Internet Safety Bootcamp: A Practical Online Safety Guide
Using a worldwide network like the internet is an amazing experience. In seconds you can find any information you need. You can shop online for anything from food to furniture.
Overall the internet is possibly the human invention that has done the most good for humanity. It’s had an impact in just about every aspect of human existence. From our personal social lives all the way to national interest projects, such as scientific research and public services.
At the same time, the internet brings with it significant risks and dangers. By connecting everyone together, we also allow elements of the world that are out to enrich themselves or cause hard. Although such people may be an overall minority if they aren’t defended against.
Governments and big companies like Google have done a lot to increase our online safety. That does not mean we can just sit back and relax. Ultimately the responsibility for your online safety is your own. By the end of this article, you should understand the main risks that come with being an internet user and the main ways to defend against them.
Why is Personal Information Sensitive?
You’ll often hear about how personal information is the main target of various internet attacks and scams. Have you ever stopped to ask yourself why this information is so valuable? Obviously, if someone can get a hold of your passwords or credit card numbers, they can steal your money. That’s probably the type of information theft that most people think of when the topic is brought up.
There are other pieces of information that you may not worry about too much. Often these are the sorts of things that can simply be looked up. There are plenty of people who feel that if they have nothing to hide then it doesn’t matter if someone has this personal information.
The truth is that even seemingly innocent personal information can be used for some pretty nasty purposes in the wrong hands. ID numbers, passport information, where you work, who you know and even when you are going on vacation are all things that can be used against you. If someone knows enough about you, it makes it easier to trick you. Alternatively, they may simply use that information to steal your identity. That’s just two vectors of attack. You can be sure they are coming up with new ones every day.
The bottom line is that you shouldn’t assume because you don’t think that some personal info isn’t desirable, doesn’t mean that someone, somewhere has a use for it.
Securing Your Devices
The individual devices that you use to connect to the internet each come with their own security weaknesses. The good news is that at this point in our technological development, device security is fairly good.
Not all attacks on your personal information will come from somewhere far away on the internet. Local unauthorized access is a problem too. If someone steals your smartphone or laptop they might suddenly have access to almost all of your accounts and information.
A passcode or password is a given. Make use of remote wiping and tracking functionality as well. If you really want a robust remote security solution, consider something like Cerberus.
You should also ensure that your device has a good security suite. This should include an anti-virus, anti-malware and network firewall function.
Finally, if your device has the ability, encrypt the content of its storage. That way it’s almost impossible for someone to forcibly extract your information if they have your device.
Securing Your Network
There are two types of network defense that you need to mount for your own internet safety. Both your local- and wide- area networks need security. When it comes to the local network, you should ensure that your WiFi password is a strong one. Disabling WPS is a good idea too if your router has it. Do change the router’s administrator password from the default. So that even if someone manages to break into your WiFi network itself the won’t have free reign.
On the WAN front, you might want to make use of a router-level VPN or at least a device-level VPN. VPNs encrypt your network traffic so that people on the net cannot tell where you are browsing, what information you are sending or anything else really.
That doesn’t mean you should trust any VPN provider blindly, however. Check out our VPN buyer’s guide to see what factors really matter. We also have a running top five VPN list worth checking out. While it’s rare, it can also be illegal in some countries to use a VPN, so double check your local laws.
Dealing With Public WiFi
If at all possible, you should avoid using public WiFi hotspots. If you absolutely must expose yourself to an unknown network then a VPN is an absolute must. Otherwise, your information may be stolen by anyone within range.
Recognizing Scams
The internet is a paradise for scammers of all stripes. While we can deal with network intrusions, viruses and malware using technology, scams target something else: you.
A scam is meant to fool the person it’s targeted at into giving up their information or willingly loading malicious software onto their systems. Usually, it works by contacting the person via email, Skype or some other channel. The scammer will misrepresent themselves somehow an attempt to manipulate you.
Often these attacks are very scattershot. Scammers will send out masses of emails, most of which are either caught in automated spam filters or quickly dismissed by the recipients. This acts as a natural filter: only the most vulnerable people are likely to respond.
The only way not to be caught is by developing critical reasoning skills. At the very least you should ask yourself the following questions:
- Was I expecting this message?
- Do I know the person who sent this to me?
- Is what they are saying reasonable?
- Does it sound too good to be true?
- Is the use of language poor?
Interrogate any message that requires you to give up any personal information. Regardless of what you think about the message never give up your credit card details, ID number or any usernames or passwords via email or instant messaging.
Phishing and Spear Phishing
Two prominent types of scam that you should be aware of are phishing and spear phishing. As the names suggest, these are attempts at getting someone to give up their credit card details, usernames, passwords and more.
Usually, you’ll get an email from what looks to be your bank or other trusted entity. They might “spoof” a plausible-looking email address.
The key indicator of a phishing attempt is that the entity wants you to send information by using a link within the message or as a direct email reply. That’s the main reason no bank or other institution will ever ask you to click on an email link.
As a rule, you should only provide sensitive information by manually going to their website and logging in. Clicking on a link in a phishing email will usually take you to a fake version of their site. When you try to “log in” it actually captures your credentials. The scammers can then access your account on the real site.
Often the emails will be written in such a way that they make you act before you think. It might be an email about your tax affairs or something that says your email account is going to be deleted unless you log in. By creating a sense of urgency, the scammers reduce our time for critical thought.
“Spear” phishing is a more targeted attack. Here you aren’t the victim of a mass attack. The scammers know who you are and will pose as a colleague or someone you expect to hear from.
If the request is unusual, such as asking you to pay an amount into an account, verify via another channel such as a phone call whether the request is real.
Using a Web of Trust
Because of how many scams site there are out there, other sites that use crowd-sourcing have sprung up to give people a good idea of how risky a given site is. For example, Norton Safeweb is a service from Symantec that helps users figure out is a site is fake or not.
Using community web safety sites such as these can help prevent you accidentally buying from fake online stores or giving information to known scammers.
The Risks of P2P and Illegal Sites
Everybody loves TV shows, movies, games, and music. Not everyone likes to pay for them. These days thanks to cheap streaming services and other subscription models, piracy is not as popular as it once was. Still, plenty of people flock to torrent and “warez” sites to get some free entertainment.
Predictably hackers, scammers, and others of ill-repute take this as a fantastic opportunity to embed malicious software in your system. The authorities may also capture your IP address and trace your activities back to you via your ISP.
The only way to be safe in this instance is to stay off illegal sites and avoid using torrents from providers you can't verify.
Two-Factor Authentication is King
Two-factor authentication is a way to split the credentials you need to access a system into separate systems. You need both factors to log into anything.
Your SIM card or primary email are common secondary factors. So when you provide the correct username and password a one-time confirmation code is sent to another account you control. Unless the hacker in question also controls your email or has a copy of your SIM card, they can't get in.
Learn Safe Password Habits
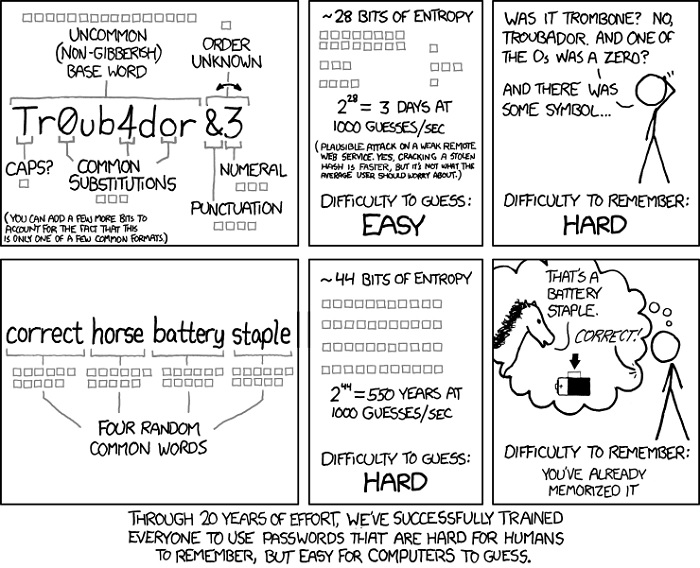
Image is CC BY NC. Source XKCD
Your password is a key to a cryptographic puzzle. Which means that if someone happens to guess your password, they can unlock your account or encrypted information protected by it.
Of course, most websites only let you try two or three times before locking you out, so it's incredibly unlikely that someone will guess it in the number of tries allowed.
When a company that hosts your information suffers a data breach it's a different story. If a hacker has a database of cryptographic hashes sitting on a hard drive, they have plenty of time to let a computer sit and guess the password.
As the popular XKCD cartoon above indicates, your password choices affect how hard or easy it is to brute force your way past it with guesses.
The strongest passwords are those that get generated by a randomizer algorithm. They are basically impossible to remember though, so for an optimal solution you should use a password manager.
The Cloud is Your Friend
These days cloud storage through providers such as DropBox is dirt cheap. They'll give you a terabyte of online storage for about ten bucks. That's more than enough for most people to keep copies of critical information safe.
Ransomware, in particular, will destroy your data permanently. Even network drives and attached USB storage isn't safe. Services like DropBox, on the other hand, can roll back your files weeks or months into the past. Now that's peace of mind.
Credit Monitoring Can Catch Identity Theft
The recent Equifax data breach has left a lot of people worried that their identities will be stolen and used to incur debt or other credit-related activities. It's a legitimate fear, so the option of credit monitoring has been put on the table.
If you pay for credit monitoring then you'll be alerted as soon as someone applies for credit in your name. That could save you a lot of trouble and help you stop identity theft in its tracks.
As it happens, Equifax itself is offering a year's worth of free credit monitoring for anyone affected by their breach.
Pay Attention to Credit Card Statements
I know, I know. Who wants to go through all that paperwork at the end of the month? Still, you should make a habit of scanning through your credit card statements at the end of each month to spot any weird charges that you don't recognize.
While most card providers will send you an email each time a transaction happens, there is usually a lower threshold for these notifications. Small charges might be slipped through undetected this way. If you have any doubts about a charge, even if only for a buck or two, phone the card company immediately.
It's All in Your Head
No really, effective online safety is more about your mindset than any sort of specific actions you can take. The bad guys are always adapting to our countermeasures. This means we can't learn good safety by rote.
Instead, what matters is situational awareness. The knowledge that you might be targeted should be in your thoughts when you're on the web. Pay attention to what you see and trust your gut when things don't feel right. Apply critical thinking and raise red flags whenever you're asked for sensitive information when you weren't expecting to be.
There's no such thing as a perfect defense, but you can get pretty close with your head screwed on right.