Account Takeover Attacks Found to be Evolving at a Rapid Pace
- Account takeover actors are targeting everyone nowadays, as there’s a way to make money from anything.
- The scene is proliferating, as the tools and tutorials on how to do it become more widely available.
- Users are advised to keep their data to themselves, use 2FA, and also unique and strong passwords everywhere.
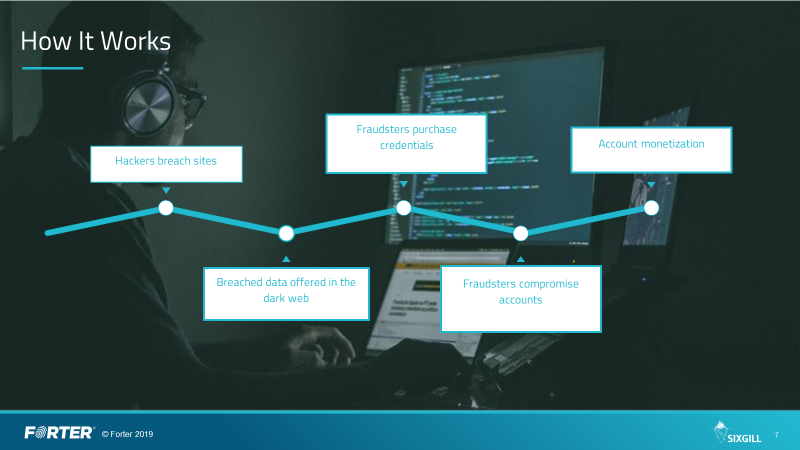
Account takeover (ATO) attacks are getting more effective and higher in number, as cybercrime actors have already figured how useful and valuable they are. Stealing one’s credentials opens multiple ways of further exploitation and monetization, while for the victims, it can be a devastating experience and a catastrophic event. SixGill dives deeper into the matter and has compiled a detailed report where the most prominent ways of ATO evolution are laid out.
Firstly, ATO actors are expanding their scope, as they are targeting a larger number of entities, both businesses and regular internet users. This expansion is made possible by the wide availability of data breach information that leaks on the dark web, as credentials stuffing is now one of the most common ways that lead to account takeover.
Source: SixGill Blog
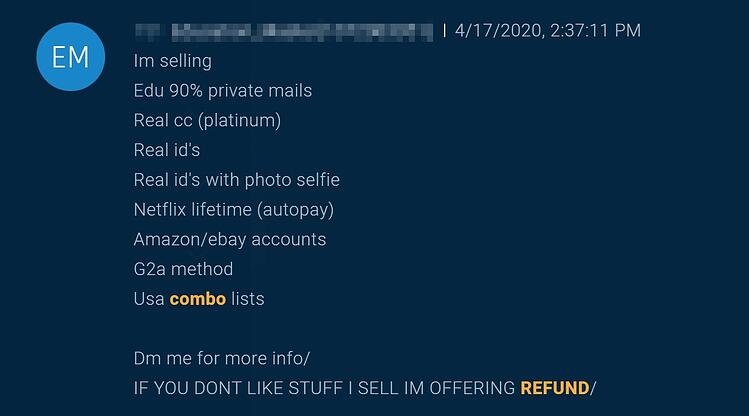
Secondly, the data that is published on the dark web is now a lot more detailed than ever before. More often than not, dumps today contain usernames, email addresses, passwords, IP addresses, billing addresses, credit card details, language, country, and even sensitive documents like passports, government IDs, and more. The fraudsters use the above to fool fingerprinting protection systems, so the account takeover attacks become easier.
Source: SixGill Blog
Then, there’s the amazing level of customer support quality that dark web marketplaces and forums offer nowadays. Even if an actor has no idea how to use ATO data and tools, they can enjoy the guidance of experienced and successful actors on how to proceed. Next, there’s the element of having large groups of actors becoming better at what they do, as fraudsters are constantly finding new ways to trick their targets, avoid detection, bypass protection systems, and avoid arousing suspicion.
Source: SixGill Blog
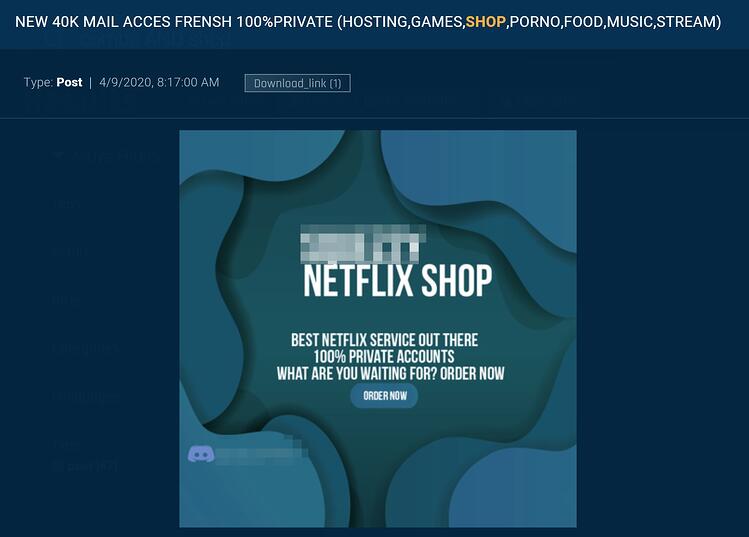
And finally, cyber-criminals are no longer interested solely in credit cards, as the full spectrum of a person’s online existence is now considered extremely precious. From Netflix credentials and Spotify accounts to air-travel loyalty club memberships and Nintendo Switch accounts, everything can be exploited. Thus, actors aren’t looking just to hastily grab what they can, but instead, they are attempting to compromise the whole online estate of their targets.
There are several things you can do to protect yourself from account takeover attacks. First, use unique and strong passwords everywhere, and never reuse the same password on two different platforms. Secondly, you should activate 2FA wherever this is possible. Thirdly, you should avoid revealing any information about yourself online, as things like your phone number, for example, can be used for SIM swapping attacks. By using anonymous email addresses, password managers, and even USB authentication solutions, you should stay safe from ATO actors who are usually after easy targets.