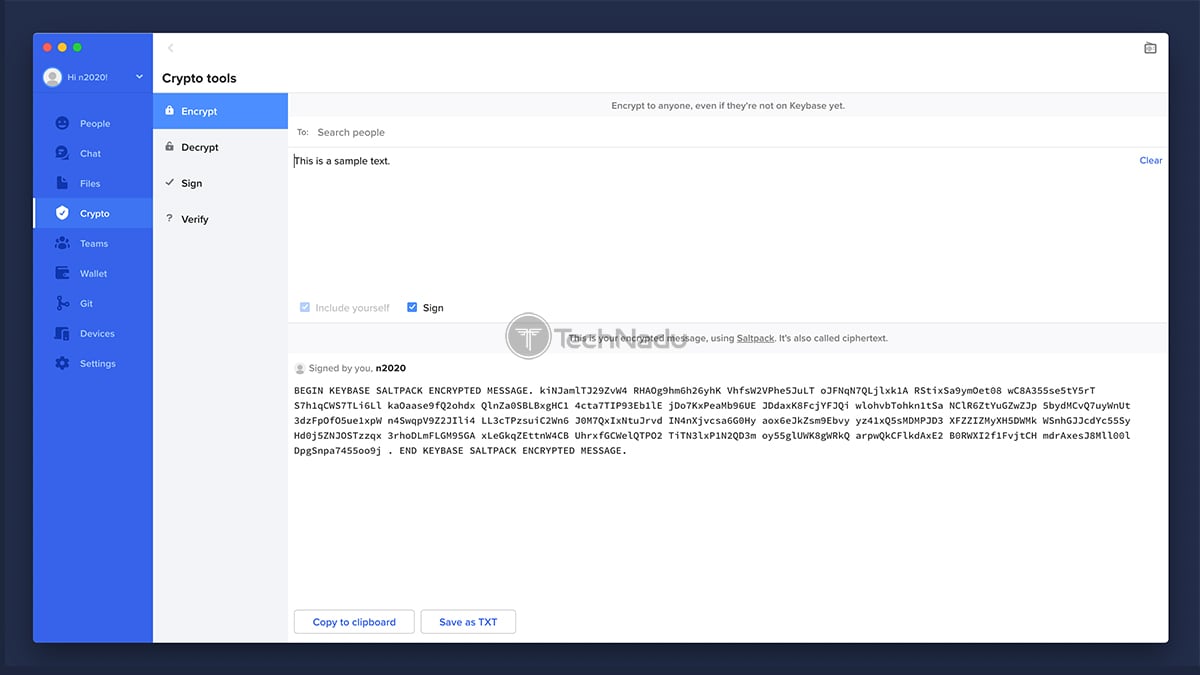
- Crypto: The ‘Crypto Tools’ section allows you to encrypt and decrypt your messages, as well a sign and verify them. This option comes in handy if you’re sending encrypted messages to users who are not on Keybase yet.
- Teams: Many of you are familiar with Slack or Microsoft Teams – which are applications designed for effortless communication within large teams. Well, Keybase can be used in the same manner. You can easily create new teams or join existing ones – and you’ll get to share messages here, along with any other type of data.
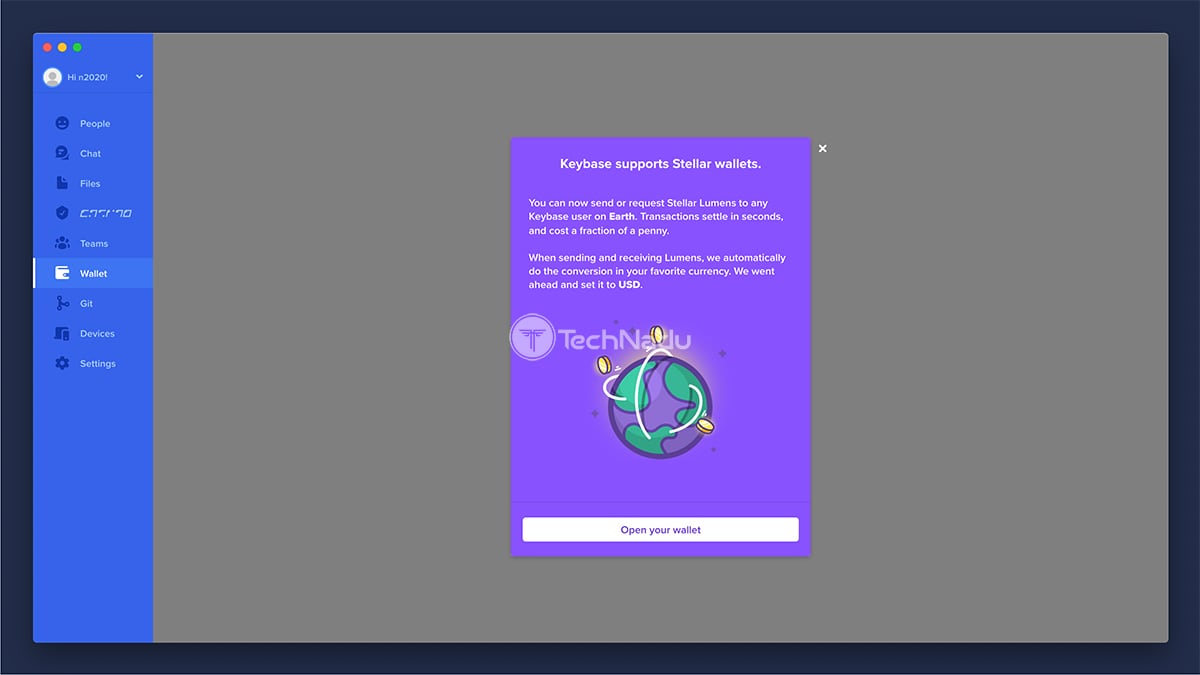
- Wallet: Who says that Keybase is only for messaging? The application now supports crypto-payments as well. This is where you can send or request Stellar Lumens – and these payments can be exchanged between Keybase users.
- Git: If you’re a programmer/developer, you already know what Git is – a free and open-source distributed version control system. You also understand the importance of handling your Git repositories in a secure way, as someone taking over your account can lead to massive damage. So, you can secure your Git repositories by keeping then contained within Keybase.
- Devices: All the devices you’ve added to your Keybase account will appear here. You are also free to add computers, phones, and create paper keys as well. In case you lose access to any of your devices, you can revoke access to that device – and Keybase will protect everything you’ve been doing within this application.
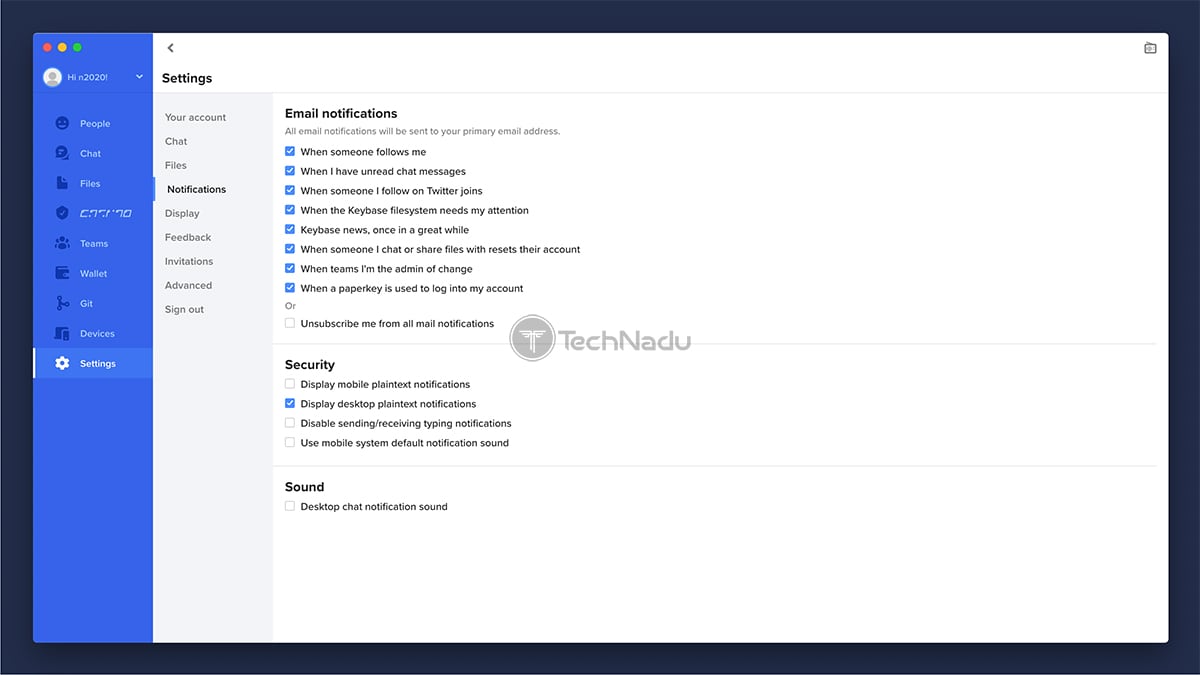
- Settings: When it comes to the application’s settings, you will get to manage your account (add new email addresses, change your password), choose between Keybase’s light and dark themes, switch between different notification methods, and similar. The application already comes with everything set-up properly, but you can dive into its settings to further customize it.
When it comes to Keybase’s mobile apps, they follow the same design pattern. At the bottom of the screen, you’ll find a series of segments – just like on the desktop app. In other words, this is where you’ll get to switch between messages, files, your crypto-wallet, and more. Once you learn the ropes of using this service on your computer, you’ll get to easily transition to its mobile app.
Ease of Use
Despite minor annoyances, Keybase is easy to use – once you handle the basics. First-time users will probably feel overwhelmed, so we recommend taking the time to explore the app. After that, you’ll focus only on what matters to you. Our Score: 7/10.
So, how easy it is to use Keybase? Considering that this application has the potential to be used daily (as your primary messaging app), it should be intuitive and simple enough. The best way to answer that question is by checking a usual workflow that you can expect.
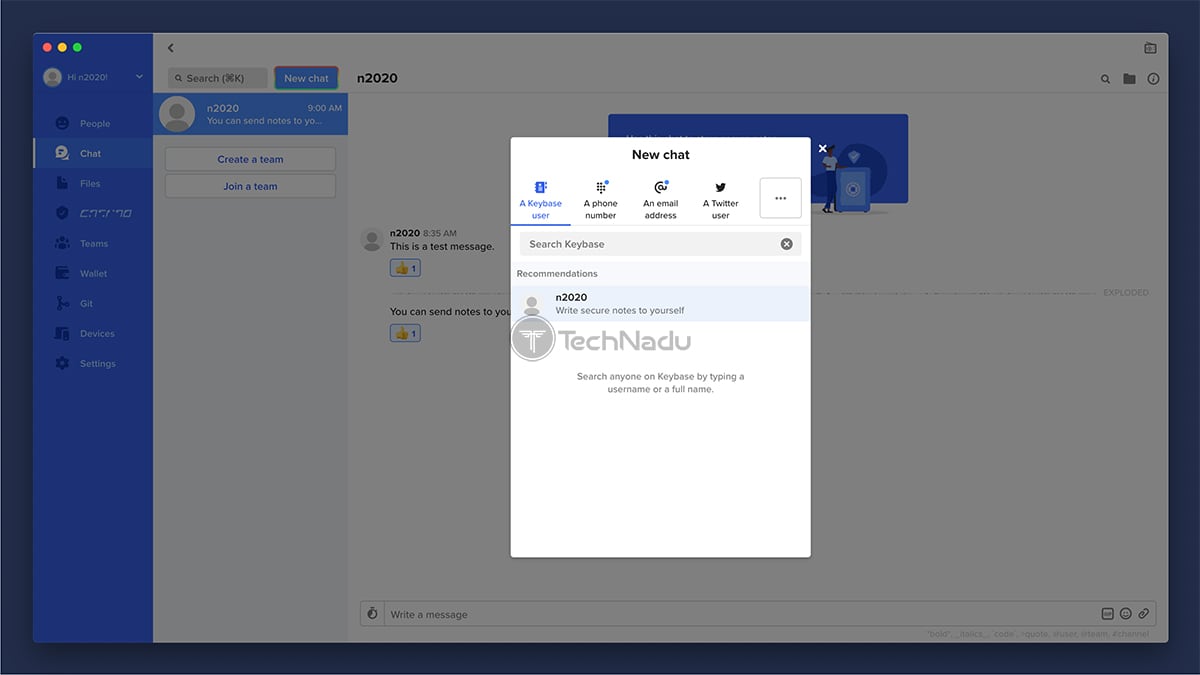
Even though Keybase is much more than a messaging app, it’s being advertised as the ultimate solution for exchanging messages. So, to get started, you can use the ‘People’ or ‘Chat’ tab to search for other Keybase users. If you go with the ‘Chat’ tab, you need to click on the ‘New Chat’ button. Then, you can search for individuals in the Keybase database, or you can search via a phone number, email address, Twitter handle, and in a couple more ways. If you find someone who’s not on Keybase, you can still send them a message – but you’ll also receive an invitation link that needs to be shared. The recipient will need to register for Keybase to read your message.
As you start to type your message, you’ll see a series of options. You can send “explosive” messages that disappear after a certain time, and you can also send GIFs, emoji, and pretty much any other type of file/data. You can also ‘react’ to messages in a similar way you can do on Slack, for example. Keybase can also integrate with a number of bots, so you can bring GitHub, Jira, or Google Meet into your chat.
So, here’s the best way to explain Keybase and its chat-related options. If you’ve ever used Slack or Microsoft Teams – you will have no problem understanding Keybase. The way you send messages is intuitive enough, and you can use markdown to format your text, you can mention someone (@someone), or refer to a particular channel (#channel). This also applies to the sending and downloading files within a single thread.
All in all, Keybase is actually easy to use. First-time users will most probably feel overwhelmed at first, simply because there are so many features combined in a somewhat confusing way. And also, the chances are that you won’t use all of Keybase’s features – as they’re really wide in their scope. So, it would be good to eliminate those from Keybase’s UI and to simplify things – which can’t be done right now.
Security & Privacy
Keybase collects plenty of information about your use of the application. However, it can’t read any of your encrypted messages or files. And also, a recent audit proved that Keybase comes without any risks for your online privacy. Our Score: 9/10.
Aside from proving your online identities, Keybase is used for secure communication and cloud-based file storage. In other words, you’ll want to know how Keybase protects your privacy and whether it collects any data. So, keep on reading to learn more.
Privacy Policy
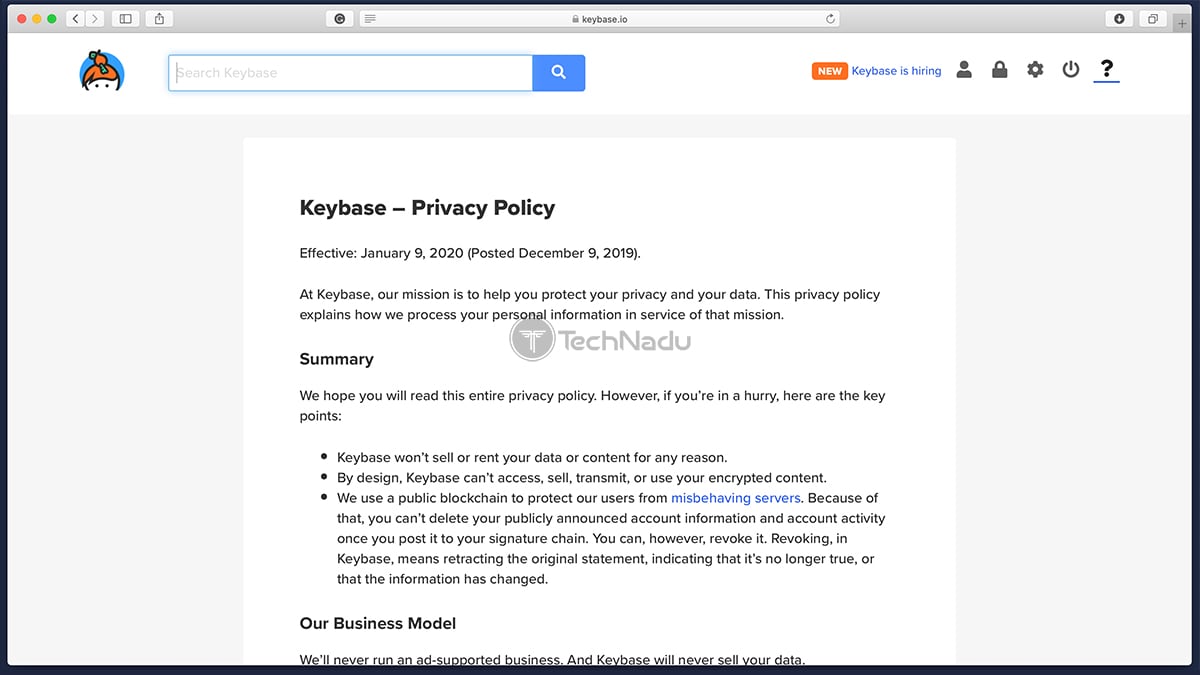
When it comes to Keybase’s Privacy Policy, the document starts by saying that this company’s mission is to protect your privacy and your data. It then continues to explain that Keybase doesn’t sell or rent your information – and also, Keybase can’t read your encrypted data. So, this means that some information is still stored on the company’s servers.
Speaking of your PII data stored on Keybase’s servers, we’re talking about your contact and account information, team names and membership, hashed Keybase passwords, account activity, any files or data you upload, unique personal identifiers, network usage and activity, and any interaction you have with the company. As you can see, plenty of information is collected. However, it’s important to understand that anything you encrypt within Keybase is not readable by anyone – and this includes the company behind Keybase as well.
You should also know that Keybase uses blockchain technology. Every account has a public signature chain, which is a list of statements about any changes related to your account. In other words, you can’t delete any information from this “sigchain”. If you change your Twitter username (for example), your old username won’t be deleted from your sigchain – you will only get to revoke it and then verify your identity by using your new username.
Encryption & Technical Security
The most important piece of information here is that Keybase secures your communications and files via end-to-end encryption. This means that your files are encrypted before they’re sent over the Web, and they’re decrypted only by the recipient. Considering that Keybase doesn’t have the key necessary to read this data, only you and the recipient can see this data. This also means that no one on the Web will be able to see anything that you’ve encrypted.
It would be an understatement to say that Keybase is based on complex technologies. We’re talking about end-to-end encryption and blockchain here – and it would take hours just to begin explaining the underlying technology used in this case. Therefore, to understand more about the safety and privacy that Keybase offers, our strong advice would to check this public report, published by NCC Group. As you'll get to see, the report points to certain weaknesses of Keybase’s design – all of which were promptly fixed. In total, 5 issues were discovered – and none of those were marked as being ‘high risk’. No critical issues were found, though.
So, what can we conclude here? Is Keybase safe? Well, we can conclude that Keybase is based on highly complex technologies, so it’s best to leave cybersecurity experts to inspect its code. Based on the most recent report, Keybase protects your privacy is a secure way and comes without any vulnerabilities that could expose your data.
Customer (User) Support
For inexperienced users, everything about Keybase can be confusing. Sadly, you won’t get to find plenty of reading material about the technology that powers Keybase, which is something we wished to see greatly improved. Our Score: 5/10.
Even before you start using this application, we’re sure that you’ll have many questions. Keybase is unlike any other application out there – and it looks to be rapidly expanding into new areas. So, you’ll want to learn about this application, as well as stay on top of the latest developments. However, Keybase doesn’t provide an in-depth customer support section. Instead, you’ll only get to rely on the application’s “Docs” page.
The Docs page allows you to learn about some of the technology that powers Keybase, and you’ll also get to learn about its individual features. However, this content isn’t exactly written for average computer users, so we recommend diving into it only if you have some experience with encryption and blockchain. Of course, some parts are less challenging to read, so it doesn't hurt to take a look. We also recommend checking Keybase’s blog, where you’ll find additional information about this application – especially if you check older posts.
Pricing
Keybase comes completely free of charge – and it doesn’t have any hidden costs. Premium features are expected to arrive at some point in the future. Our Score: 10/10.
So, the big question is – how much does Keybase cost? Well, it costs $0! Yes, that’s right – this entire suite of features is completely free-of-charge, without any hidden costs. As per Keybase’s website, the application will remain free and without any ads in the future. However, there are plans for premium features to be introduced at some point – reserved for those willing to pay. There aren’t any official announcements about this, just yet.
If you decide to become a Keybase user, there’s nothing to be concerned about in terms of your expenses. Premium features are going to be optional and they won’t affect your current use of the application.
Do We Recommend Keybase?
As per different sources online, Keybase has from 100,000 to 400,000 users. So, in terms of the size of the global market, this is still a niche product. This is something you’ll also realize as soon as you start using this application. It’s truly unique and highly innovative, but it’s trying to do too many different things at once. With this said, we can recommend it to high-end users who really want to explore the latest of what today’s blockchain and end-to-end encryption can do.
- PROS: Highly innovative; Ultra-secure; Offers many different tools; Present on a wide range of platforms; Offers a unique concept.
- CONS: Complicated initial configuration; Semi-helpful customer support resources; Not used on a massive scale; Can be overwhelming for average computer users.
- OUR SCORE: 7.6 out of 10!
In case you want additional information about this digital service and its applications, we recommend checking the official Keybase website. And with this, we conclude our lengthy review of Keybase. If you decide to become a user, make sure to share your experience with us via the comments section below. Thanks!
| Review Summary Keybase is something truly unique and innovative - but it's trying to do many different things at once, which often leads to confusion. However, if you're a high-end user willing to explore new technologies, you're going to like what you'll find here. | 7.6 Overall Score | ||
| Background, Jurisdiction & Reputation | 8 | ||
| Supported Platforms & Devices | 9 | ||
| Installation & Initial Configuration | 5 | ||
| User Interface | 8 | ||
| Ease of Use | 7 | ||
| Security & Privacy | 9 | ||
| Customer (User) Support | 5 | ||
| Pricing | 10 | ||