“DarkHotel” Is Exploiting VPN Zero-Days to Breach Chinese Agencies
- The “DarkHotel” APT was engaging in cyber-espionage operations against the Chinese government.
- The hackers have set up a very clever attack chain based on a zero-day that has been fixed now.
- The exploited software is Sangfor SSL VPN, which is extensively used by Chinese agencies.
“DarkHotel,” the same group of actors that was recently suspected of targeting the WHO, are reportedly now exploiting zero-days in VPN tools to attack various Chinese government agencies. DarkHotel is an APT that has previously been involved in intelligence gathering operations, and which has targeted a broad spectrum of fields, from electronics and pharmaceutical manufacturers to military defense and law enforcement service providers. For years, it used hotel networks to follow its high-profile targets (CEOs, vice-presidents) around as they traveled. This time, they are allegedly focusing on Chinese agencies and their employees.
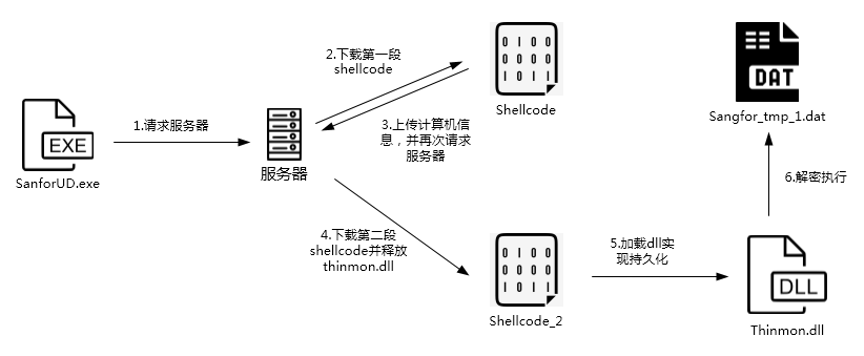
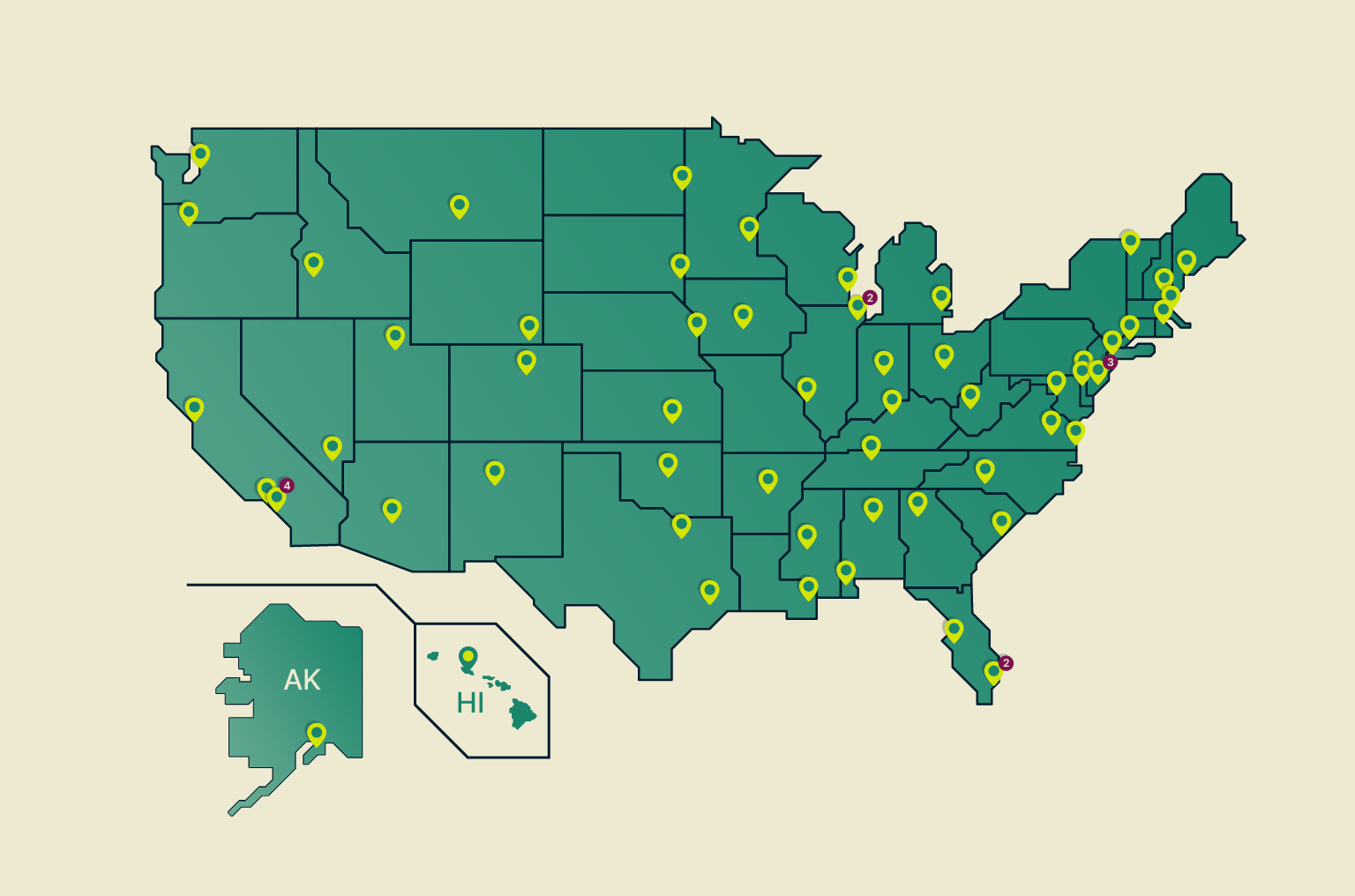
According to reports by the Chinese security expert Qihoo 360, DarkHotel is exploiting a zero-day vulnerability in Sangfor SSL VPN, which is the top enterprise network access solution of the Shenzhen-based ‘Sangfor Technologies.’ Of the 200 VPN servers that have been compromised in this campaign, many belonged to government agencies in Beijing and Shanghai, as well as Chinese embassies in the UK, India, Israel, North Korea, UAE, Saudi Arabia, Italy, Thailand, Indonesia, Iran, and Turkey. Hackers managed to discover a novel attack chain that gave them access to Sangfor VPN servers by replacing “SangforUD.exe” with a malicious clone they created.
Source: Qihoo 360
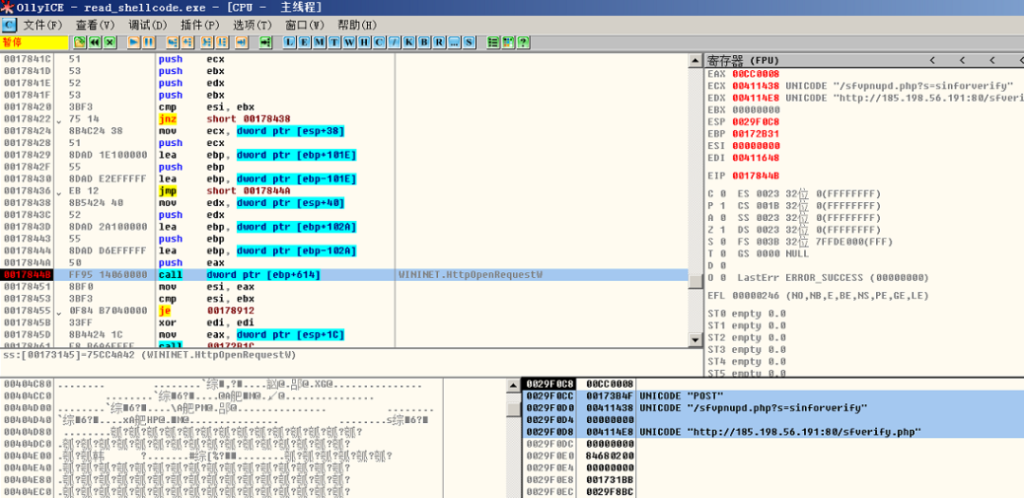
They then pushed this file as an update of the Sangfor VPN desktop app, which the users installed on their computers. The hackers were then able to plant a backdoor to the target devices and execute code via shellcode fetched from the cloud. As the Qihoo 360 researchers point out, the entire attack is very sophisticated and well-concealed. The shellcode gets system information and sends it to the C2 server. At the same time, the backdoor will install malicious DLL components that can do things like hijacking the printer service on the registry level.
Source: Qihoo 360
DarkHotel, which is an APT that is believed to originate from the Middle East, is actively taking advantage of the current situation that has introduced much carelessness to system administrators. Diplomatic missions are using VPN tools to connect remotely, so highly valuable secrets are flying around at unprecedented rates right now. Interestingly, the attackers were found to be focusing their attacks in very old Sangfor VPN server versions, that date back to 2014. This is indicative of the negligence and sloppiness that underpin the current “remote work” operations even at the highest level, and how the pandemic has found everyone unprepared, except for the malicious actors.