ScarCruft Evolution on the Spotlight with a New Bluetooth Harvester
- ScarCruft activity spotted by Kaspersky, and the group shows signs of rampant activity and evolution.
- They now use a Bluetooth searching tool that harvests information about the connected devices.
- ScarCruft uses some of the same tools as DarkHotel APT does, and often targets the same organizations.
Kaspersky researchers who have been following the Korean hacker group “ScarCruft” are reporting on their most recent findings that indicate new developments. The particular threat actors have already proven that they are skilled and resourceful, carrying out successful attacks since 2016 and going largely undetected. However, Kaspersky Lab researchers have managed to use recent telemetry data and restructure ScarCruft’s binary infection procedure, which sheds light on the newest techniques used by the malicious actors.
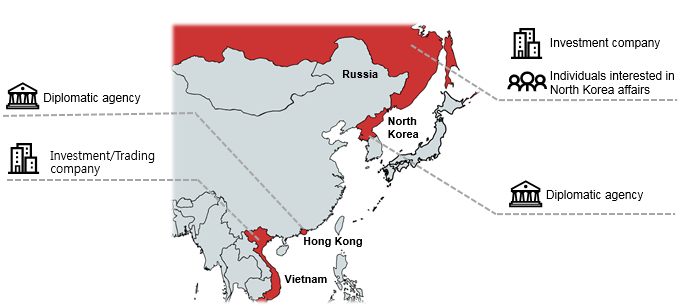
First of all, ScarCruft’s current geographic location of interest seems to be trading companies based in Russia and Vietnam. There’s also an incident that shows a diplomatic agency in Hong Kong as a target, as well as another one in North Korea. This indicates that the group is acting based on intelligence gathering, which could mean that they are state-sponsored. However, this can’t be defined with certainty and it’s just an assumption.
image source: securelist.com
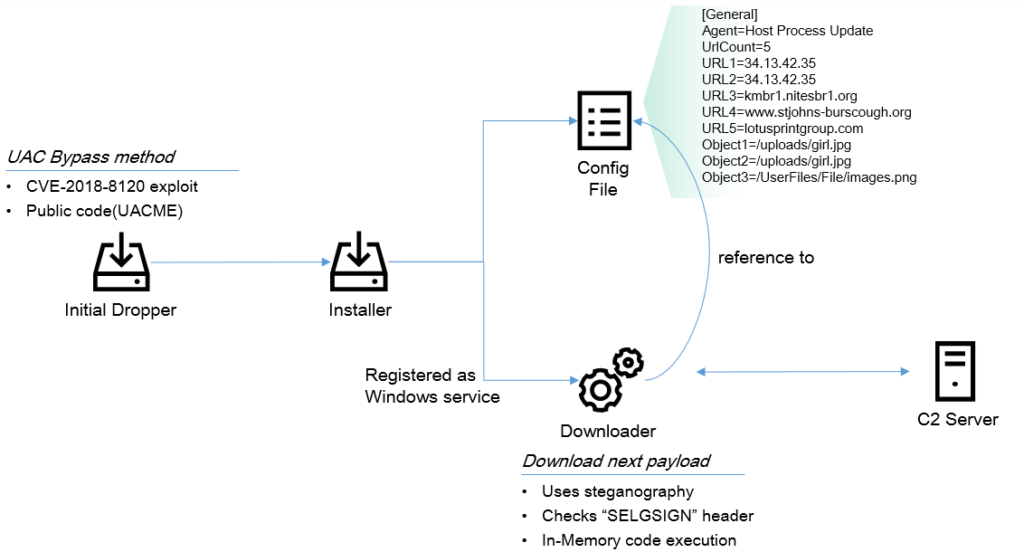
To carry out the infection and deploy an implant that will download the main payload, ScarCruft does what any sophisticated group would do, and that is to exploit zero-day vulnerabilities. The initial dropper has the capacity to bypass the Windows UAC (User Account Control), so the required system privileges to download the primary payload are secured. To minimize the risks of being detected at the network level, the malware downloader uses steganography, so the downloaded file is an image containing encrypted malware code.
image source: securelist.com
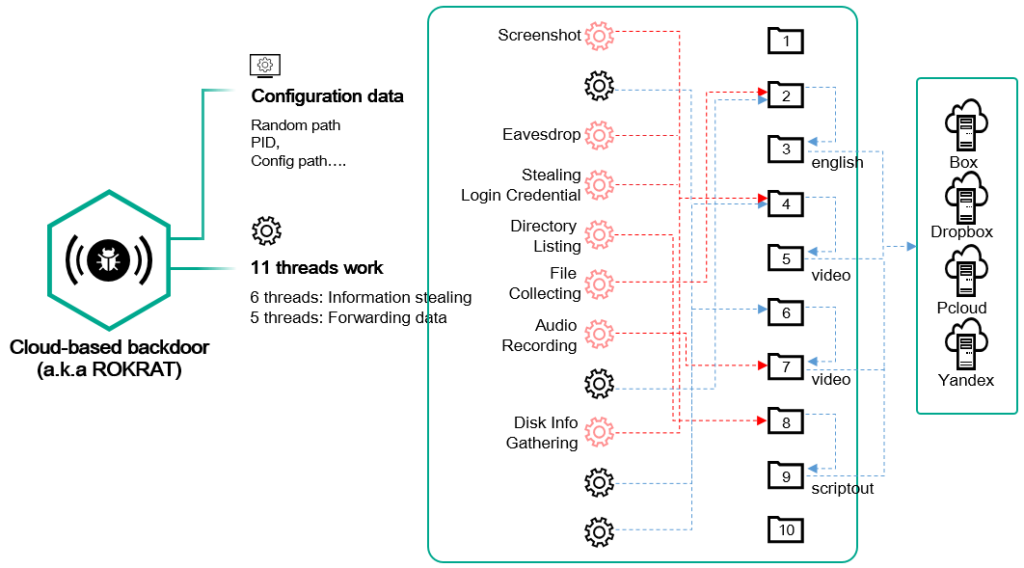
The final payload is the cloud-based backdoor known as “ROKRAT”, which is able to steal user information, forward the collected data to various cloud services (Dropbox Yandex), receive and follow additional commands, capture audio and screenshots from the infected system, and now even comes with a Bluetooth device harvester. This latest addition allows ScarCruft to command the host systems to conduct a Bluetooth device search and then send the acquired device information. The address, class, connection status, authentication status, and even the “remember device” setting are all collected and forwarded to the actors.
image source: securelist.com
By analyzing the group’s tools, the researchers have realized that their activities overlap with the DarkHotel APT group, which is North Korean. Both groups use the “GreezeBackdoor” tool and Konni malware. Kaspersky has noticed their overlapping again in the past, but also highlighted the fact that the two remain distinct, as they use different procedures and tactics. At this point, the researchers believe that ScarCruft will definitely continue to evolve, as they stay very active and seem capable of furthering and widening their data collection techniques.
Have something to say about the story? Feel free to do so in the comments down below, or on our socials, on Facebook and Twitter.