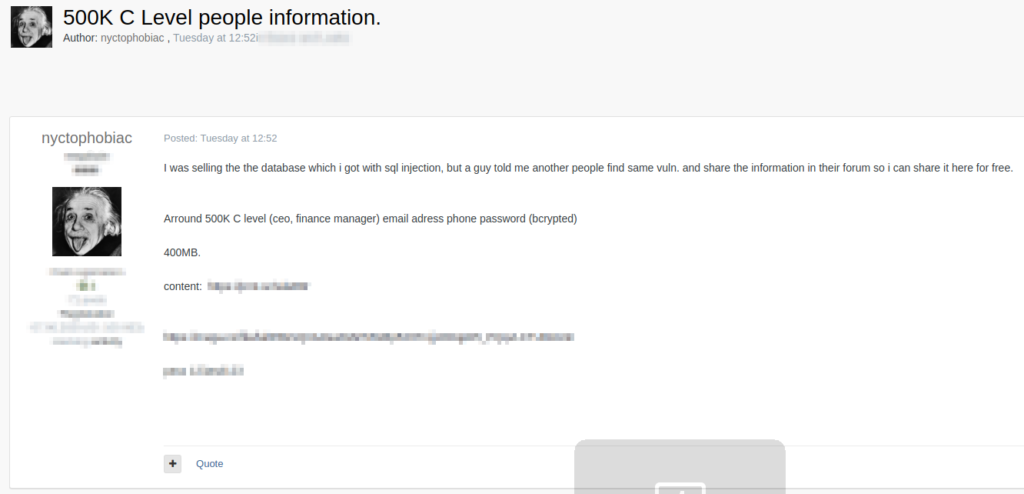
Database Containing the Data of Company Executives Posted on the Dark Web
- Half a million records of high-ranking individuals from around the world are freely shared on dark web forums.
- The exposure is severe as it includes email IDs, phone numbers, and hashed passwords of company CEOs.
- The leaking website had an SQL injection vulnerability that was exploited heavily before the platform’s IT noticed and plugged it.
About 500,000 records of C-level (high-ranking executives, CEOs, Finance Managers) individuals have appeared on a Russian-speaking dark web forum, exposing the sensitive details of people who are considered “key” in the firms they work for. The new pack was discovered by researchers of Cyble, who have informed the individuals found in the shared database.
According to the poster of the database, it belongs to “capitaleconomics.com,” which was compromised thanks to the existence of an SQL injection vulnerability.
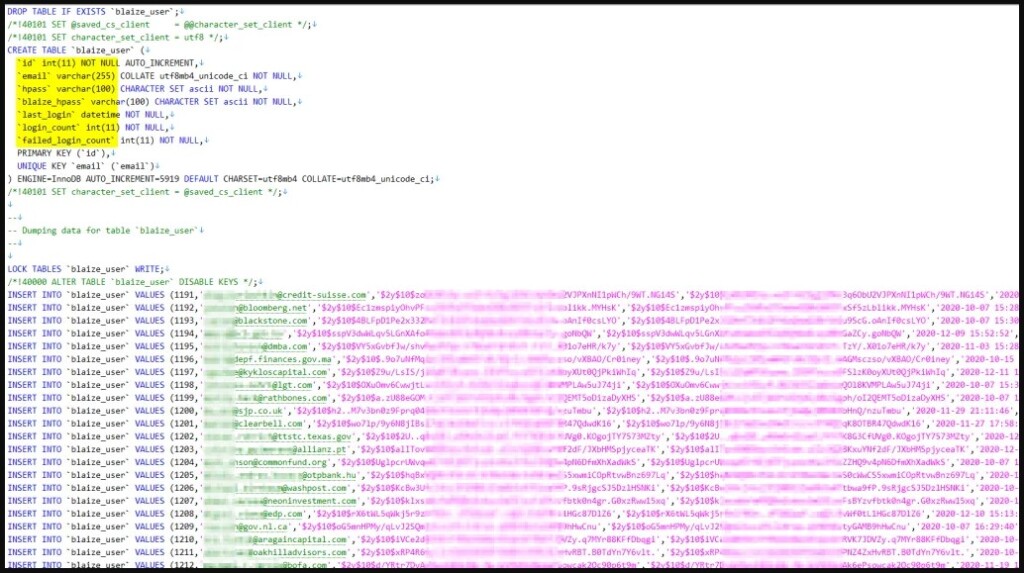
The database was initially put up for sale. Still, since the tip about the existence of a vulnerability on the particular website was shared among more hackers, the poster decided to just share all 400MB of stolen data for free. The details contained in the pack include the following:
- Email Addresses
- Phone numbers
- Passwords (bcrypted)
'Capital Economics' has amended the flaw now, so the data is no longer available for exfiltration, but the data leak has already happened. In this case, having a leak of email addresses and phone numbers creates a notable exploitation potential.
The valid email IDs can be used for business email compromise (BEC) attacks following account takeovers, and of course, phishing. Phone numbers can be used for SIM swapping leading to 2FA bypassing, malware distribution through SMS, or smishing.
We have reached out to Cyble’s experts, who have downloaded the database to check the validity of its contents, as well as to inform the affected individuals. They confirmed that the data appears to derive from executives working on companies from around the globe. So, this was not a focused leak concerning a particular region.
What is not clear is whether these people were members of the Capital Economics platform or if the service somehow scraped their data from a partner or a third-party. Also, there’s no data leak notice on their website or their social media channels at the time of writing this.
The Bcrypt algorithm that is used for hashing the passwords is generally considered secure, but it’s not very effective against crackers who are willing to put in the effort against short and weak passwords. Thus, resetting your passwords and picking something unique and strong like a long passphrase would be the right thing to do now.